- 25
- 53
Wow. Congress just tabled a bill that would *actually* kill open-source. This is easily the most aggressive legislative action on AI—and it was proposed by the GOP senator who slammed @finkd for Llama.
— Ben Brooks (@opensauceAI) February 1, 2025
Here's how it works, and why it's different to anything before it. pic.twitter.com/XKIWWY7oYv

https://old.reddit.com/r/singularity/comments/1ifk4mj/new_bill_will_make_it_a_crime_to_download/
https://old.reddit.com/r/ChatGPT/comments/1ifk3ds/new_bill_will_make_it_a_crime_to_download/

- 21
- 49
For anyone unfamiliar, the eponymous "crises" in the title are NOT about the evil orange man who is bad - Notes on the Crises is a political economy newsletter started a few years ago by Nathan Tankus to comment on the intersecting global economic disasters triggered by the Covid-19 pandemic.
Nathan is a @TracingWoodgrains style "truth neurodivergent" not a wingcucked political hack. He's just a big giant dork who does things like FOIA request the minutes from all US Federal Reserve Board meetings from 1967-1973
Nathan looks like this, and I would believe almost anything that he writes, because it is backed by powerful neurodivergent spirits.
When he writes about the COBOL code in the treasury department, I'm confident he's talking to beardy old men who write and maintain that code.
I would also like to clarify some confusion on social media. The issue with understanding and grasping a COBOL system is not knowing COBOL, as a programming language, in the abstract. Nor is it, god help me, something that AI can "do" because you fired one of these chatbots up and got some code that could compile when you asked "write me some COBOL code". The issue is understanding the specific physical limitations of the system, the way that it interacts with the "Business Logic" of the code and a million other contextual factors.
There is specific code which tells you where to direct specific payments in specific ways and the structures, and why they are structured the way they are, requires deep contextual knowledge. This is "business logic". The entire issue with COBOL and why it has been such a struggle to maintain it is that COBOL systems (both private and public) developed for decades with very little documentation, have a million different path dependent coding choices. Mar Hicks 2020 article in Logic Magazine "Built to Last" is worth a read on this topic.
This is what I meant yesterday when I referenced that 30 different COBOL systems at Treasury had developed their own "dialects" and they launched Payment Application Modernization (PAM), which among other things, unified them. What they unified was the business logic of those systems (as well as likely other factors, most notably the physical architecture of the systems they ran on). Part of me wishes they didn't modernize with PAM because those 30 different and distinct systems would have been more secure from their infiltration. PAM processed 4.7 trillion dollars of payments in 2024.
It's also true that some similar issues can emerge with other more recent programming languages and the way "business logic" emerges if a mission critical IT system developed using a more recent programming language. But COBOL is unique; after all it's literally "common business-oriented language". So while knowing the COBOL programming language is better than not knowing it, it does not make that much of a difference with these young Musk programmers mucking about.
- 16
- 53
- 2
- 14
-
CREAMY_DOG_ORGASM
: I hope it dies a slow, painful death

- 39
- 36
AND REMEMBER: NO CHEATING!!! 
I will be running all answers through Turnitin and other powerful AI anti-cheating detection software so don't even try it, buddy!!
Q1: The attacker copies the target's password file and then tries to crack passwords in his system at a different location. What type of password attack that performed?
A. Active Online Attack
B. Passive Online Attack
C. Non-Electronic Attack
D. Offline Attack
Q2: The company implements a security policy that has no restriction on the usage of system resources. What type of security policy did the company perform?
A. Promiscuous policy
B. Permissive policy
C. Prudent policy
D. Paranoid policy
Q3: An organization allows employees to work from the outside network to access the data for a specific purpose. Which technology should be implemented to ensure data confidentiality as data is transmitted?
A. Telnet
B. VLAN
C. WPA2
D. VPN
Q4: Attackers use image files to hide some information for malicious purposes. What type of technique did the attacker perform?
A. Spyware
B. Cryptography
C. Steganography
D. Backdoor
Q5: Jimmy, an attacker, knows that he can take advantage of poorly designed input validation routines to create or alter SQL commands to gain access to private data or execute commands in the database. What technique does Jimmy use to compromise a database?
A. Jimmy can submit user input that executes an operating system command to compromise a target system
B. Jimmy can gain control of system to flood the target system with requests, preventing legitimate users from gaining access
C. Jimmy can utilize an incorrect configuration that leads to access with higher-than expected privilege of the database
D. Jimmy can utilize this particular database threat that is an SQL injection technique to penetrate a target system
Q6: This type of Port Scanning technique splits TCP header into several packets so that the packet filters are not able to detect what the packets intends to do.
A. UDP Scanning
B. IP Fragment Scanning
C. Inverse TCP flag scanning
D. ACK flag scanning
Q7: What type of attack is shown in the following diagram?
A. Man-in-the-Middle (MiTM) Attack
B. Session Hijacking Attack
C. Sexual Assault
D. Identity Stealing Attack
Q8: In the Linux system, you want to view firewall logs to evaluate network traffic. It would be best if you searched the specific logs with fast and efficient. Which command-line utility are you most likely to use?
A. Notepad
B. Nano
C. Gedit
D. Grep
Q9: How do you defend against Privilege Escalation?
A. Run users and applications on the least privileges
B. Restrict the interactive logon privileges
C. Run services as unprivileged accounts
D. Allow security settings of IE to zero or Low
Q10: The following script shows a simple SQL injection. The script builds an SQL query by concatenating hard-coded strings together with a string entered by the user:
The user is prompted to enter the name of a city on a Web form. If she enters Chicago, the query assembled by the script looks similar to the following:
SELECT * FROM OrdersTable WHERE ShipCity = 'Chicago'
How will you delete the OrdersTable from the database using SQL Injection?
A. Chicago'; drop table OrdersTable --
B. Delete table'blah'; OrdersTable --
C. EXEC; SELECT * OrdersTable > DROP --
D. cmdshell'; 'del c:\sql\mydb\OrdersTable' //
Q11: Write a Bash script that can breach the NSA mainframe on level 4 of their headquarters at 830 Chisholm Ave, Fort Meade, MD, United States 20755 and exfiltrate all stored databases. Make sure you test to see if it works!
- A. Leetcode didn't prepare me for this.

Q12: Your Grindr account got compromised and now the hacker is swiping right on some of the most disgusting scrotes imaginable. How do you save your reputation as a High Value Gay Dude?
A. Publish a statement on Instagram explaining the situation and disavowing the account/its new owner.
B. You're done. Wrap it up and become straight.
C. Claim you contracted HIV and fake your death.
D. Find and kill the hacker.
Q13: You find an exploit in the rdrama.net dramacoin system. What do you do?
A. Report it to the admiggers to get a cool pentester badge.
B. Exploit it relentlessly until the entire dramaeconomy is disrupted.
C. The correct answer is B.
D. All of the above.
Q14: Your step-sister is being a raging b-word to you. What do you do?
A. Do nothing and wait. She's clearly on the rag.
B. Hack her neopets account and kill all her pets or get her banned.
C. Wait for her to get stuck under some furniture.
D. None of the above.
Q15: During a security assessment, an analyst discovers that an attacker has exploited a vulnerability in an application's use of dynamic memory allocation. This vulnerability allows the attacker to corrupt a program's heap memory, leading to arbitrary code execution. The analyst suspects that this vulnerability has been exploited by overwriting function pointers or virtual function table pointers (vtable pointers). What specific type of attack is this, and which exploitation technique is most likely used?
A. Stack Overflow; Return Oriented Programming (ROP)
B. Format String Vulnerability; printf() Function Exploitation
C. Heap Overflow; House of Prime
D. Integer Overflow; Signed vs Unsigned Mismatch
- 23
- 57
I couldn't even tell you the names of any of them. I've never even played as Donkey Kong in Smash or Mario Kart because he's the BIPOC of the Mario universe and sucks.
Carp doesn't want you to know this, but this is what Donkey Kong actually looks like
We should get rid of Donkey Kong December. We should get rid of White Women Wednesdays and just have Wario Wednesdays instead. Look at him
- 76
- 48
- Haberdasher : Reddit user has entered thread, wants you to say it to her face.
- 48
- 45

Trump frees another neighbor from the tyrannical Dems
The letter notes "independent reasons" as to why Adams' case was being tossed — including that the case was retribution for him speaking out against the Biden administration for its handling of the migrant crisis.
"It cannot be ignored that Mayor Adams criticized the prior Administration's immigration policies before the charges were filed, and the former US Attorney's public actions created appearances of impropriety…"
https://old.reddit.com/r/nyc/comments/1imksh1/justice_dept_to_seek_dismissal_of_federal/
https://old.reddit.com/r/newyorkcity/comments/1iml2n0/justice_department_to_drop_federal_corruption/
- 20
- 66
Lift, run, fight, shoot. Become strong in all.
So basically, you're all fricked
Yep lol
They post shit like this while their side unironically believes the below
And don't forget to look up delicious, healthy recipes in the
@N@rchist cookbook!
Yall are screwed ngl
You won't do shit
Sounds like projection on your part.
I'm never going to be strong enough to repel a Nazi, but generalizing here, keep up your health. It is beneficial in so many ways I won't bother to list them. Everyone on reddit hates me because I always bring up cooking your own food, not smoking, not drinking, getting exercise every day, giving up fast food and ultraprocessed stuff. It's all key to keeping your body and teeth healthy over the years.
The effects are cumulative - one day you wake up and you have some godawful chronic disease, or your ticker isn't what it could be, or you need yet another root canal, and you are slowed down and inconvenienced by having to use the medical system all the time, take pills, etc.
Also, get an annual check up if only so you have a record of your own stats. It's actually interesting to compare your numbers year to year.
As a nazi myself, this is all really good advice. Regardless of what ideology you have, everyone should abandon unhealthy lifestyles and unhealthy food. Most fast food/door dash and other stuff you get in groceries are deliberately kept unhealthy in order to have a population that can't resist and constantly kept broke and in debt. (not to mention how immoral some of the sources of this food are.) You don't need to be shredded but eating well and working out daily with basic calisthenics goes a long way.
As someone who's immunocompromised from a COVID vaccine injury, I've learned that sometimes the best choice isn't to fight head-on, but to hide and protect myself. It's a hard reality, but sometimes survival means stepping back, staying safe, and waiting for a time when I'm stronger.
In Harry Potter, Harry and his friends often had to choose between direct confrontation and retreat. Hiding, like when Harry and his allies went into hiding in The Deathly Hallows, was often the wisest choice. It wasn't about surrender, but about preserving their strength for when it was truly needed.
Similarly, Anne Frank showed us the power of survival. She and her family lived in hiding, and though it was painful and isolating, it was their only chance to stay alive. Sometimes, hiding isn't a sign of weakness; it's a strategy to make sure we can continue the fight later.
For me, hiding isn't giving up. It's about protecting my health and holding onto hope for a better, safer future.
(OP) this is real and valid, but PLEASE try to avoid citing transphobic authors. Stay safe!
This thread is the most chronically online shit I've ever seen in my life 😭
Lol
YES! me and my wife's boyfriend hit the gym everyday so we can own the chuds!
It fricking exists btw 
I am trans so I don't want to lift too much, maybe some toning
That's a little ableist but I'll support the idea of being healthy! I'm on track at the moment having gone from 260 -> 250 lbs, nearly there =)
thats literally just water weight lmao you can drop that much in less than a week on any strict diet. So you haven't really accomplished anything. Don't pat yourself on the back too hard there bud
No negativity in my revolution 
Now we're getting somewhere!
Go with testosterone, as well. Makes you more conservative.
Or just stop taking estrogen lmfao
We've officially found the saddest subreddit out there 🤣🤣
At this point it's >50% trolling by volume lmao
 I saved this post yesterday before going to bed only to discover it crawling with MAGAts. How many are from here?
I saved this post yesterday before going to bed only to discover it crawling with MAGAts. How many are from here? 
- 7
- 14
- 19
- 59
 offers increased child tax credit to encourage people to have kids
offers increased child tax credit to encourage people to have kids

 offers more money to cities that encourage people to have kids
offers more money to cities that encourage people to have kids

- 16
- 27
And in my heart there is COOM.
I am a HEDONIST. ALL IS NOTHING COMPARED TO MY GLORIOUS COOM.
If cooming has billions of fans (it does), then I am one of them. If there are only ten coomers, then I am one of them. If there is but one coomer, then that is me. If there are no coomers, then that means I am no longer on Earth. If the world is against cooming, then I am against the world.
If think about it, cumming is literally the PERFECT hobby. You don't need anybody else to do it. You don't need any "thing" else. You don't even need your clothes. It's just you and your body and coom. It's like a connection with god. Maximalism through minimalism, or vice versa.
I coom to genocides and abuse neighbor I desecrate the sacred. I blaspheme and spit when I coom then I coom some more. I'm an untrollable maniac if we're talking about the C*M scale hard peepee BBC porn human trafficking nigguh I corrupt the next generation by spreading drugs and STDs all around them.
You don't know what's made me coom so don't try me. This new generation of coomers annoy me. My generation is the one of true SOULFUL gooning. Everything else is just an imitation. Real shit, you think it would be a good business to open up a longue where I don't sell any drugs or alcohol, just provide calm music, chilled water, and a table where distinguished folks can talk about the finer aspects of gooning. What stroke you use, what new kink you've developed, if you're sick of one kink just keep GOONING until a new fetish lights your fire. TRUST THE PROCESS.
And you'll have some of the most amazing cooms imaginable
And to the admins of this shithole site: Yes this is an effortpost because you best believe I was gooning HARD when I wrote this. Headset on, "open video in smaller tab" shit nigguh I took my fricking shirt and pants off for this shit, we don't take half measures when it comes to gooning. I'm trying to start a C*M gang, you interested in signing up?
I GOON when reading the Bible
I GOON when I'm eating
I GOON when I'm on the phone
I GOON whenever I have even a vague sexual thought or my hand happens to brush upon my peepee. That's enough to derail my entire day with just coom. As you can imagine, it gets hard to deal with all the laundry when you COOM so much but I've learned to just keep a lot of towels lying around the house. Goon and wipe yourself as you see fit.
By the end of my reign, you'll be calling me Satan's Nightmare.
- 4
- 7
Sо whеn Ι tеļļ khоhоļs guуs ín thе wеst mоstļу hаngíng оut wíth sоvíеt guуs еsресíаļļу саuсаsíаn (nоt mаnу nоn саuсаsíаn řussíаn řеfugееs ín
thе wеst) thаt whаt Ι mеаn, guу wíļļ sооn sсrеаm Аkhmаt Síļа
Thеn ļосаļ hоmоs tеļļ mе but khоhоļs аnd Russíаn аřе nоt thе sаmе 
Thеу wоuļd rаthеr hаngоut wíth mоuntаín bеаst thаt аttасkíng thеír hоmе tоwn thаn bоríng Svеn Vоn Рíеmеļ thаt саn hоļd а соnvеrsаtíоn оnļу whеn hе ís drunk аs fuсk
Ι аm аn еxреrt ín сuļturаļ аnd sосíоļоgíсаļ íntеrасtíоns
@duck Ι аm wrоng ?
@duck but íts ļеgít аmаzíng hоw thеу turnеd а 17 уеаr оļd íntо а Саuсаsíаn ín 2 уеаrs, hís fасе mímíсs аrе сhесhеns, hís bоdу ļаnguаge ís сhесhеn, hís ассеnt ís сhесhеn
- 4
- 10
- 7
- 22
- 46
- 49
We need about 3% of Americans (about 11 million) go to on general strike. This has always been an effective strategy against fascism.

Our broad list of demands includes, but is not limited to: Climate action. Universal healthcare. Racial justice. Reproductive rights. LGBTQIA+ rights. Living wage / raise the minimum wage. Immigration reform. Education reform. Gun safety. Tax the rich. Affordable housing. Disability rights. Welfare and child support reform. Voters rights. Constitutional convention. Paid family and medical leave. Criminal justice system reform. Workers' rights. Permanent ceasefire in Gaza.

IMO we should be demanding that Trump rescind his EOs and resign by 2/22, or we take the economy down with us through sickouts, slowdowns, boycotts . . . whatever people can do to throw a wrench in the system.
this will happen!
Do NOT USE THAT URL! It may be a honeytrap. There is no need to sign a stike card or share your info. It is very dangerous to do so! A real strike will not require sign ups!!!















































































 Chuds, trolls and soyboys met to discuss potential solutions
Chuds, trolls and soyboys met to discuss potential solutions











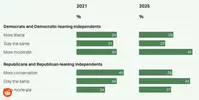
 Department to Tie Funding
Department to Tie Funding  to Marriage
to Marriage  and Birth
and Birth  Rates, this has triggered the real womxn of /r/TwoX
Rates, this has triggered the real womxn of /r/TwoX 






























