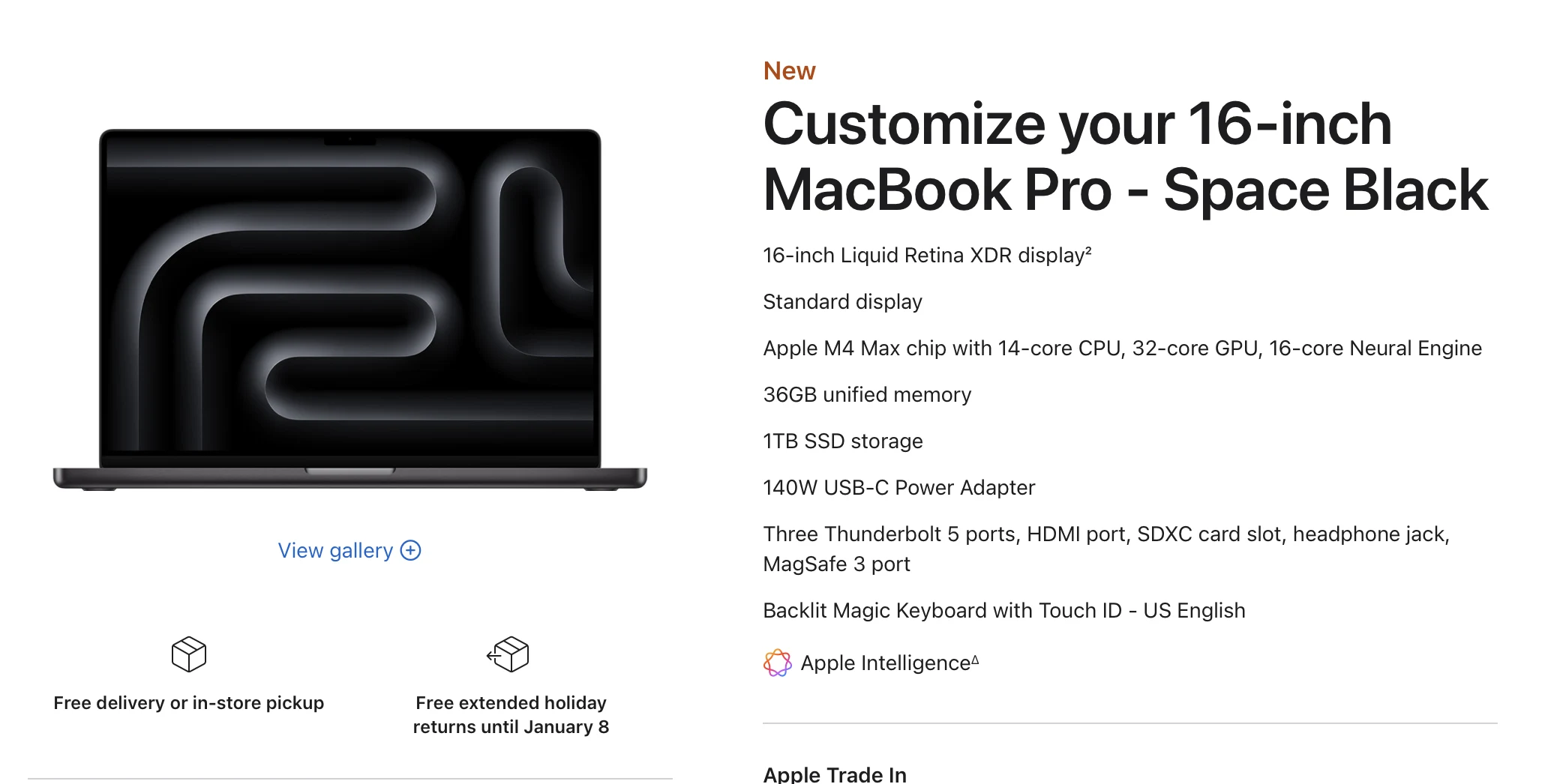
I was debating going with a 16in M4 Pro vs a 14in M4 Max, and really wanted the larger screen size but thought I'd regret not having the better processor and graphics. Well Best Buy had the 16in with the specs of the 14in for $400 off, which makes it cheaper than either previous choice. The only thing I'm down is 12gigs of ram (48 vs 36) but I feel like 36 is a lot already. My current computer has like 8 gigs lol.
Now I'm just waiting for the order to show up confirmed on Best Buy's website and to get a confirmation email. It shows that it's already charged my card, and it's driving me nuts! They only have two in stock so I'm sweating.
My next update will hopefully be brought to you by the blazing fast performance of the M4 Max. I can finally turn off poor mode!








Jump in the discussion.
No email address required.
Buy a thinkpad x230 and install heads. Write protect the flash chip. Put nail polish on the screws and take high resolution pictures to ensure signs of tampering. Do NOT use a HDD or SSD. They have DMA so a malicious firmware could do a lot of damage, use of USB is preferred since they do not have DMA. Completely remove the microphone, sound card, webcam and the WWAN card from the laptop. Remove the fan to prevent binary acoustic data transmission. Replace the default wifi card with a supported atheros card. Disable wifi when not in use, preferably by physically removing the card. Make your own independent Linux distro from scratch. Most Linux distros value convenience over security and will thus never have good security. Your only option is to make your own. Use musl instead of glibc, Libressl instead of openssl, sinit instead of systemd, oksh instead of bash, toybox instead of gnu coreutils to reduce attack surface. Enable as little kernel modules as possible. Use a hardened memory allocator. Apply strong SELinux and sandboxing policies. Restrict the root account heavily to make sure it never gets compromised. Disable JavaScript and CSS in your browser. Block all STRAGMAN domains in your hosts file. Monitor all network requests. Do not use a phone. Never speak near anyone who owns a phone, they are always listening. Never use any non-corebooted technology made after 2006. Never leave your devices unattended. Tape triple layer aluminum foil all around your room as tempest shielding. Type really quietly as defense against audio keylogging. Use ecc ram to minimize rowhammer and rambleed. Encrypt everything multiple times with various different encryption implementations. Compile everything from source. Use hardened compilation flags. Always read through the source before installing something if possible. Only use the internet when absolutely necessary.
Jump in the discussion.
No email address required.
More options
Context