- 22
- 59
!mathematics again with "stochastic terrorism"
Autocracy: silence these dissidents!
Elon: Right away, sir!
Democracy: remove these misinformation bots and stochastic terrorists.
Elon: Over my dead body!
Exactly. Not to mention himself feeding the Fire with right wing disinformation and almost incitement of violence
Democracy is when le hate speech censorship by a random judge
I hope other nations follow suit. There should be serious repercussions to actively allowing hate speech and misinformation, which is what Musk is doing by unbanning accounts and rolling down moderation.
The UK riots that happened last month happened mostly because of misinformation and calls to violence that spread on Twitter, Facebook and even Telegram. This isn't some "1984 censorship" type shit, this really is as simple as "Twitter did nothing whilst many boosted accounts called for patriots to set fire to asylum centres and mosques".
I'd love to understand why people think that sort of stuff should be allowed to happen on mainstream social media sites.
100% agree, what Musk did during the UK riots was fueling stochastic terrorism. The CEO of Xitter didn't just participate, he started it.
After that he boosted some German right wing influencers, actively shared and relativized posts of the German far right party and tried to engage the German chancellery in an insane "discussion". All of that before replying with a "get fricked" meme to Thierry Breton, the EU's head of digital services and law enforcement, who warned Musk in an open letter that the missing content moderation of his platform makes Xitter susceptible to a ban, short term or permanent.
I can't wait until a ban will be discussed and hopefully enforced.
 YAH NEED A LOICENSE FOR THAT ACCOUNT MATE
YAH NEED A LOICENSE FOR THAT ACCOUNT MATE
Who needs fascist Musk's toxic platform anyway.
Do Europe next, please.
Pls daddy EU 
- 49
- 90
Orange Site:
https://news.ycombinator.com/item?id=41399872

https://old.reddit.com/r/hardware/comments/1f4ti5n/anandtech_shutting_down/
https://old.reddit.com/r/Android/comments/1f501hm/anandtech_shuts_down_after_27_years/
https://old.reddit.com/r/gadgets/comments/1f4xi5v/anandtech_is_shutting_down/
https://old.reddit.com/r/LinusTechTips/comments/1f4ty4v/anandtech_is_shutting_down/
https://old.reddit.com/r/pcgaming/comments/1f4xmnv/anandtech_is_closing_down/
https://old.reddit.com/r/technology/comments/1f4tzeh/an_anandtech_farewell/

After 27 years of providing in-depth coverage of the amazing world of PC and mobile hardware, AnandTech is saying farewell. We want to thank everyone from the AnandTech community for their support and passion for what we’ve done over the yearshttps://t.co/3EGh4FJguE
— AnandTech (@anandtech) August 30, 2024
AnandTech shuts down after 27 years ☹️ Anand built a legendary site for covering the inner workings of computers. It’ll be sorely missed 🫡 https://t.co/BLanCnjptl
— Tom Warren (@tomwarren) August 30, 2024
The end of an era. @anandtech, started in 1997 by a then 14-year-old @anandshimpi, is closing its doors after 27 years. I worked there for 11 years and learned my craft. Here's my video on it. It gets a little emotional.https://t.co/KbQxDggfST pic.twitter.com/546ozCweEf
— 𝐷𝑟. 𝐼𝑎𝑛 𝐶𝑢𝑡𝑟𝑒𝑠𝑠 (@IanCutress) August 30, 2024
Mention of AnandTech still brings back memories of the early GPU days for me. https://t.co/WGC2MWhp2l
— John Carmack (@ID_AA_Carmack) August 30, 2024

https://lemmy.world/post/19224370?scrollToComments=true
https://lemmy.world/post/19223871?scrollToComments=true
https://lemmy.world/post/19232541?scrollToComments=true

- collectijism : This should have a lot more than 30 comments but sand Nazi banned us all
- 93
- 125
Twitter will be shut down in macacoland within 24 hours and the Brazilians trying circumvent the rules by using a VPN will be subjected to a fine of 50,000 R$ (around 9,000 dollars) per day of use.
- 78
- 35
No, I will not use Linux 
!applechads help me out
- 45
- 117
Introduction
Like many, Sam Curry and I spend a lot of time waiting in airport security lines. If you do this enough, you might sometimes see a special lane at airport security called Known Crewmember (KCM). KCM is a TSA program that allows pilots and flight attendants to bypass security screening, even when flying on domestic personal trips.
The KCM process is fairly simple: the employee uses the dedicated lane and presents their KCM barcode or provides the TSA agent their employee number and airline. Various forms of ID need to be presented while the TSA agent's laptop verifies the employment status with the airline. If successful, the employee can access the sterile area without any screening at all.
A similar system also exists for cockpit access, called the Cockpit Access Security System (CASS). Most aircraft have at least one jumpseat inside the cockpit sitting behind the flying pilots. When pilots need to commute or travel, it is not always possible for them to occupy a revenue seat, so a jumpseat can be used instead. CASS allows the gate agent of a flight to verify that the jumpseater is an authorized pilot. The gate agent can then inform the crew of the flight that the jumpseater was authenticated by CASS.
The employment status check is the most critical component of these processes. If the individual doesn't currently work for an airline, they have not had a background check and should not be permitted to bypass security screening or access the cockpit. This process is also responsible for returning the photo of the crewmember to ensure the right person is being authorized for access. So how does this work, when every airline presumably uses a different system to store their employee information? That is what we were wondering, and where it gets interesting...
ARINC
ARINC (a subsidiary of Collins Aerospace) appears to be contracted by the TSA to operate the Known Crewmember system. ARINC operates a few central components, including an online website for pilots and flight attendants to check their KCM status, and an API to route authorization requests between different airlines. Each airline appears to operate their own authorization system to participate in KCM and CASS, and it interacts with the "hub" of ARINC.
The TSA and airlines can send requests such as CockpitAccessRequest and CrewVerificationRequest to ARINC, which then routes it to the appropriate airline's system and receives the response. There are 77 airlines currently participating in KCM. While larger airlines have likely built their own system, how do smaller airlines respond to these requests to participate in KCM or CASS?
FlyCASS.com
In our search for vendors that actually run the authorization systems, we found a site called FlyCASS which pitches small airlines a web-based interface to CASS. Intrigued, we noticed every airline had its own login page, such as Air Transport International (8C) being available at /ati. With only a login page exposed, we thought we had hit a dead end.
Just to be sure though, we tried a single quote in the username as a SQL injection test, and immediately received a MySQL error:
This was a very bad sign, as it seemed the username was directly interpolated into the login SQL query. Sure enough, we had discovered SQL injection and were able to use sqlmap to confirm the issue. Using the username of ' or '1'='1 and password of ') OR MD5('1')=MD5('1, we were able to login to FlyCASS as an administrator of Air Transport International!
KCM and CASS Admin
It turns out that FlyCASS also operates both KCM and CASS for its participating airlines. Now that we are an administrator of Air Transport International, we are able to manage the list of pilots and flight attendants associated with them. Surprisingly, there is no further check or authentication to add a new employee to the airline. As the administrator of the airline, we were able to add anyone as an authorized user for KCM and CASS.
To test that it was possible to add new employees, we created an employee named Test TestOnly with a test photo of our choice and authorized it for KCM and CASS access. We then used the Query features to check if our new employee was authorized. Unfortunately, our test user was now approved to use both KCM and CASS:
At this point, we realized we had discovered a very serious problem. Anyone with basic knowledge of SQL injection could login to this site and add anyone they wanted to KCM and CASS, allowing themselves to both skip security screening and then access the cockpits of commercial airliners.
We ended up finding several more serious issues but began the disclosure process immediately after finding the first issue.
Disclosure
We had difficulty identifying the right disclosure contact for this issue. We did not want to contact FlyCASS first as it appeared to be operated only by one person and we did not want to alarm them. On April 23rd, we were able to disclose the issue to the Department of Homeland Security, who acknowledged the issue and confirmed that they "are taking this very seriously". FlyCASS was subsequently disabled in KCM/CASS and later appears to have remediated the issues.
After the issue was fixed, we attempted to coordinate the safe disclosure of this issue. Unfortunately, instead of working with us, the Department of Homeland Security stopped responding to us, and the TSA press office issued dangerously incorrect statements about the vulnerability, denying what we had discovered.
The TSA press office said in a statement that this vulnerability could not be used to access a KCM checkpoint because the TSA initiates a vetting process before issuing a KCM barcode to a new member. However, a KCM barcode is not required to use KCM checkpoints, as the TSO can enter an airline employee ID manually. After we informed the TSA of this, they deleted the section of their website that mentions manually entering an employee ID, and did not respond to our correction. We have confirmed that the interface used by TSOs still allows manual input of employee IDs.
Several other attacks were also likely possible. Since our vulnerability allowed us to edit an existing KCM member, we could have changed the photo and name of an existing enrolled user, which would likely bypass any vetting process that may exist for new members. If you are able to obtain an unenrolled KCM barcode, you can also enroll it to an employee ID yourself on the KCM website.
Timeline
04/23/2024: Initial disclosure to ARINC and FAA
04/24/2024: Subsequent disclosure to DHS via CISA
04/25/2024: DHS CISO confirms they are working on a resolution
05/07/2024: DHS CISO confirms FlyCASS was disconnected from KCM/CASS
05/17/2024: Follow-up to DHS CISO about TSA statements (no reply)
06/04/2024: Follow-up to DHS CISO about TSA statements (no reply)
Collaborators
- 13
- 39
Context for s*x-havers:
Rust is a recent programming language which includes safety measures to prevent programmers from writing certain types of bugs. Linux is written in C, an old programming language which doesn't have any sort of security features. Linux has many millions of line of C code, and there is a push to transition at least part of the code to Rust to increase the overall security, but many object as there is a lot of friction in integrating the 2 languages and also people don't want to learn a new language to keep doing their job.
Today one of the guys pushing Rust's adoption into Linux has officially given up, citing "too much non-technical nonsense" and pointing to these 3 heated minutes during his talk at a technical conference for Linux developers:
- 28
- 53
- 10
- 34
New startup investment grifters want to be real-life Bond villains. Apparently planning a fleet of giant, reflective orbital satellites.
Why? So users can log into their app (naturally) and order sunlight on a specific location after dark.
Maybe they will get funding from North Korea to bring Die Another Day (objectively the most r-slurred film of the series) to life.
- 16
- 16
I remember doing mess duty (dishwashing) in highschool only for a few days during a military camp thing. (We all had to take turns since it was military training type shit) It was super easy because we had a big machine that would automatically clean and dry all the dishes. We just had to make sure there wasn't any plastic or large food items on the plate.
Only annoying part was this straggy little kid who kept crying about how I forgot some wrapper on the plate or whatever. Neighbor, idgaf, if the dish washing machine breaks. This isn't the military, its a day camp, im focused on getting one of these girls to suck my peepee not doing some dishes.
Anyway, my point is dishwashing isn't a hard job. Quit crying.
- 23
- 58
- 15
- 8
@timmy_blueballs have become less r-slurred and now understand how SQL injections work and how too defend against them by having SQL code take input values as literal text values rather than as SQL input values.
@timmy_blueballs still have many questions about some of the SQL functions and how they work but @timmy_blueballs presume @timmy_blueballs will not have too really care that deeply too get started on @timmy_blueballs's coding career and can learn along the way.
What would you all suggest @timmy_blueballs try too learn now? @timmy_blueballs was thinking of studying HTML and finishing up by tomorrow night.
Good direction will be appreciated.
Thanks.
@timmy_blueballs stand with Israel.
- 48
- 17
- 23
- 67
why else would he add image support to HTML? https://t.co/n1D0S4k5aP pic.twitter.com/42ZnkQ2dyM
— sandrone (@kosenjuu) August 25, 2024
- 5
- 47
- HailVictory1776 : Someone please post that France must be destroyed for their disgusting hatred of freedom and liberty
- 41
- 79
Telegram Founder Pavel Durov Arrested in France, Reportedly For Refusing to Censor Contenthttps://t.co/zXC8PJoXJR
— Reclaim The Net (@ReclaimTheNetHQ) August 24, 2024
- 20
- 14
After that what should be @timmy_blueballs's next step too find a job?
No, the SQL program @timmy_blueballs is currently learning from is not certified.
Any help would be appreciated.
Thanks for the help.
@timmy_blueballs stand with Israel.
- stuttered : Repost
- 15
- 56
- 7
- 35
I imagine it's pretty bad if the French are executing a warrant on you for child s*x crimes.







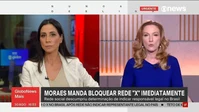
 STF decision to ban X in
STF decision to ban X in  . Redditors accuse Musk of stochastic terrorism
. Redditors accuse Musk of stochastic terrorism














 God bless this mess
God bless this mess 
 ) Make the plunge back to Micro$oft or stick with Crapple? I look forward to hearing totally original burns about Apple being for r-slur children
) Make the plunge back to Micro$oft or stick with Crapple? I look forward to hearing totally original burns about Apple being for r-slur children 






 Diversity Is Our Strength
Diversity Is Our Strength 
















.webp?h=8)






 )
)



 New tech startup grift just dropped
New tech startup grift just dropped





















 )
)




