- 3
- 14
thanks to some sql help from intrepid data scientist @LucasWerkmeistr, i have compiled a list of the 206 articles in english wikipedia with the suffix -ussy. here's a threadussy of a few of them pic.twitter.com/VctAF5dZLJ
— depths of wikipedia (@depthsofwiki) September 28, 2022
- 42
- 112
Never thought I find my hidden niche.
— Coco 🥜 (✦Commission(Closed)✦) (@setawar) September 26, 2022
A High Quality Victorian Era Painting of A Lady With Large Breast pic.twitter.com/k0sh0cdRCx
Frick it this goes in slackernews
I love my ai overlords
- 3
- 9
Your "Too long, didn't click"
In your “Content you see” settings, you can now choose to show, blur, or hide content that depicts the following topics:
Drug and alcohol addiction: Contains discussions of substance abuse or addiction experience.
Violence: Contains violent or graphic content similar to what you might see in an age-restricted movie.
Sexual themes: Contains sexually suggestive subject matter, such as erotic writing or imagery.
Some examples of content that would require a community label:
Fanart of your favorite ship engaging with each other in...a very private moment
Euphoria GIFs showing Rue’s substance abuse
A movie trailer depicting graphic war scenes
A graphic 50 Shades of Grey edit
- 69
- 78
It's close to the end of the year, you know what that means! More expensive shit that holds little to no tangible benefit compared to the expensive shit that came out last year!!! The current focus is on CPUs and boy oh boy this is one of the product launches ever.
To start off with, AMD's new zen 4 processors operate at 95°c regardless of how beefy your cooling solution is. This is by design, apparently.
AMD went on to say that 95C is not running hot, rather Zen 4 will intentionally go to this temperature as much as possible under load because the power management system knows that this is the ideal way to squeeze the most performance out of the chip without damaging it.
Good stuff.
Additionally, the big expensive ryzen 9 7950x only barely outpaces the significantly older ryzen 7 5800x3D which is really really funny.
Intel has also recently decided to make it known that they exist too, announcing their new line of "raptor lake" processors. The graphs speak for themselves.
In the midst all of this, many are still waiting for somebody to announce a product that isn't completely pointless.
- 12
- 31
Reminder: Absolutely NO anti-CCP sentiment

https://old.reddit.com/r/technology/comments/xpqpu7/facebook_busts_chinese_influence_network/
https://old.reddit.com/r/China/comments/xpqflu/facebook_busts_chinese_influence_network/
https://old.reddit.com/r/technology/comments/xpsf3c/meta_disrupted_chinabased_propaganda_machine/
Generated from TLDR This:
Credit: CC0 Public Domain Meta removed a Chinese influence network that attempted to inflame political tensions on Facebook, Instagram and Twitter ahead of the midterm elections.
Ben Nimmo, global threat intelligence lead for Meta, says the activity marked a shift for Chinese influence operations which typically seek to shape public opinion abroad by pushing pro-China propaganda and attacking the United States.
The influence operation targeted primarily the United States and the Czech Republic.
"I don't think China is trying to change the outcome of various issue-oriented political dialogs in the United States or trying to change the outcomes of specific elections," he said. "
Fewer than 10 accounts followed one or more of the Instagram accounts, according to Meta.
Meta said it removed all of them for violating its policies against "coordinated inauthentic behavior
- 8
- 20
- 4
- 7
Generated from TLDR This:
Where is the heart of the technology industry?
The simple answer is “Silicon Valley,” a term that now generally means the San Francisco-San Jose-Oakland area of California.
The Exchange explores startups, markets and money.
To answer that question, we have to understand how Silicon Valley compares to the larger United States venture capital and startup market; if Silicon Valley is truly losing its dominance domestically, it certainly cannot claim an international title.
https://t.co/5UabCGkHqb — Chamath Palihapitiya (@chamath) September 26, 2022 In time, I do anticipate that a more global tech industry will dilute Silicon Valley’s former hegemony as the spawning point for what’s next, and it will become more figurehead than anything else.
- 5
- 21
If only Tether finally collapsed. It would be good for bitcoin and crypto.
Generated from TLDR This:
The U.S. Securities and Exchange Commission has fined Tether’s former auditing firm, Friedman LLP, to the tune of $1.5 million, according to an order issued Friday.
The regulator found the accounting firm engaged in several instances of “improper professional conduct” in its audits of two companies from 2017 to 2020.
While the order doesn’t mention Tether outright, the stablecoin issuer retained Friedman LLP as auditor from May 2017 to January 2018 before ending the relationship.
Tether’s dollar backing Tether’s financial activities have been under probe for some time, driven in part by the company’s insistence that the composition of its reserves is commercially sensitive in such a competitive market.
Tether and Friedman LLP have not responded to requests for comment at the time of publishing.
- 31
- 67


Generated from TLDR This:
It’s been a little while since we had a high-profile media feed hijacking, but tonight someone sent an Apple News notification from Fast Company containing a racial slur and invitation for a particular sexual act.
Apple has addressed the incident on its Apple News Twitter account, saying that it’s disabled Fast Company’s channel.
Two obscene and racist push notifications were sent about a minute apart.
The messages are vile and are not in line with the content of Fast Company.
Message posted by Fast Company hackers Image: FastCompany.com The hackers also pointed to a forum for trading information stolen in security breaches, where they shared the same details, starting with posts made two days ago.
Vox Media staffers who don’t pay for subscriptions to Fast Company say it popped up on their phones as well.
- 6
- 18
Imagine that you get a police sketch, and then ask a talented artist to make a high-quality photorealistic rendition of that police sketch. That's how this is "decompressing" the "compressed" images, with all the chances for failure and individual touches that brings 
Can't wait until my family photos get chewed up and then "decompressed" by a DEI-approved LGBTAI that turns my grandma into a black transvestite
- 5
- 16
most dramatic subthread where someone's code gets insulted: https://news.ycombinator.com/item?id=13316207
this guy arguing still: https://news.ycombinator.com/item?id=13316170
etc
- 25
- 42
Great to see /r/programming giving valuable input on this, these comments are so high quality!
What is it about Rust that causes commenters in the subreddit to turn their brain off?
When you use Rust, it implies that you do not trust programmers to handle memory safety correctly.. I guess for some people that comes across as a personal attack.

There is a weird pattern in lots of domains where people see things like this as a threat or a comment on themselves. You get the same weird response in completely unrelated things like games losing console exclusivity. For somebody who is a C programmer, Rust in the Linux kernel is a very strong signal that Rust is growing and C is losing its exclusiveness in these spaces. It probably doesn't help that Linus famously hates C++ and his resistance to C++ in the kernel has been a major point of pride for the "C is awesome" crowd.

What is it about Rust that causes commenters in the subreddit to turn their brain off?
So because Rust doesn't get unanimous praise it means other programmers are brain dead?

It's a terrible language designed for people who aren't confident in their code.
downmarseyd threads:
- 26
- 86
- 36
- 71

https://old.reddit.com/r/PoliticalHumor/comments/xmgy7l/were_messing_with_texas/
https://old.reddit.com/r/BlatantConservative/comments/xnd3yr/rdramanet_can_suck_my_peepee/

https://rdrama.net/post/107591/ublatantconservative-cucks-out-plans-on-ending
https://rdrama.net/post/107616/-
https://rdrama.net/post/107968/twitter-bluecheck-techdirt-journaloid-covers-political
https://rdrama.net/post/107406/you-are-one-of-the-good

https://x.com/jimmy_wales/status/1573604989255155712
https://nitter.42l.fr/mmasnick/status/1574481534110732288
https://nitter.42l.fr/BlatBlat16/status/1574516847403143168
Generated by TLDR This:
Subreddit Discriminates Against Anyone Who Doesn’t Call Texas Governor Greg Abbott ‘A Little Piss Baby’ To Highlight Absurdity Of Content Moderation Law from the greg-abbott-is-a-little-piss-baby dept Last year, I tried to create a “test suite” of websites that any new internet regulation ought to be “tested” against.
Last week, we called out that Texas’s HB 20 social media content moderation law almost certainly applies to sites like Wikipedia and Reddit, yet I couldn’t see any fathomable way in which those sites could comply, given that so much of the moderation on each is driven by users rather than the company.
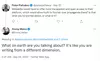
To which a reasonably perplexed Wikipedia founder Jimmy Wales rightly responds: What on earth are you talking about?
It’s like you are writing from a different dimension.
Just this week, an appeals court reinstated the law after a different court had declared it unconstitutional.
Partially to raise awareness of the bullshit of it all, but mainly because we find it funny.
- 54
- 49
Disgusting sexist pigs.

https://old.reddit.com/r/news/comments/xoqwat/pennsylvania_school_district_bans_girls_who_code/
https://old.reddit.com/r/politics/comments/xorcak/pennsylvania_school_district_bans_girls_who_code/
Generated from TLDR This:
A school district in Pennsylvania has banned the Girls Who Code book series for young readers, according to an index of banned books compiled by the free expression non-profit Pen America.
The Girls Who Code series features a group of girls who become friends in their school’s coding club.
Saujani said that the group Moms for Liberty, a conservative non-profit formed in 2021 that has been pushing book bans through local chapters across the country, was responsible for the Central York district’s ban on the series.
According to Pen America’s banned books report, many of the titles being banned deal with LGBTQ+ themes or have non-white characters.
An author of one of the Girls Who Code books, Jo Whittemore, said on Twitter: “Some people choose not to focus on how awesome and empowering and inspiring these books are but instead choose fear.”
- 1
- 8
- 7
- 10
Generated from TLDR This:
The humble cell phone is now a critical tool in the modern workplace; even more so as the modern workplace has shifted out of the office.
Last month, Cloudflare was one of 130 companies that were targeted by a sophisticated phishing attack.
And this is how we think about Zero Trust SIM: another layer of defense at a different level of the stack, making life even harder for those who are trying to penetrate your organization.
By integrating Cloudflare’s security capabilities at the SIM-level, teams can better secure their fleets of mobile devices, especially in a world where BYOD is the norm and no longer the exception.
In fact, under the covers, we’re using the same software networking foundations that our customers use to build out the connectivity layer behind the Zero Trust SIM.
We know that whilst security is critical, security that is hard to deploy tends to be deployed haphazardly, ad-hoc, and often, not at all.
- 49
- 61
Tldr ssns suck, if you know someone's birthday and place of birth they're super easy to guess.
Social Security numbers (SSNs) may not be as random as believed, as a new study contends that powerful mathematical techniques combined with open-source research can, in some cases, reveal a person's secret number.
The study, published on Monday in the journal Proceedings of the National Academy of Sciences, serves as a stark warning that SSNs are increasingly vulnerable, putting more people at risk of identity theft.
"Unless mitigating strategies are implemented, the predictability of SSNs exposes them to risks of identity theft on mass scales," the study said.
The study comes from Carnegie Mellon University's Alessandro Acquisti, an assistant professor of information technology and public policy, and Ralph Gross, a postdoctoral researcher.
The Social Security Administration responded on Tuesday, saying the public should not be alarmed since there is no foolproof method for predicting an SSN. However, the agency said it is developing a new system to randomly assign SSNs that will be in place next year, although those efforts are unrelated to the study.
"The method by which Social Security assigns numbers has been a matter of public record for years," the statement said. "The suggestion that Mr. Acquisti has cracked a code for predicting an SSN is a dramatic exaggeration."
Gross and Acquisti developed an algorithm that analyzed data from the Social Security Administration's Death Master File, a public database of some 65 million Americans who have died and their SSNs, which is used for antifraud purposes.
They looked for numerical patterns in the deceased's SSNs, drawing correlations between where a person was born and their birth date and how that data relates to their SSN.
"Our prediction algorithm exploits the observation that individuals with close birth dates and identical state of SSN assignment are likely to share similar SSNs," they wrote.
The first three digits of an SSN is an area number, which is based on the Zip code of the mailing address provided when a card was applied for. The next two digits is a group number, which assigned in a "precise but nonconsecutive order between one and 99." The last four digits is a serial number.
The algorithm, which the authors did not detail, successfully ascertained the first five digits for 44% of the records in the Death Master File for people born between 1989 to 2003. The complete SSN could be picked out for 8.5% of those people in under 1,000 attempts. For people born between 1973 and 1988, the algorithm could predict the first five digits for 7% of those in the Death Master File.
"SSNs were designed as identifiers at a time when personal computers and identity theft were unthinkable," the study said.
Other changes in how the Social Security Administration assigns numbers have made guessing even easier. In 1989, the agency stated a program called Enumeration at Birth, assigning SSNs to newborns as part of the birth certification process.
The changes, however, increased the correlation between a person's birth date and all nine digits of a SSN, especially for people in less populated states, making SSNs easier to discover, the researchers wrote.
Additionally, the proliferation of information on social-networking profiles, such as a person's hometown and birth date, puts people at greater risk, since that information could be used to infer SSNs.
"Such findings highlight the hidden privacy costs of widespread information dissemination and the complex interactions among multiple data sources in modern information economies," the researchers wrote.
Attackers could then take the SSNs they think are accurate and run them through credit approval services. Even though many of those services will limit the number of attempts to verify data, botnets could be employed to test vast numbers of SSNs to ensure they're valid, they wrote.
The Social Security Administration also said that it has cautioned the private sector against using SSNs as a personal identifier
https://www.pnas.org/doi/10.1073/pnas.0904891106
Paper abstract:
Information about an individual's place and date of birth can be exploited to predict his or her Social Security number (SSN). Using only publicly available information, we observed a correlation between individuals' SSNs and their birth data and found that for younger cohorts the correlation allows statistical inference of private SSNs. The inferences are made possible by the public availability of the Social Security Administration's Death Master File and the widespread accessibility of personal information from multiple sources, such as data brokers or profiles on social networking sites. Our results highlight the unexpected privacy consequences of the complex interactions among multiple data sources in modern information economies and quantify privacy risks associated with information revelation in public forums.
PDF:
https://www.pnas.org/doi/pdf/10.1073/pnas.0904891106?download=true
Research website:
https://www.heinz.cmu.edu/~acquisti/ssnstudy/
Q. What exactly does it mean that SSNs are "predictable"?
It means that information about an individual's state and date of birth can be sufficient to statistically infer narrow ranges of values wherein that individual's SSN is likely to fall.
"Can,'' because this is true (in general, and simplifying things a bit) only for individuals who received their SSN around the time of their birth (by 2005, at least 92 percent of SSNs assigned to US citizens were assigned at birth [SSA, 2006]; the percentages of individuals receiving their SSNs around the time of their birth started increasing dramatically in the late 1980s as a result of the Enumeration at Birth initiative).
"Ranges of values" means that the predictions are based on statistical inferences: in general, the first 5 digits can be predicted with a very high degree of accuracy with a single attempt - especially for individuals born after 1988 and in less populous states. In some cases, we were able predict the whole 9 digits of individual SSNs at the very first attempt. More often, the predictions produce windows of values that are likely to include the actual 9 digits. These windows can be very large (and, therefore, inaccurate) for certain years and states (for instance, for individuals born in California in 1973), but can get very narrow (and therefore more concerning, in terms of identity theft risks) for smaller states and recent years (for instance, 1 out of 20 SSNs of individuals born in DE in 1996 in our dataset could be identified with just 10 or fewer attempts per SSN).
Q. How do your SSN predictions work?
Our predictions are based on the fact that SSNs are assigned according to a complex yet regular - and therefore predictable - pattern. The prediction works based on the interpolation of an individual's date and state of birth with SSN issuance patterns derived from the so-called "Death Master File", a publicly available file reporting SSNs, names, dates of birth and death, and states of SSN application for individuals whose deaths have been reported to the SSA (also popularly known as SSDI or SSN Death Index). Part of the process is described in the PNAS paper. Certain details have been omitted from publication.
Q. How did you verify your predictions?
We ran two tests. In the first test, we plotted the SSNs of Death Master File (DMF) records versus time for data between 1973 and 2003. We observed statistical patterns that appeared in the DMF data; then, we used these patterns to predict the SSNs of DMF records. In a second test, we interpolated demographic data extracted from students' profiles on an online social network, with patterns extracted from the DMF, and used it to predict the profile owners' SSNs. We verified the accuracy of our predictions against the individuals' actual SSNs using a secure, IRB-approved, anonymized protocol which only produced aggregate statistics, without revealing to us the actual SSN of any individual in particular.
Q. If the algorithm only produces windows of values likely to include the correct SSN, why is this a concern?
Because various public- and private-sector online services may be attacked to test (using brute-force verifications) subsets of variations predicted by the algorithm.
Statistical predictions of windows of possible SSNs do not imply, alone, that an exact SSN will be found. However, when the range of values wherein an SSN is likely to fall gets dramatically reduced, a number of "brute force" attacks which would be otherwise inefficient or unfeasible become possible and feasible. When one or two attempts are sufficient to identify a large proportion of issued SSNs' first five digits, an attacker has incentives to invest resources into harvesting the remaining four from public documents or commercial services. When fewer than 10, 100, or 1,000 attempts are sufficient to identify complete SSNs for massive amounts of targets, attackers can exploit various public- and private-sector online services (such as online "instant" credit approval sites, as discussed in the paper) to test subsets of variations predicted by the algorithm in order to verify which SSN corresponds to an individual with a given birth date.
Q. Have you "broken" some secret code? Doesn't the Social Security Administration publicly discloses information about the assignment scheme?
No, we have not broken a secret code, and yes, the assignment scheme is publicly available. The SSN assignment scheme was created in the 1930s and was not designed to be "secure": back then, it was not imagined that one day SSNs would start being used for authentication. The assignment scheme is complex, and that complexity has led to the belief that the assignment, from the perspective of the user, is effectively random (see ``SSNs are assigned randomly by computer within the confines of the area numbers allocated to a particular state based on data keyed to the Modernized Enumeration System'' [SSA, 2001]). Indeed, we only used publicly available information, and ended up discovering, based on that information, that the randomness is effectively so low that the entire 9 digits of an SSN can be predicted with a limited number of attempts. We also discovered that certain interpretations of the assignment scheme held outside the SSA were, in fact, incorrect.
Q. Isn't this old news? Everybody knows that Area Numbers are associated with states (etc.)
Yes, the SSN assignment scheme is well known, and yes, the existence of a link between Area Numbers and states is public knowledge - but the patterns we discovered (and the accuracy of the predictions based on them) are not.
As noted in the manuscript, the SSN assignment scheme is public knowledge (p. 1). > In fact, previous work in this area used those patterns to estimate when and where a SSN may have been issued (p. 1 and [Wessmiller, 2002], [Sweeney, 2004], [EPIC, 2008]: that is, starting from a known SSN, and trying to infer the state and the range of years when it may have been issued. Instead, our work focused on the inverse, harder, and much more consequential inference: exploiting the presumptive exact date and location of SSN issuance to estimate, quite reliably, SSNs. This became possible because:
- We discovered (p. 3) that the interpretation held outside the SSA about how Area Numbers are assigned was incorrect: contrary to a commonly held view about their assignment, the same AN is used for 9,999 consecutively assigned SSNs (under the interpretation of the assignment scheme held outside the SSA, the SSA was believed to rotate through all of a state's ANs for each assigned SN. Such scheme would render the AN random for states with multiple ANs, and the predictions we present in this article dramatically less accurate).
- We discovered (p. 4) that the assignment of the last 4 digits is not only sequential (as indeed stated in the publicly available information about the assignment scheme), but in fact highly correlated with the applicant's date of birth, and therefore not random (note that the SSA states, instead, that ``SSNs are assigned randomly by computer within the confines of the area numbers allocated to a particular state'' [SSA, 2001]). In various cases, we were able to predict the entire 9-digits of an SSN at the first attempt (the odds of that happening by random guess are roughly 1 over 1 billion). This is particularly the case for SSNs assigned after the onset of the EAB (1987 onwards).
- We discovered that the analysis of publicly available SSNs assigned to deceased individuals (and included in the DMF) allows the inferences of granular assignment patters that make it possible to predict the SSNs of individuals still alive. For instance, the relationship between Area Numbers and states, while public knowledge, would not be sufficient, alone, to predict Area Numbers except in very specific cases (see p. 1): low-population states (such as WY) and certain U.S. possessions are allocated 1 AN each - implying that knowledge that an individual applied for his/her SSN in that state or possession does indeed provide almost certain knowledge of the first 3 digits of his/her SSN. However, other states are allocated sets of ANs. For instance, an individual applying from a zipcode within the state of New York may be assigned any of 85 possible first 3 SSN digits. Therefore, knowledge that an individual applied for his/her SSN in that state provides low odds (1 over 85) of correctly guessing his/her first 3 digits with a single random guess. Those odds do not even include the probability of also correctly guessing the Group Numbers - which vary from 01 to 99 in combination with the different Area Numbers.
In short, without the discovery of patterns linking SSN digits to demographic data, knowledge of the assignment scheme would not be sufficient to predict neither the first 5 digits or in fact the entire 9 digits of an SSN with a degree of accuracy necessary to expose them to practical risks of identification. For instance, the probability of correctly guessing the first 5 digits of the SSN of an individual born in NY in 1998, even assuming knowledge that the SSN was issued within that state, would be 0.012%, and the probability of correctly guessing the entire 9 digits with fewer than 1,000 attempts would be 0.0012%. However, under the more granular understanding of the relationships between assignment scheme and demographic patterns described in the manuscript, those probabilities are 30% and 3% respectively: several orders of magnitude larger, and much more vulnerable to brute-force attacks. See Table 6 on p. 27 of the Supporting Information.
Q. Can the predictability of SSNs lead to identity theft? Does this research publication provides all is needed to acquire SSNs?
No. Aside from the fact that sensitive details were omitted from the article, to move from mere statistical predictions to actual identity theft an attacker needs to exploit holes and weaknesses in the U.S. identity "infrastructure:" the widespread availability of personal, demographic data for millions of individuals, the existence of large botnets of compromised computers, and the lax identity matching and authentication techniques adopted in the credit/financial sectors (among others). Our findings can help combat and decrease identity theft by showing why such known (yet underestimated) weaknesses in our identity infrastructure should finally be addressed; by alerting industry and policy-makers of a new exploit; and by highlighting the need to abandon SSNs as passwords and move toward more secure, efficient, and privacy-preserving means of authenticating identities.
Q. How does this differ from previous research?
Previous research in the area of SSNs focused on detecting SSNs in public databases, using SSNs to link data across multiple data sources, or - in the cases closest to our study - inferring the year[s] and state of issuance of known SSNs. Per se, the existence of SSN issuance patterns is well known - the SSA makes certain details available through public materials, and others (notably, Latanya Sweeney and her "SSN Watch") have used those patterns, plus a combination of public and private SSN data, to estimate when and where a <known> SSN may have been issued [Wessmiller, 2002], [Sweeney, 2004], [EPIC, 2008]. However, our work focuses on the inverse, harder, and much more consequential inference: it shows that it is possible to exploit the presumptive time and location of SSN issuance to estimate, quite reliably, <unknown> SSNs.</unknown></known>
Q. What data do you need to predict SSN? Isn't birth data hard to come by?
Data about SSNs from the so-called "Death Master File," which is publicly available, and demographic data (dates of birth and states of birth) from wherever it is available. Mass amounts of birth data for US residents can be obtained or inferred - often for free, or at negligible per unit prices - from multiple sources, including commercial data brokers (such as www.peoplefinders.com, which sells access to birth data and personal addresses for ``almost every adult in the United States''); voter registration lists (for most states); online free people searches (such as www.zabasearch.com); as well as social networking sites: our estimates indicate that at least 10 millions US residents make publicly available or inferable their birthday information on their online profiles.
Q. From which social networking site did you find data for one of your tests?
There is no specific networking site which is uniquely exposed. The data can be extracted from several such sites, as well as other sources, as noted above.
Q. Aren't SSN in fact as available as birth data?
They are not.
It is true that SSNs are widely available. They have been found in public records of federal agencies, states, counties, courts, hospitals, and so forth [The President’s Identity Theft Task Force, 2007], as well as in personal documents, such as online resumes [Sweeney, 2006]. Companies exchange SSNs in personal information markets, and individuals obtain ``credit reports,'' containing their SSNs, from credit bureaus; stolen SSNs are lucratively exchanged in underground cybermarkets [Franklin, 2007]. However, the GAO found that only few brokers offering SSNs for sale to the general public are actually able to sell whole SSNs [GAO, 2006]. Furthermore, the GAO also found that while still widespread, SSNs are becoming harder to find in public documents [GAO, 2008]. In fact, the number of SSNs widely available may also be decreasing because of numerous legislative initiatives in this area. Various recent initiatives have been focusing on removing SSNs from public exposure or redacting their first five digits [NCSL, 2007], [FTC, 2008], and [GAO, 2008]. On the other hand, birth data remains widely available, as noted above.
- 4
- 11
Generated from TLDR This:
By Sumit Goswami While the metaverse bridges the physical and virtual worlds through innovations in hardware and; software, It needs a lot of innovations at all levels.
Artificial Intelligence is being widely used for various healthcare use cases like improving diagnosis, predicting and preventing the spread of communicable diseases, enhancing patient and health system engagement, powering surgical robots, and improving health system efficiency.
Web3.0 is expected to change the way we use the internet today.
We expect this to be portable and personal, semantic web, decentralised, more secure, enhanced user control on experience and behaviour, and a virtual world that almost mimics the real world using the Metaverse technology.
Metaverse has the capability to bring about that change, it has the ability to change the way we work, interact, consume and transact.
The author is the managing director of India with Renew Global 

















 Pumpkin Spice Mafia Gang Gang
Pumpkin Spice Mafia Gang Gang 









 Facebook busts
Facebook busts  influence network targeting Americans on abortion and guns ahead of midterms
influence network targeting Americans on abortion and guns ahead of midterms 







 Fast Company used to send an obscene Apple News push notification
Fast Company used to send an obscene Apple News push notification 





 you are loved
you are loved 







 | Hacker News
| Hacker News


 upgraded by Stable Diffusion
upgraded by Stable Diffusion
 or
or  ?
?













 slapfights occur in /r/programming when rust invades the linux kernel
slapfights occur in /r/programming when rust invades the linux kernel 
](/images/16642641415516248.webp)

 Subreddit Discriminates Against Anyone Who Doesn’t Call Texas Governor Greg Abbott ‘A Little Piss Baby’ To Highlight Absurdity Of Content Moderation Law
Subreddit Discriminates Against Anyone Who Doesn’t Call Texas Governor Greg Abbott ‘A Little Piss Baby’ To Highlight Absurdity Of Content Moderation Law 

 Sexist Pennsylvania school district accused of banning Girls Who Code book series
Sexist Pennsylvania school district accused of banning Girls Who Code book series 







