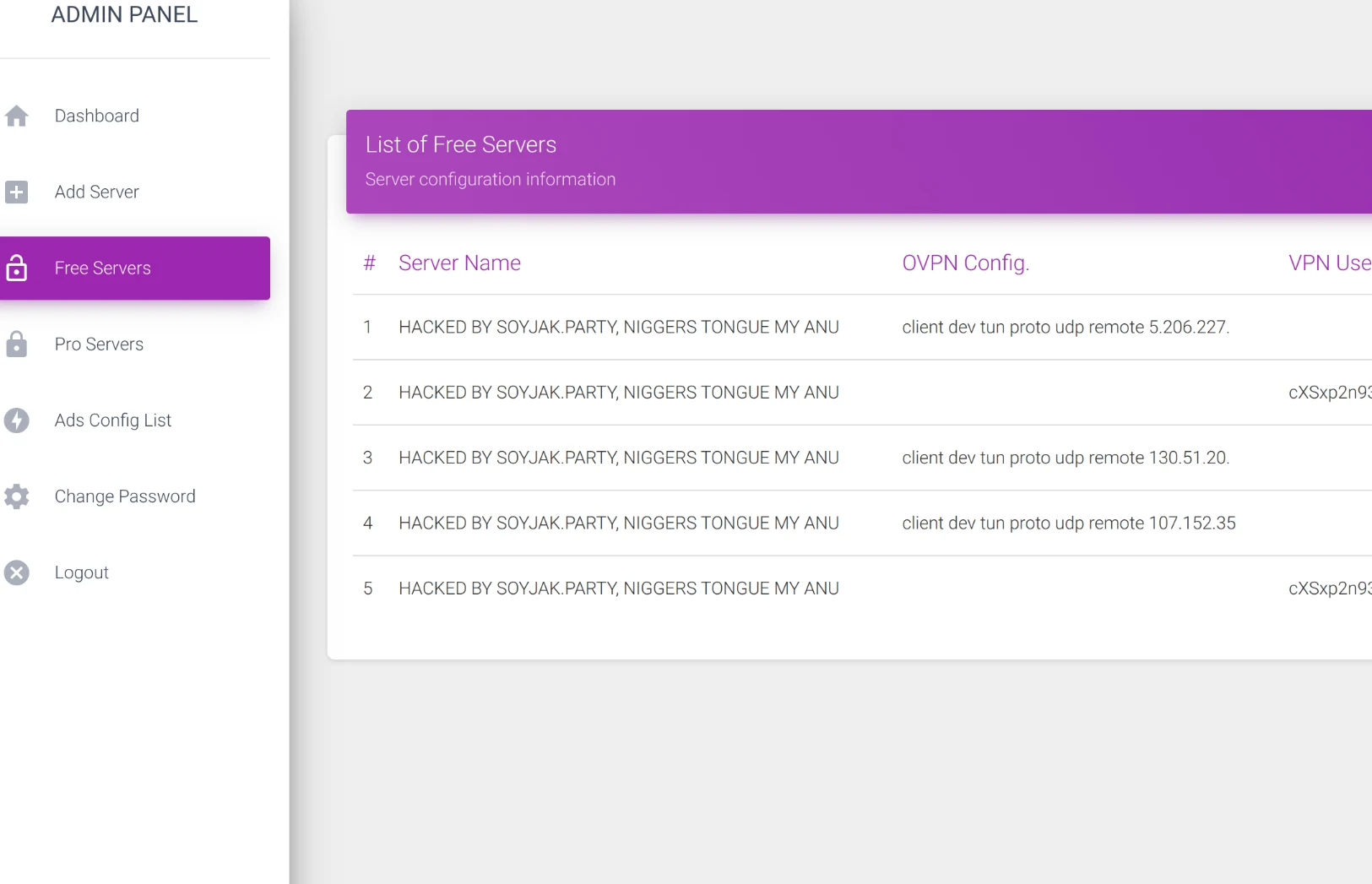
I setup 16 OpenVPN servers
No you didn't, you're using Surfshark's servers.
t. VPN Fren
This shit glows.
Also nice security, cute twink. Parameterise your SQL queries.
fricking L M A O 
thread: https://archived.moe/g/thread/95091081
EDIT:  deleted thread xd, desuarchive: https://archived.moe/g/thread/95091081
deleted thread xd, desuarchive: https://archived.moe/g/thread/95091081
!codecels a lesson you must learn, but dont learn it like this r-slur





.webp?x=8)
 (probably a
(probably a  ) makes 'TempleVPN', sets up ad for it on /g/, is instantly mogged by a 'teen because dipshit didnt sanitize inputs
) makes 'TempleVPN', sets up ad for it on /g/, is instantly mogged by a 'teen because dipshit didnt sanitize inputs






Jump in the discussion.
No email address required.
How is this still a thing in Current Year?
Jump in the discussion.
No email address required.
If he hired sexy Indian dudes to code for him, I'm not surprised. Or maybe he hired Null.
Jump in the discussion.
No email address required.
More options
Context
Watch CIA recruiting media to understand how shit like this happens.
Jump in the discussion.
No email address required.
How's your daughter
Jump in the discussion.
No email address required.
Still refuses to change in front of me after i got drunk and bragged about how hot my daughter was to fricking my friends. Kids these days.
Jump in the discussion.
No email address required.
More options
Context
More options
Context
More options
Context
Diversity hires
Jump in the discussion.
No email address required.
More options
Context
cashgrab and/or r-slur
Jump in the discussion.
No email address required.
More options
Context
For real, neighbor should've rerouted the auxiliary encryption to the dedicated network processor first and foremost lmao
Jump in the discussion.
No email address required.
Jump in the discussion.
No email address required.
More options
Context
More options
Context
I'm not a codecel, what does this actually mean?
Jump in the discussion.
No email address required.
Basically a SQL query gets (or puts) data from your database.
A query might look like
SELECT FIRSTNAME FROM USERS WHERE USERNAME = 'drumpf'
If you take data from a user (like in a username field on a page) and pass it straight over to the database a malicious user might be able to frick up your database. In my above example 'drumpf' would be ok. But if I instead said my username was drumpf'; drop table users; I could chain multiple commands together and cause trouble.
Parameterizing queries prevents that and is so elementary that it's shocking to see people neglect to do it. Basically it would prevent me from chaining the above commands and treat the whole thing as my username, which wouldn't find any matches but it wouldn't break anything either.
Jump in the discussion.
No email address required.
More options
Context
Databases use Structured Query Language which is text to do things like look up values. You write out what you want to happen. Quite often you're taking user's input and using it in your searches. But critically bear in mind that it is, at the end of the day, a big line of text. When dealing with inputs, there are two ways of doing things:
You build up a string of what you want to run on the database filling in the inputs as you go
You use a sort-of "template" and pass the template and the inputs in separately.
The problem with (1) is that you're not in control of what's inside the input, I am. So instead the username "bob" that the programmer expected, it is "bob';" and that extra quote-semicolon tells the database that the query is finished. You then tack on whatever you want and it'll be run. So things like "add GenocideMaxxer to the list of people who can log in to the management console" are popular to use. You then finish off by adding "--" and those two dashes tell the database to ignore the rest of what was sent. For example "find users called 'bob' whose id is 123" becomes "find users called 'bob' and then also do this thing"
The second method is method superficially similar but critically different in the way that inputs are used. You pass "find all the users called $1 whose id is $2" and then you pass that along with the inputs separately. The way that the query parser/planner operates means that by the time the parameters are read then the database request isn't a string that can be injected in to at that point, it's been broken down in to bits and the values/inputs that I enter can't be used for anything other than being a value/input in the process.
The vulnerability expressed in the former case is notorious and has been widely exploited since the late 90s when the Interwebs were taking off. You can more about it here, but that's the gist of it. https://en.wikipedia.org/wiki/SQL_injection#Incorrectly_constructed_SQL_statements
Jump in the discussion.
No email address required.
More options
Context
More options
Context
More options
Context