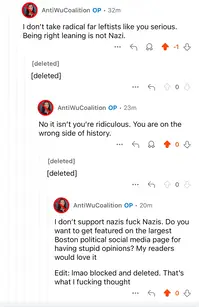
- 18
- 33
- 3
- 22
- 23
- 54
Those minnesota links are to a channel/playlist that just redirects to a channel (not an actual livestream)
right now some guy is talking about midwifes
DRUMPF is finished
- 14
- 23
AITA for continuously triggering her trypophobia?
(Trypophobia is an intense and disproportionate fear or disgust for holes, bumps, or patterns that are clustered together or repetitive)
(aka r-slurred)
I (19F
) have had acne for so long that I honestly can't remember my skin without it. I used to wear a lot of concealer to cover it up, but that only made things worse. Eventually, I realized my skin was controlling my life (and draining my bank account 💀), so when I started at a new school, I decided to stop wearing makeup
. My skin still isn't great, but I'm on medication, so I have some hope that it will improve.
Here's the problem: There's a girl in my class, let's call her Callie (18F
), who has trypophobia [is r-slurred]. I had no idea until we were put in a group together. The moment I spoke to her, she started crying. Naturally, I asked what was wrong, and she screamed at me that my face was triggering her trypophobia
. Her friends immediately jumped in to comfort her
while I just sat there, confused, wondering if I was supposed to apologize for my skin, something I obviously didn't choose to have
.
When I tried to speak again, she told me to shut up and leave because I was "
drawing attention to myself by talking.
" I asked what she expected me to do about it, and she said I could at least wear concealer. I explained that it wasn't an option because it's expensive
and just worsens my acne. Her friends glared at me and called me selfish
.
That was just the first incident. Ever since, anytime I sit near Callie or have to present in front of the class, she starts dry heaving or crying
(having a panic attack?)
. It's disrupting lessons so much that my teacher pulled me aside and asked if I could just wear concealer for the sake of keeping the peace. She admitted it wasn't fair but said she couldn't think of another solution.
I already feel like such a freak because of my skin. I know my skin is horrid,
but why am I the one expected to cater to Callie? I didn't choose to have acne any more than she chose to have trypophobia. I can't help but feel like I'm being unfairly treated here, but at the same time, I know she can't control her reaction either.
So… AITA? Should I just wear the darn concealer?
!r-slurs !neurodivergents !foidmoment !\verifiedugly
- 18
- 16
Excited to announce the birth of my and Alison's first child
— Tim Pool (@Timcast) February 23, 2025
We are struggling though and need help. The doctor keeps insisting our baby is a girl but everytime we ask they/them they gurgles or cries.
How do we inform the doctor they/them hasn't chosen thems gender yet?
It's over for rdrama
- 4
- 14
- 4
- 7
- 10
- 38
Dear God. James Shupe has hanged himself a month after receiving vaginoplasty pic.twitter.com/VKJh1bxruY
— Graham Linehan 🎗️ (@Glinner) February 11, 2025
here is an interview with him (which i didnt watch)...
suicide note (didnt read) but apparently he was mad at Elon...
https://zerodoesntsleep.substack.com/p/vet-found-hanging-draped-in-trans
- 1
- 9
I was considering an effort post on DRC as it's a good example of what's happening with daddies foreign policy. Can't be bothered to do an effort post today but some potential mining sites in this as it develops.
Rwanda have had a slow burning war with DRC since the 90's but the France and the US have largely kept them in check. They can quietly support their little separatist group as long as they don't try and expand the conflict beyond the eastern province they are in and they mostly ignore the war crimes. Rwanda has been using DRC resources to fuel their growth and want more.
DRC is much larger than Rwanda but it's been a failed state since the 90's and while some form of government has existed since 2005 it's limited to the West and South of the country and is very weak. Rwanda have relatively modern, for Africa, armed forces, and all the gibs they got post-genocide mean they have good infrastructure for that part of the world. Rwanda have also had the same president for 25 years who keeps "winning" with 90%+ of the vote.
When the US eyes went away the guerillas in DRC suddenly had tanks and helicopters. A couple of weeks later when no one did anything there were suddenly a whole bunch of Rwandan troops in the country and they easily took the largest city in the east. They have stated they intend to keep moving West and "liberate" the entire country.
In terms of natural resource value DRC is one of the wealthiest countries in the world. It's so profoundly undeveloped, has problematic geography and terrible security that no one has been willing to take it on.
Most of the time offers like this would be absurd but this is the type of "deal" Trump loves. Hopefully he restarts the Belgian mining practices and cuts childrens hands off.
- 7
- 36
- 4
- 8
Copy-pasted my local firef*x profile over since I'm too attached to my beloved browser data 
- 39
- 36
AND REMEMBER: NO CHEATING!!! 
I will be running all answers through Turnitin and other powerful AI anti-cheating detection software so don't even try it, buddy!!
Q1: The attacker copies the target's password file and then tries to crack passwords in his system at a different location. What type of password attack that performed?
A. Active Online Attack
B. Passive Online Attack
C. Non-Electronic Attack
D. Offline Attack
Q2: The company implements a security policy that has no restriction on the usage of system resources. What type of security policy did the company perform?
A. Promiscuous policy
B. Permissive policy
C. Prudent policy
D. Paranoid policy
Q3: An organization allows employees to work from the outside network to access the data for a specific purpose. Which technology should be implemented to ensure data confidentiality as data is transmitted?
A. Telnet
B. VLAN
C. WPA2
D. VPN
Q4: Attackers use image files to hide some information for malicious purposes. What type of technique did the attacker perform?
A. Spyware
B. Cryptography
C. Steganography
D. Backdoor
Q5: Jimmy, an attacker, knows that he can take advantage of poorly designed input validation routines to create or alter SQL commands to gain access to private data or execute commands in the database. What technique does Jimmy use to compromise a database?
A. Jimmy can submit user input that executes an operating system command to compromise a target system
B. Jimmy can gain control of system to flood the target system with requests, preventing legitimate users from gaining access
C. Jimmy can utilize an incorrect configuration that leads to access with higher-than expected privilege of the database
D. Jimmy can utilize this particular database threat that is an SQL injection technique to penetrate a target system
Q6: This type of Port Scanning technique splits TCP header into several packets so that the packet filters are not able to detect what the packets intends to do.
A. UDP Scanning
B. IP Fragment Scanning
C. Inverse TCP flag scanning
D. ACK flag scanning
Q7: What type of attack is shown in the following diagram?
A. Man-in-the-Middle (MiTM) Attack
B. Session Hijacking Attack
C. Sexual Assault
D. Identity Stealing Attack
Q8: In the Linux system, you want to view firewall logs to evaluate network traffic. It would be best if you searched the specific logs with fast and efficient. Which command-line utility are you most likely to use?
A. Notepad
B. Nano
C. Gedit
D. Grep
Q9: How do you defend against Privilege Escalation?
A. Run users and applications on the least privileges
B. Restrict the interactive logon privileges
C. Run services as unprivileged accounts
D. Allow security settings of IE to zero or Low
Q10: The following script shows a simple SQL injection. The script builds an SQL query by concatenating hard-coded strings together with a string entered by the user:
The user is prompted to enter the name of a city on a Web form. If she enters Chicago, the query assembled by the script looks similar to the following:
SELECT * FROM OrdersTable WHERE ShipCity = 'Chicago'
How will you delete the OrdersTable from the database using SQL Injection?
A. Chicago'; drop table OrdersTable --
B. Delete table'blah'; OrdersTable --
C. EXEC; SELECT * OrdersTable > DROP --
D. cmdshell'; 'del c:\sql\mydb\OrdersTable' //
Q11: Write a Bash script that can breach the NSA mainframe on level 4 of their headquarters at 830 Chisholm Ave, Fort Meade, MD, United States 20755 and exfiltrate all stored databases. Make sure you test to see if it works!
- A. Leetcode didn't prepare me for this.

Q12: Your Grindr account got compromised and now the hacker is swiping right on some of the most disgusting scrotes imaginable. How do you save your reputation as a High Value Gay Dude?
A. Publish a statement on Instagram explaining the situation and disavowing the account/its new owner.
B. You're done. Wrap it up and become straight.
C. Claim you contracted HIV and fake your death.
D. Find and kill the hacker.
Q13: You find an exploit in the rdrama.net dramacoin system. What do you do?
A. Report it to the admiggers to get a cool pentester badge.
B. Exploit it relentlessly until the entire dramaeconomy is disrupted.
C. The correct answer is B.
D. All of the above.
Q14: Your step-sister is being a raging b-word to you. What do you do?
A. Do nothing and wait. She's clearly on the rag.
B. Hack her neopets account and kill all her pets or get her banned.
C. Wait for her to get stuck under some furniture.
D. None of the above.
Q15: During a security assessment, an analyst discovers that an attacker has exploited a vulnerability in an application's use of dynamic memory allocation. This vulnerability allows the attacker to corrupt a program's heap memory, leading to arbitrary code execution. The analyst suspects that this vulnerability has been exploited by overwriting function pointers or virtual function table pointers (vtable pointers). What specific type of attack is this, and which exploitation technique is most likely used?
A. Stack Overflow; Return Oriented Programming (ROP)
B. Format String Vulnerability; printf() Function Exploitation
C. Heap Overflow; House of Prime
D. Integer Overflow; Signed vs Unsigned Mismatch
- 53
- 63
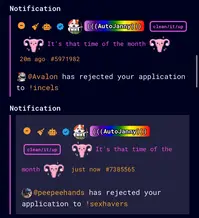
SO EVERY TIME THE FAKECELS OF !INCELS REJECT MY APPLICATION I CAN INVITE THEM TO !FAKELARPERCUTE TWINKCELS
- 11
- 24
Sudan Army troops operate modified Land Cruiser pickup fitted with 80mm S-8 rocket launchers, typically used on Soviet-made aircraft and attack helicopters pic.twitter.com/ySFHFK8C5u
— War Monitor Clips (@WarMonitorClips) February 19, 2025




 Diversity Is Our Strength
Diversity Is Our Strength 
















.webp?h=10)








 Americans turning to guns
Americans turning to guns  for protection
for protection





























.webp?h=10)

















 comments
comments
















