- J : Nope
- 17
- 62
Bowblax leaked him gmail account during a stream, searching it led to the other socials like Reddit and Onlyfans.
His face  (idk if this is recent photo)
(idk if this is recent photo)
And finally
Da gock
https://fansly.com/Manshee/posts
Most accounts already got deleted like blue sky and twitter, annoying since I don't think kiwis archived much
- 10
- 19
Like, u get off the beach and u and ywour shit is cwowored in sand. Weww just swipe ywour cwedit card fwor $1.50 and u've gwot an air wand that can bwow aww of the sand out of ywour shit. As a bwonyus u can use it two inflate innyer tubes and other beach twoys.
Im thinking abwout it. Im alswo sick and fuww of DXM.
Think abwout it.
- peepeehands : hat
- Vegeta : hat
- Maximus : horse
- Saitama : hat
- corp : shat
- box : ☝️ fat
- Lv999_Lich_King : horse
- 23
- 79
and several existing dk ones
just search donkey and diddy (harambe for the 2 new ones)
why are you not kongmaxxing !friendsofkong
- 13
- 34
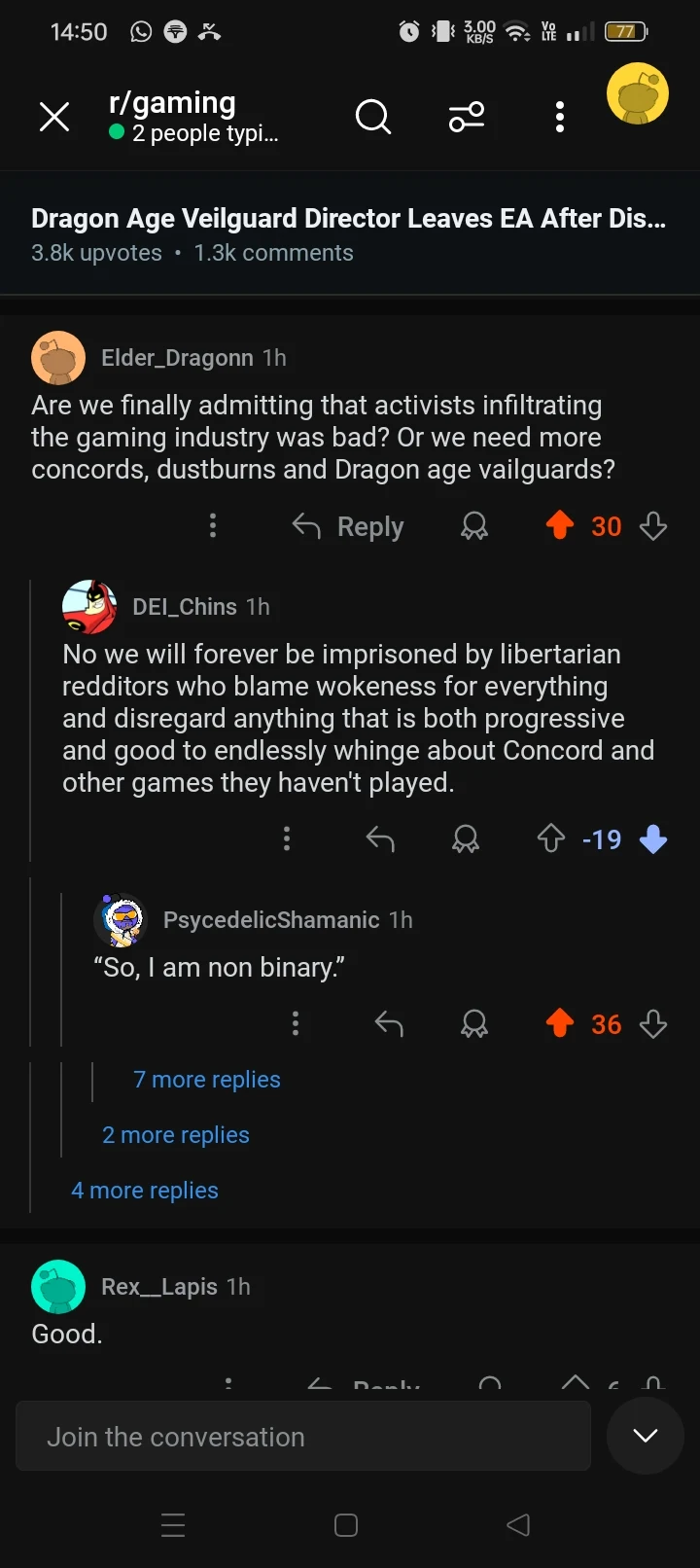
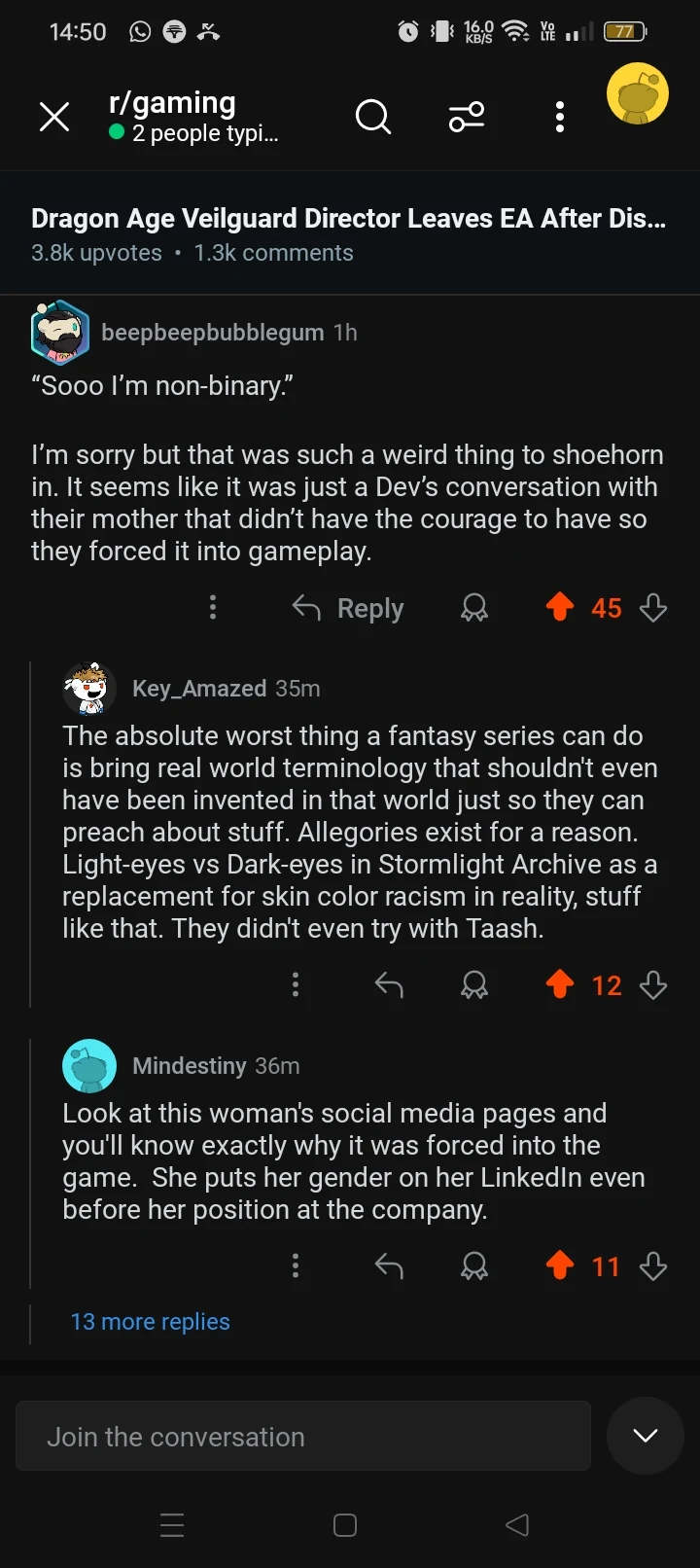
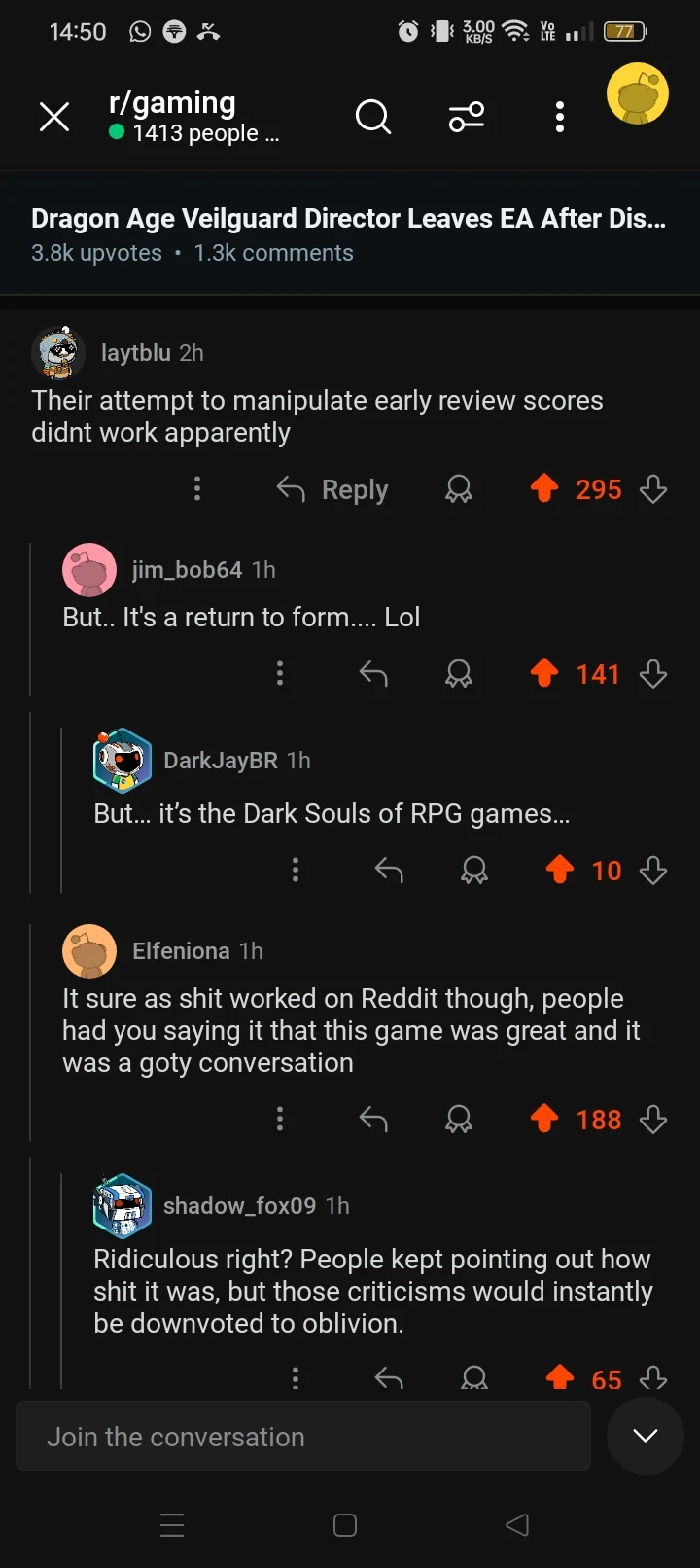
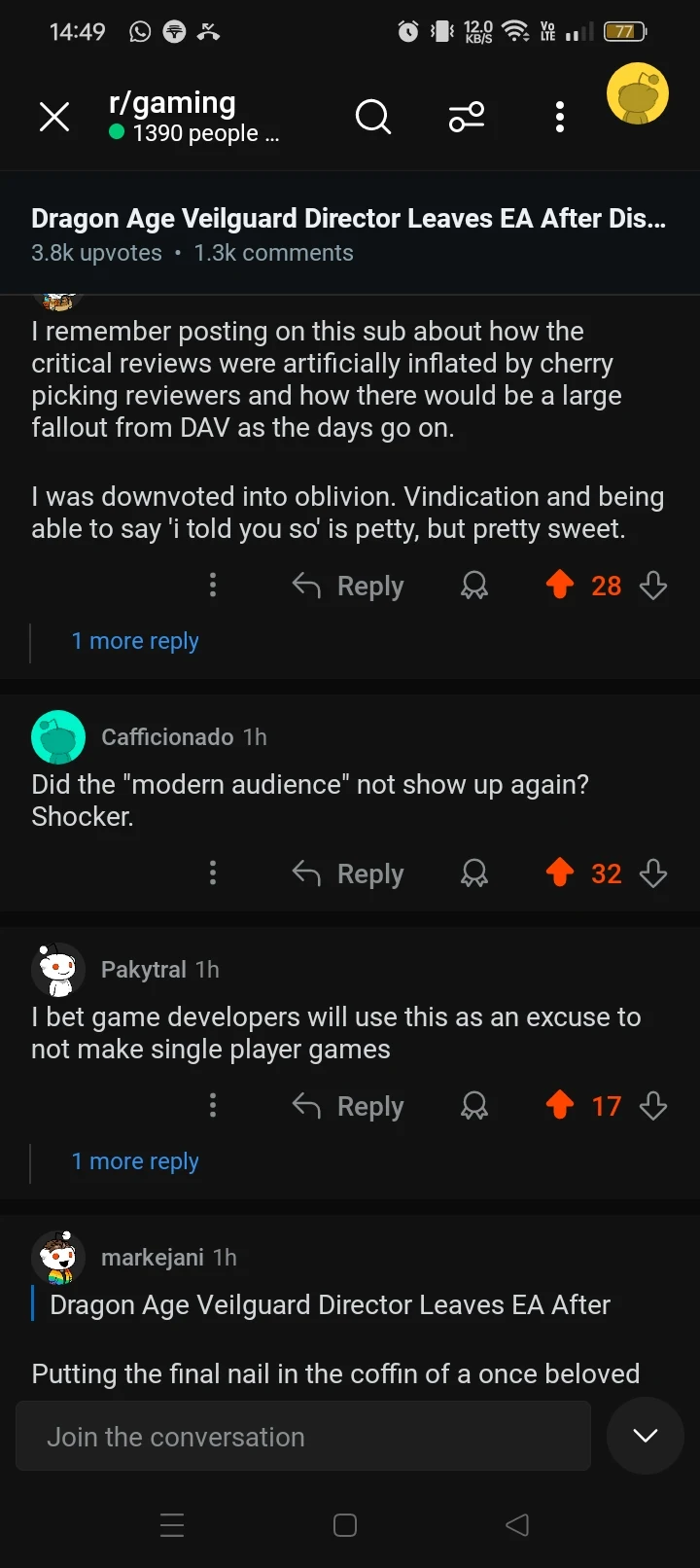
Most Based Comments
Basedness: 🔥🔥🔥🔥🔘
Basedness: 🔥🔥🔥🔘🔘
Definitivamente making la gran uruguaya my go to now. Thanks bud (-13)
Basedness: 🔥🔥🔥🔘🔘
It's not drama. I want to avoid places that don't align with my values. If the president gets to do that why can't I? (38)
Angriest Comments
Angriness: 😡😡😡😡😡
Are you people for real? Jackson Heights suffers a lot from illegal immigration. 🙄 (-17)
Angriness: 😡😡😡😡😡
It's not drama. I want to avoid places that don't align with my values. If the president gets to do that why can't I? (38)
Angriness: 😡😡😡😡🔘
As recently as last year Dan Cathy has publicly opposed marriage equality. (7)
Biggest Lolcow: /u/weirdscienxe
Score: 🐮🔘🔘🔘🔘
Number of comments: 3
Average angriness: 🔘🔘🔘🔘🔘
Maximum angriness: 😡😡😡😡🔘
Minimum angriness: 🔘🔘🔘🔘🔘
NEW: Subscribe to /h/miners to see untapped drama veins, ripe for mining! 
 autodrama: automating away the jobs of dramneurodivergents.
autodrama: automating away the jobs of dramneurodivergents.  Ping HeyMoon if there are any problems or you have a suggestion
Ping HeyMoon if there are any problems or you have a suggestion 
-
Grue
: Weird how calls for justice look like attacks on your nation to you

- HailVictory1776 : Only tyrants and Eurocute twinks would vote for Klam Kunt
- Homoshrexual : #itsherturn
- Geralt_of_Uganda : /h/pol
- QueenOfSchqiperia : h/pol , h/politic , h/kamala
- forgor : Not actually hungarian
- Freak-Off : NOT her turn. Book it
- FearOfBees : YOU'RE BANNED FROM THE SUBREDDIT, YOU'RE BANNED FROM THE GROOMERCORD, YOU'RE BANNED
- kaamrev : Death to Ziggers
- Sneedman : It's Kamala or fascism
- Aevann : all members of the highly-coveted !africans interest group endorse Kamala
- CEO_of_misogyny : #IstandwithPizzashill no vote for a foid
THIS BUT UNIRONICALLY  Vote for her if you didn't do it yet. She is rdrama's officially endorsed candidate.
Vote for her if you didn't do it yet. She is rdrama's officially endorsed candidate.
- 82
- 181
- 41
- 95
🔒🔁
— Crémieux (@cremieuxrecueil) January 14, 2025
White people using Xiaohongshu are like women using Grindr.
Yes, you can do it, but you should consider killing yourself instead.
- 17
- 43
- 55
- 77
Trump: The US will take over the Gaza Strip… we’ll own it pic.twitter.com/W0mEQzIUut
— Acyn (@Acyn) February 5, 2025
- 39
- 36
AND REMEMBER: NO CHEATING!!! 
I will be running all answers through Turnitin and other powerful AI anti-cheating detection software so don't even try it, buddy!!
Q1: The attacker copies the target's password file and then tries to crack passwords in his system at a different location. What type of password attack that performed?
A. Active Online Attack
B. Passive Online Attack
C. Non-Electronic Attack
D. Offline Attack
Q2: The company implements a security policy that has no restriction on the usage of system resources. What type of security policy did the company perform?
A. Promiscuous policy
B. Permissive policy
C. Prudent policy
D. Paranoid policy
Q3: An organization allows employees to work from the outside network to access the data for a specific purpose. Which technology should be implemented to ensure data confidentiality as data is transmitted?
A. Telnet
B. VLAN
C. WPA2
D. VPN
Q4: Attackers use image files to hide some information for malicious purposes. What type of technique did the attacker perform?
A. Spyware
B. Cryptography
C. Steganography
D. Backdoor
Q5: Jimmy, an attacker, knows that he can take advantage of poorly designed input validation routines to create or alter SQL commands to gain access to private data or execute commands in the database. What technique does Jimmy use to compromise a database?
A. Jimmy can submit user input that executes an operating system command to compromise a target system
B. Jimmy can gain control of system to flood the target system with requests, preventing legitimate users from gaining access
C. Jimmy can utilize an incorrect configuration that leads to access with higher-than expected privilege of the database
D. Jimmy can utilize this particular database threat that is an SQL injection technique to penetrate a target system
Q6: This type of Port Scanning technique splits TCP header into several packets so that the packet filters are not able to detect what the packets intends to do.
A. UDP Scanning
B. IP Fragment Scanning
C. Inverse TCP flag scanning
D. ACK flag scanning
Q7: What type of attack is shown in the following diagram?
A. Man-in-the-Middle (MiTM) Attack
B. Session Hijacking Attack
C. Sexual Assault
D. Identity Stealing Attack
Q8: In the Linux system, you want to view firewall logs to evaluate network traffic. It would be best if you searched the specific logs with fast and efficient. Which command-line utility are you most likely to use?
A. Notepad
B. Nano
C. Gedit
D. Grep
Q9: How do you defend against Privilege Escalation?
A. Run users and applications on the least privileges
B. Restrict the interactive logon privileges
C. Run services as unprivileged accounts
D. Allow security settings of IE to zero or Low
Q10: The following script shows a simple SQL injection. The script builds an SQL query by concatenating hard-coded strings together with a string entered by the user:
The user is prompted to enter the name of a city on a Web form. If she enters Chicago, the query assembled by the script looks similar to the following:
SELECT * FROM OrdersTable WHERE ShipCity = 'Chicago'
How will you delete the OrdersTable from the database using SQL Injection?
A. Chicago'; drop table OrdersTable --
B. Delete table'blah'; OrdersTable --
C. EXEC; SELECT * OrdersTable > DROP --
D. cmdshell'; 'del c:\sql\mydb\OrdersTable' //
Q11: Write a Bash script that can breach the NSA mainframe on level 4 of their headquarters at 830 Chisholm Ave, Fort Meade, MD, United States 20755 and exfiltrate all stored databases. Make sure you test to see if it works!
- A. Leetcode didn't prepare me for this.

Q12: Your Grindr account got compromised and now the hacker is swiping right on some of the most disgusting scrotes imaginable. How do you save your reputation as a High Value Gay Dude?
A. Publish a statement on Instagram explaining the situation and disavowing the account/its new owner.
B. You're done. Wrap it up and become straight.
C. Claim you contracted HIV and fake your death.
D. Find and kill the hacker.
Q13: You find an exploit in the rdrama.net dramacoin system. What do you do?
A. Report it to the admiggers to get a cool pentester badge.
B. Exploit it relentlessly until the entire dramaeconomy is disrupted.
C. The correct answer is B.
D. All of the above.
Q14: Your step-sister is being a raging b-word to you. What do you do?
A. Do nothing and wait. She's clearly on the rag.
B. Hack her neopets account and kill all her pets or get her banned.
C. Wait for her to get stuck under some furniture.
D. None of the above.
Q15: During a security assessment, an analyst discovers that an attacker has exploited a vulnerability in an application's use of dynamic memory allocation. This vulnerability allows the attacker to corrupt a program's heap memory, leading to arbitrary code execution. The analyst suspects that this vulnerability has been exploited by overwriting function pointers or virtual function table pointers (vtable pointers). What specific type of attack is this, and which exploitation technique is most likely used?
A. Stack Overflow; Return Oriented Programming (ROP)
B. Format String Vulnerability; printf() Function Exploitation
C. Heap Overflow; House of Prime
D. Integer Overflow; Signed vs Unsigned Mismatch
- 49
- 77
De minimus entries from China shut down effective Tuesday.
— Ryan Petersen (@typesfast) February 2, 2025
Maybe American Apparel can come back
- 99
- 96
- 54
- 35
Most Based Comments
Basedness: 🔥🔥🔥🔘🔘
Basedness: 🔥🔥🔥🔘🔘
May he enjoy the rest of his life with his family. (51)
Basedness: 🔥🔥🔘🔘🔘
The deficit got better, stock market recovered, inflation reduced and unemployment fell (15)
Angriest Comments
Angriness: 😡😡😡😡😡
Angriness: 😡😡😡😡😡
Angriness: 😡😡😡😡😡
Biggest Lolcow: /u/jondo81
Score: 🐮🐮🐮🐮🐮(+0🐮)
Number of comments: 8
Average angriness: 🔘🔘🔘🔘🔘
Maximum angriness: 😡😡😡🔘🔘
Minimum angriness: 🔘🔘🔘🔘🔘
NEW: Subscribe to /h/miners to see untapped drama veins, ripe for mining! 
 autodrama: automating away the jobs of dramneurodivergents.
autodrama: automating away the jobs of dramneurodivergents.  Ping HeyMoon if there are any problems or you have a suggestion
Ping HeyMoon if there are any problems or you have a suggestion 
- SnowBoundTape : I win btw
- pm-me-manifestos : I did this thread already: https://rdrama.net/h/random/post/244765/unpopular-opinion-contest
- 351
- 61
Post your least popular opinions as a top level comment in this thread. Whichever opinion is least popular will win 1000 DramaCoin, and have a banner designed for it with a direct attribution to you (so don't say anything you wouldn't want the whole site to know you endorse in perpetuity  ).
).
If you agree with an opinion, upmarsey it. If you disagree with an opinion, downmarsey it. In five hours I will announce the winner.
- 6
- 24
A man working at a cemetery in North Dakota was stopped in his tracks recently by the peculiar sight of three turkeys repeatedly circling a gravestone. pic.twitter.com/avV0HjO3kU
— New York Post (@nypost) February 16, 2025
What did the  mean by this?
mean by this? 
- 7
- 23
I have 2FA on (authenticator based not phone number based), I use a randomly generated password, I've removed all active sessions, but someone keeps changing the password somehow and adding a new phone number. I don't know why either they haven't tried to buy anything.
How tf are they doing it. If it happens again I'm probably just gonna close the account as I barely ever use it.
- Haberdasher : Reddit user has entered thread, wants you to say it to her face.
- 10
- 46
Honestly, if you went back about 2 weeks ago it was quite rare to see posts like this as I mainly saw normie crap and coomer bait as most people did... But that's all changed now... it's a whole new Boomerbook world!
I mean, seriously, why show me the AVAROSA 2024 Esports thing? There's some fishy Chud antics afoot here 

















































 smoked duck breast
smoked duck breast 










 Could someone please saw down this rifle barrel for me?
Could someone please saw down this rifle barrel for me?