It's full of quality code like this.
The lead software tester was a daughter of another friend with whopping 2 years of experience (and a non-stem degree).
They didn't have 2fa for anything, they got access to one of the developers outlook email+password through social engineering and got access to EVERYTHING.
the whole sourcecode: t.me/sawarim
I want to thank your countrymen for paying for this @UraniumDonGER



.webp?h=10)
 Lois, democracy and liberalism is non-negotiable
Lois, democracy and liberalism is non-negotiable





Jump in the discussion.
No email address required.
Oh wow coders quick get in on this! Here's a chance to tell everyone that you're a coder and could do better than this or relate it to some shitty experience from your own life!
Fricking wow. Big deal. You know how to defensively build apps to avoid sql injection but are you getting paid by government money to not do that? Ha. Thought not. So who's really the stupid one?
Jump in the discussion.
No email address required.
I'm sitting here staring at it thinking "what's the big deal? Looks like a pretty good input sanitization function to me ".
".
Jump in the discussion.
No email address required.
Rolling your own function to do this is a bad idea (biggest issue)
Runtime efficiency sucks
Code is not very maintainable (minor concern, however the code is overall rather amateurish)
There would be no better time to use a REGEX. The entire method could be reduced to two lines, and would be faster.
Jump in the discussion.
No email address required.
just charge more to make it lmao
charge more to run it
charge more to maintain it
sound like wins to me.
2. has the bonus that you can shave off some of the time later if they come to you asking you to make it faster. It's perfect.
Jump in the discussion.
No email address required.
remember put Thread.Sleep randomly in your code so you can just
so you can just  remove it and give
remove it and give  multisecond performance boosts
multisecond performance boosts
Jump in the discussion.
No email address required.
More options
Context
More options
Context
I'd rather have a few more lines of readable code, than a regex that is a pain in the butt to look at.
Jump in the discussion.
No email address required.
More options
Context
Eh, not really. The .NET CLR optimizes this kind of stuff away.
Jump in the discussion.
No email address required.
More options
Context
More options
Context
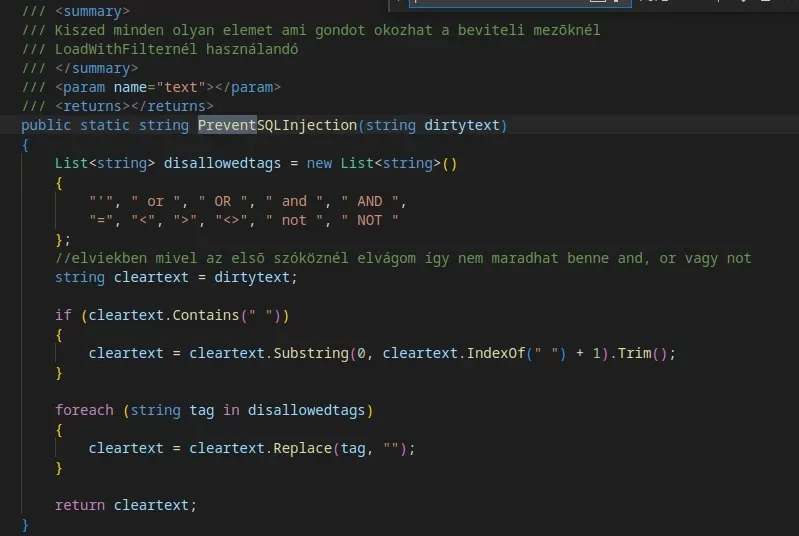
It is pretty nonsensical. First it looks for the first " " in the string, and then removes everything after that space. e.g. "testtest testetste" would get turned into "testtest ". then they trim it to "testtest". If they had just removed the +1, they wouldn't have to trim it.
So this function by defaults rejects anything beyond the first space, which is most likely not what would expect from a function called "PreventSQLInjection".
Now because of that it is literally impossible the string would ever contain stuff like " or ", which works in their favor, because they are not even checking for case sensitivity. However you could just use non space whitespace, like \n or \t and it would still work. So so far this hasn't actually done anything.
Then replacing " or " with nothing, is actually a pretty horrible way to handle it, because " o or r " would just get turned into " or ", but again thats irrelevant because it is impossible for there to be a space to begin with.
Then there might be some unicode character that is seen as a ' by the database, but not as a ' by c#
Jump in the discussion.
No email address required.
There really is a lot of layers to the crappiness of this code, lol. The more I look at it the more I can find.
I thought that was a double space, rofl. What were they even trying to do with that?
Jump in the discussion.
No email address required.
More options
Context
More options
Context
They're missing UNION, which is pretty common in SQL injection attacks. There are probably others missing, too.
Jump in the discussion.
No email address required.
Sure, and they only have AND and and, not AnD or aNd. But that shouldn't matter if everything is quoted, no?
Jump in the discussion.
No email address required.
Lol, I didn't even think of those. This is also another bad code example. The String.Replace() method has a way to toggle case sensitivity, iirc.
IF the output has been single-quoted within the code invoking the method. Any dev using this method that forgets to do so has potentially created another vulnerability. From a design standpoint, it's bad (IMO) because it splits the responsibility of security between this method and the dev invoking it. If the dev invoking it had instead just used SqlCommand, it would not only be secure but also involve less code overall. Apparently there's some other shit you can do, too.
All in all, it's a very bad idea to try to scratch-build security if reliable solutions already exist (i.e. not some homebrew solution on a personal GitHub repo).
Jump in the discussion.
No email address required.
The alternative method assumes you replace
'with''. The OP code just erases it.Jump in the discussion.
No email address required.
There's a few extra methods described in there but I only scanned the page before pasting the link. I see that one answer talked about "SQL smuggling" involving screwing with Unicode translation, which I wouldn't have considered without looking this up. However, it looks like using String.Replace() might take care of that, according to the answer.
Jump in the discussion.
No email address required.
More options
Context
More options
Context
Don’t even need to do worry about sensitivity if you just use .toLowerCase(name). So anything put in that input line is always lowercase when being passed in. If you need the first character to be uppercase for output you can format later.
Also Java should have a built in anti sql injection function, like there’s built in hashing in pretty much every backend usable language now, or just regex it yourself.
Jump in the discussion.
No email address required.
I actually said the same thing in my comment at first but I went back and changed it b/c the method returns the altered user input, which means lowercasing or uppercasing it could return the user input with alterations not intended for sanitation.
Jump in the discussion.
No email address required.
More options
Context
More options
Context
More options
Context
Funnily enough all those cases are covered because before searching for disallowed tags they truncate the text to only stuff before the first space (and including that first space for some unfathomable reason) so you're never gonna match " AND " because it literally starts with a space, it's just an extra run through the string at that point that takes up time and does nothing else.
Jump in the discussion.
No email address required.
More options
Context
More options
Context
More options
Context
More options
Context
Literally every thread on drama about coding. Me thinks coders only appear competent when commenting on other people's code but the moment they actually have to do any work themselves they all reveal themselves to be drooling r-slurs (except for our lovely admin codecels ofc )
)
Jump in the discussion.
No email address required.
Nitpicking code mistakes from the sidelines without context and smugly responding with handwavey "solutions" is one of the basic requirements for being a developer.
Jump in the discussion.
No email address required.
You don’t need context to recognize r-slur code.
Jump in the discussion.
No email address required.
More options
Context
More options
Context
More options
Context
No need to be jealous that some RDramatards have a useful skillset.
Jump in the discussion.
No email address required.
More options
Context
More options
Context