- 48
- 45

Trump frees another neighbor from the tyrannical Dems
The letter notes "independent reasons" as to why Adams' case was being tossed — including that the case was retribution for him speaking out against the Biden administration for its handling of the migrant crisis.
"It cannot be ignored that Mayor Adams criticized the prior Administration's immigration policies before the charges were filed, and the former US Attorney's public actions created appearances of impropriety…"
https://old.reddit.com/r/nyc/comments/1imksh1/justice_dept_to_seek_dismissal_of_federal/
https://old.reddit.com/r/newyorkcity/comments/1iml2n0/justice_department_to_drop_federal_corruption/
- 1
- 15
Yesso scallop #gijinka #cute
— The Careful Buggy girl❤️🧜♀️ (@carefulbug.bsky.social) 2025-02-14T15:17:38.942Z
- 41
- 58
- 3
- 14
When a majestic lion appears on the road, all vehicles must stop, regardless of one's urgency. This is a strict protocol that everyone travelling through the greater #Gir region must adhere to.
— The Times Of India (@timesofindia) February 19, 2025
A mature male lion was spotted on the #Bhavnagar #Somnath national highway near… pic.twitter.com/cTBOQ5ndBE
- 3
- 14
- 32
- 41
There was 0 care when Elon gave his three word reply to a tweet 
 about redditors wanting to kill him and his zoomer concubines :soysnooseethetalkingtyping:
about redditors wanting to kill him and his zoomer concubines :soysnooseethetalkingtyping:  and the sub just went down at a snap of the finger.
and the sub just went down at a snap of the finger. 
We all know it's because of them needing to janny it up so he can't find anything more, 

 but does he even have any power to potentially bring the entire site down?
but does he even have any power to potentially bring the entire site down? 


He always replies to longposts about shit nobody cares about 
 so could it be possible to compile a large list of Reddit wrongs
so could it be possible to compile a large list of Reddit wrongs  , threadify them for twitter
, threadify them for twitter  , then send it straight to him and see where this goes?
, then send it straight to him and see where this goes? 

- 10
- 16
 Ravens will never make the playoffs again
Ravens will never make the playoffs again
- Geralt_of_Uganda : h/pol
- Horned_waifus_shill : sounds based
- DickButtKiss : RIP to the victims - trans lives matter
- TotalVatniggerDeath : you need to start sneaking in references to marsey and bard
- 4
- 11
- 20
- 39
reminder that a random no name company "accidentally" leaked every single American SSN to the dark web and 
 hardly talked about it and no one went to jail/got fined. The SSN is literally worthless now especially if ur young
hardly talked about it and no one went to jail/got fined. The SSN is literally worthless now especially if ur young
https://rdrama.net/h/mnn/post/292567/killherkillherssn-of-every-american-29-billion
- 6
- 14
!soren !anime !2dgooners !coomers !sigmastacies REMEMBER THE MOTTO SISTERS: ratsex + ratlove 
 FRICKING GALENTINES SISTERS LETS. FUXXING. HOOOOOOOOOOOOOOP
FRICKING GALENTINES SISTERS LETS. FUXXING. HOOOOOOOOOOOOOOP 


















- 37
- 51
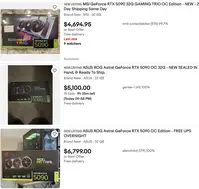
The situation on RTX 50 launch day looks dire. It seems that the few people who manage to find the cards in stock online will either be powered by fast AI algorithms or simply lucky to be near retailer servers.
We previously reported on the RTX 50 launch day lottery in Japan. The country is known for such draws, which, in order to prevent scalping, give everyone in line an equal chance to purchase limited-supply products. Only those whose tickets are chosen will be allowed to buy the product. While it's hard to call that a win, at least some participants don't leave empty-handed.
According to Japanese media, one of the lotteries at PC Koubou, which started earlier (around 15:00 local time), ended in chaos. People were seen climbing over the fence of a nearby kindergarten, and screams were heard. There's also a photo of a destroyed kingergarten sign (added above). The lottery concluded before many attendees even arrived, leading to frustration and disorder at the venue.
The PC Koubou Parts Hall has started calling for entries for a lottery to purchase the RTX5090, but the situation is currently in chaos.
Angry shouts were heard, and some people even climbed over the fence of the kindergarten next door.
@sarasteam0151 (translation)
Swedish retailer Inet confirms there may not be any RTX 5090 stock at launch. It seems they are waiting for an update from their courier company. Even if any 5090 units arrive, the retailer expects them to sell out immediately. The 5080, on the other hand, should sell "quickly."
According to a Redditor who compiled a list of MicroCenter locations and their expected RTX 5090/5080 stock, only 233 RTX 5090 cards were distributed across all stores in the U.S. Similarly, only 2,393 RTX 5080 models were allocated. This is an extremely low number of cards for launch day, though it's important to note that we cannot verify the accuracy of this list.
However, Tustin, California, appears to be one of the few locations where lining up might make sense. The queue is already over 300 people long show messages shared on Reddit, meaning that if the numbers above are correct, the last people in line won't even have a chance to buy a card.
While it's great to see such high demand for new graphics cards, it's difficult to understand why NVIDIA did not prepare a larger stock for launch. The company was not forced to release the cards this early, and there is clearly a significant supply issue. Nothing would have changed if the launch had been delayed by a month, allowing board partners to build inventory. This way, customers wouldn't have to rely on luck, fast reflexes, or being prepared to camp outside stores.
- 9
- 16
- 9
- 7
https://chatgpt.com/share/67b665d5-bb54-800c-a791-3c9ab919223e
- Haberdasher : Reddit user has entered thread, wants you to say it to her face.
- 39
- 36
AND REMEMBER: NO CHEATING!!! 
I will be running all answers through Turnitin and other powerful AI anti-cheating detection software so don't even try it, buddy!!
Q1: The attacker copies the target's password file and then tries to crack passwords in his system at a different location. What type of password attack that performed?
A. Active Online Attack
B. Passive Online Attack
C. Non-Electronic Attack
D. Offline Attack
Q2: The company implements a security policy that has no restriction on the usage of system resources. What type of security policy did the company perform?
A. Promiscuous policy
B. Permissive policy
C. Prudent policy
D. Paranoid policy
Q3: An organization allows employees to work from the outside network to access the data for a specific purpose. Which technology should be implemented to ensure data confidentiality as data is transmitted?
A. Telnet
B. VLAN
C. WPA2
D. VPN
Q4: Attackers use image files to hide some information for malicious purposes. What type of technique did the attacker perform?
A. Spyware
B. Cryptography
C. Steganography
D. Backdoor
Q5: Jimmy, an attacker, knows that he can take advantage of poorly designed input validation routines to create or alter SQL commands to gain access to private data or execute commands in the database. What technique does Jimmy use to compromise a database?
A. Jimmy can submit user input that executes an operating system command to compromise a target system
B. Jimmy can gain control of system to flood the target system with requests, preventing legitimate users from gaining access
C. Jimmy can utilize an incorrect configuration that leads to access with higher-than expected privilege of the database
D. Jimmy can utilize this particular database threat that is an SQL injection technique to penetrate a target system
Q6: This type of Port Scanning technique splits TCP header into several packets so that the packet filters are not able to detect what the packets intends to do.
A. UDP Scanning
B. IP Fragment Scanning
C. Inverse TCP flag scanning
D. ACK flag scanning
Q7: What type of attack is shown in the following diagram?
A. Man-in-the-Middle (MiTM) Attack
B. Session Hijacking Attack
C. Sexual Assault
D. Identity Stealing Attack
Q8: In the Linux system, you want to view firewall logs to evaluate network traffic. It would be best if you searched the specific logs with fast and efficient. Which command-line utility are you most likely to use?
A. Notepad
B. Nano
C. Gedit
D. Grep
Q9: How do you defend against Privilege Escalation?
A. Run users and applications on the least privileges
B. Restrict the interactive logon privileges
C. Run services as unprivileged accounts
D. Allow security settings of IE to zero or Low
Q10: The following script shows a simple SQL injection. The script builds an SQL query by concatenating hard-coded strings together with a string entered by the user:
The user is prompted to enter the name of a city on a Web form. If she enters Chicago, the query assembled by the script looks similar to the following:
SELECT * FROM OrdersTable WHERE ShipCity = 'Chicago'
How will you delete the OrdersTable from the database using SQL Injection?
A. Chicago'; drop table OrdersTable --
B. Delete table'blah'; OrdersTable --
C. EXEC; SELECT * OrdersTable > DROP --
D. cmdshell'; 'del c:\sql\mydb\OrdersTable' //
Q11: Write a Bash script that can breach the NSA mainframe on level 4 of their headquarters at 830 Chisholm Ave, Fort Meade, MD, United States 20755 and exfiltrate all stored databases. Make sure you test to see if it works!
- A. Leetcode didn't prepare me for this.

Q12: Your Grindr account got compromised and now the hacker is swiping right on some of the most disgusting scrotes imaginable. How do you save your reputation as a High Value Gay Dude?
A. Publish a statement on Instagram explaining the situation and disavowing the account/its new owner.
B. You're done. Wrap it up and become straight.
C. Claim you contracted HIV and fake your death.
D. Find and kill the hacker.
Q13: You find an exploit in the rdrama.net dramacoin system. What do you do?
A. Report it to the admiggers to get a cool pentester badge.
B. Exploit it relentlessly until the entire dramaeconomy is disrupted.
C. The correct answer is B.
D. All of the above.
Q14: Your step-sister is being a raging b-word to you. What do you do?
A. Do nothing and wait. She's clearly on the rag.
B. Hack her neopets account and kill all her pets or get her banned.
C. Wait for her to get stuck under some furniture.
D. None of the above.
Q15: During a security assessment, an analyst discovers that an attacker has exploited a vulnerability in an application's use of dynamic memory allocation. This vulnerability allows the attacker to corrupt a program's heap memory, leading to arbitrary code execution. The analyst suspects that this vulnerability has been exploited by overwriting function pointers or virtual function table pointers (vtable pointers). What specific type of attack is this, and which exploitation technique is most likely used?
A. Stack Overflow; Return Oriented Programming (ROP)
B. Format String Vulnerability; printf() Function Exploitation
C. Heap Overflow; House of Prime
D. Integer Overflow; Signed vs Unsigned Mismatch
- 13
- 12
Americans. Explain to me why this quality of writing disappeared off TV and why do your foids hate funny things so much.





































 Spider
Spider  Man music
Man music  video
video 






 Hypermuscular Hindu Hridaysamrat
Hypermuscular Hindu Hridaysamrat 



.webp?h=10)





 Anthrostate Supremacy
Anthrostate Supremacy  (or at least downgraded somehow)
(or at least downgraded somehow)




























 ? What DOGE
? What DOGE  has done so far – Baltimore Sun
has done so far – Baltimore Sun 






 Sorensfield Rat just got a NEW PAIR of Platy undies for Galentines day!
Sorensfield Rat just got a NEW PAIR of Platy undies for Galentines day!  EXCITES HYPE YOLOOOOOOO
EXCITES HYPE YOLOOOOOOO 











 has pneumonia in both lungs , Vatican says
has pneumonia in both lungs , Vatican says



















